漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0146537
漏洞标题:好课网手机端SQL注入漏洞影响所有用户(已获取管理员帐号密码)
相关厂商:好课网
漏洞作者: 三浪兄
提交时间:2015-10-14 10:02
修复时间:2015-10-15 10:03
公开时间:2015-10-15 10:03
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:厂商已经修复
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-10-14: 细节已通知厂商并且等待厂商处理中
2015-10-14: 厂商已经确认,细节仅向厂商公开
2015-10-15: 厂商已经修复漏洞并主动公开,细节向公众公开
简要描述:
裤子任意脱
详细说明:
keyword参数可注入
漏洞证明:
[20:27:12] [INFO] the back-end DBMS is MySQL
web application technology: PHP 5.4.10
back-end DBMS: MySQL 5.0.12
[20:27:12] [INFO] fetching database names
available databases [4]:
[*] class_cn
[*] eol_study2
[*] information_schema
[*] test
[20:27:12] [INFO] fetching tables for database: 'class_cn'
Database: class_cn
[94 tables]
+---------------------------------------+
| ci_sessions |
| class_active |
| class_admin_function |
| class_admin_group |
| class_admin_group_function |
| class_admin_member |
| class_admin_member_function |
| class_app_course_type |
| class_app_feedback |
| class_app_version |
| class_cart |
| class_ccback_section_filename |
| class_cooperation_order |
| class_coupon_list |
| class_coupon_op_log |
| class_coupon_public_code |
| class_coupon_single_code |
| class_coupon_user_list |
| class_course_amount |
| class_course_cc_video_undel |
| class_course_chapter |
| class_course_chapter_section |
| class_course_check |
| class_course_comment |
| class_course_detail |
| class_course_guide_doc |
| class_course_list |
| class_course_note |
| class_course_rate |
| class_course_rate_detail |
| class_course_section |
| class_course_section_check |
| class_course_section_guide_doc |
| class_course_section_multi |
| class_course_section_teacher |
| class_course_type |
| class_course_user_recommend |
| class_email_send |
| class_live_course |
| class_live_course_check |
| class_live_order |
| class_logs_coupon |
| class_logs_course_chapter_section_del |
| class_logs_course_check |
| class_logs_course_delfile |
| class_logs_course_section |
| class_logs_course_section_check_del |
| class_logs_course_section_multi_del |
| class_logs_course_update |
| class_logs_live_callback |
| class_logs_live_course |
| class_logs_live_course_del |
| class_logs_live_message |
| class_logs_order_charge_back |
| class_logs_order_check |
| class_logs_protocal_change |
| class_logs_transcoder |
| class_logs_user_change |
| class_logs_user_check |
| class_message |
| class_message_send |
| class_offline_protocol |
| class_open_uid_map |
| class_order |
| class_order_dezhi |
| class_order_haoxue |
| class_order_log |
| class_order_pay_log |
| class_promote_course |
| class_promote_course_check |
| class_promote_list |
| class_statistic_total |
| class_tag_course |
| class_tag_course_type |
| class_tag_list |
| class_user |
| class_user_comment |
| class_user_comment_viewtimes |
| class_user_favorites_course |
| class_user_msg |
| class_user_num |
| class_user_org_cert |
| class_user_org_cert_check |
| class_user_pay_request |
| class_user_pay_request_check |
| class_user_person_cert |
| class_user_person_cert_check |
| class_user_ratio_set |
| class_user_settle |
| class_user_settle_order |
| class_user_study_course |
| class_user_teacher |
| class_user_weibo |
| class_void_generator |
+---------------------------------------+
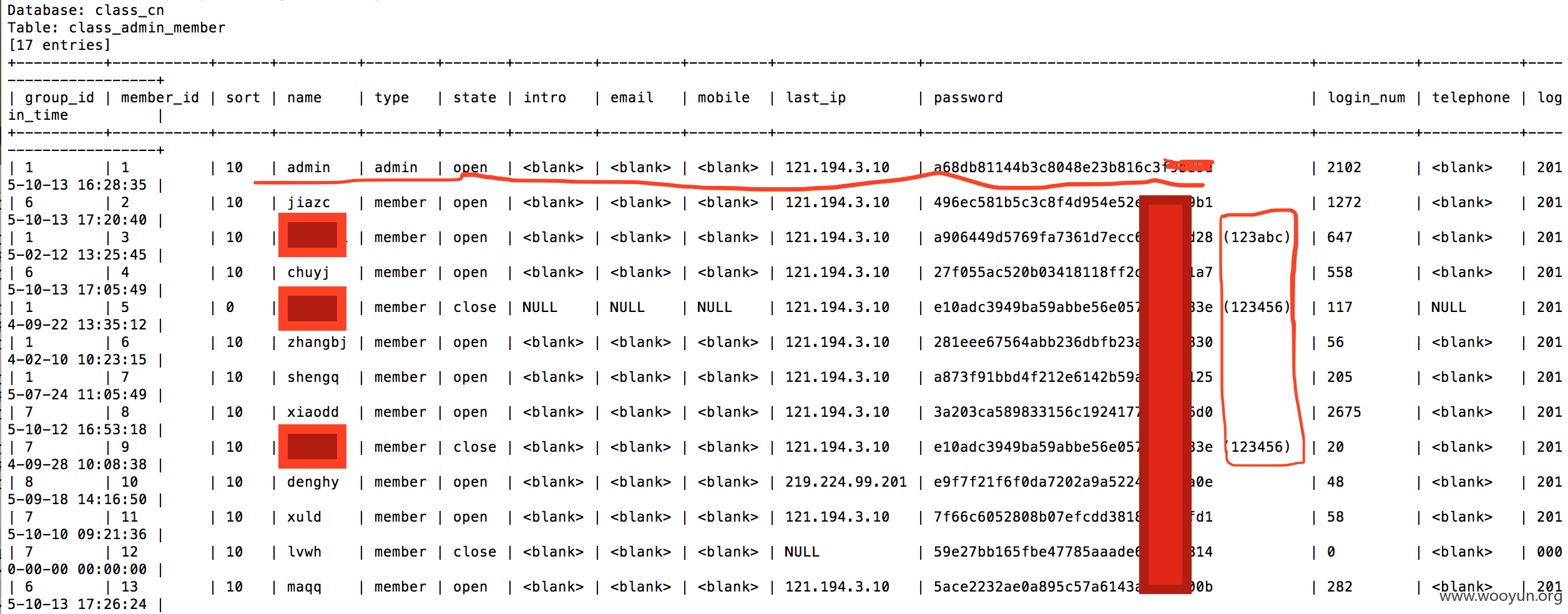
管理员密码以及管理员组的各种弱密码 。。。
截取部分用户:
修复方案:
过滤
版权声明:转载请注明来源 三浪兄@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:20
确认时间:2015-10-14 11:08
厂商回复:
非常感谢。 rank 20
最新状态:
2015-10-15:多谢提交漏洞,我们将全面检查本站安全问题。谢谢。