问题url: **.**.**.**/

咋一看跟标题中的档案人员远程教育平台没有什么关系,好吧我也是后来才知道的。
存在SQL注入:
参数username存在 post型注入
直接上SQLMAP跑一下,结果如下:
可以看到是操作系统为windows,数据库用户名sa ,DBA权限。
测试发现其打开了3389端口
尝试使用os-cmd添加用户wooyun 密码wooyun(测试账号wooyun的密码被我改成了Wooyun@2015,乌云审核人员请注意)
将添加的用户wooyun 添加到administrators组
尝试用wooyun wooyun 登录,运行输入mstsc /admin,远程IP **.**.**.** 发现登陆成功:
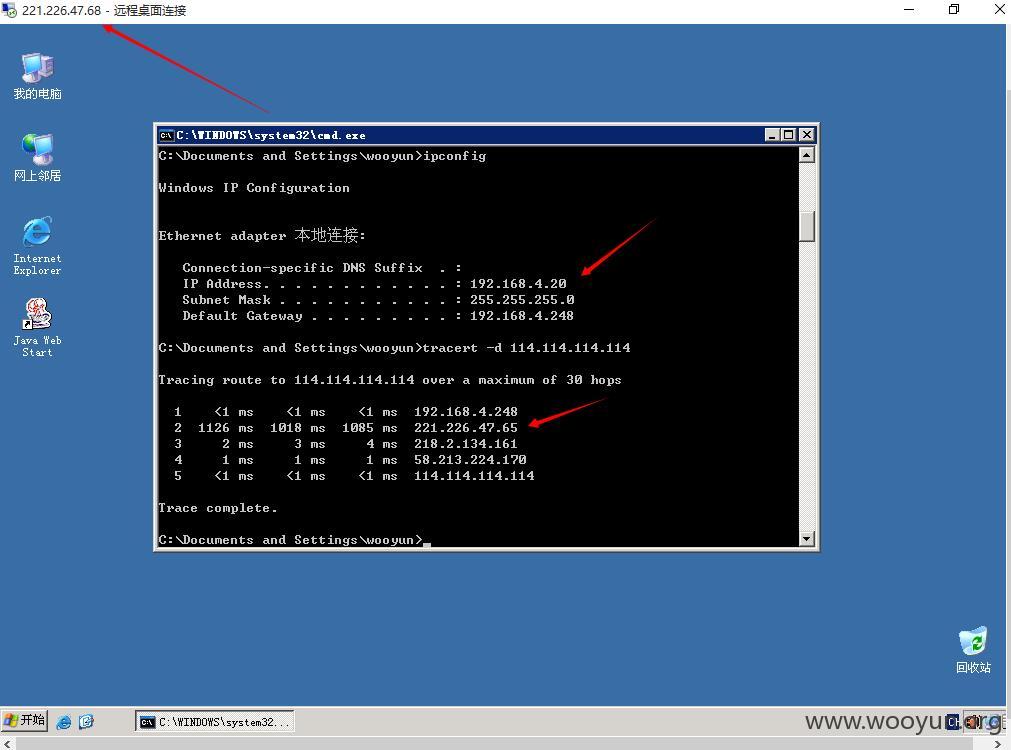
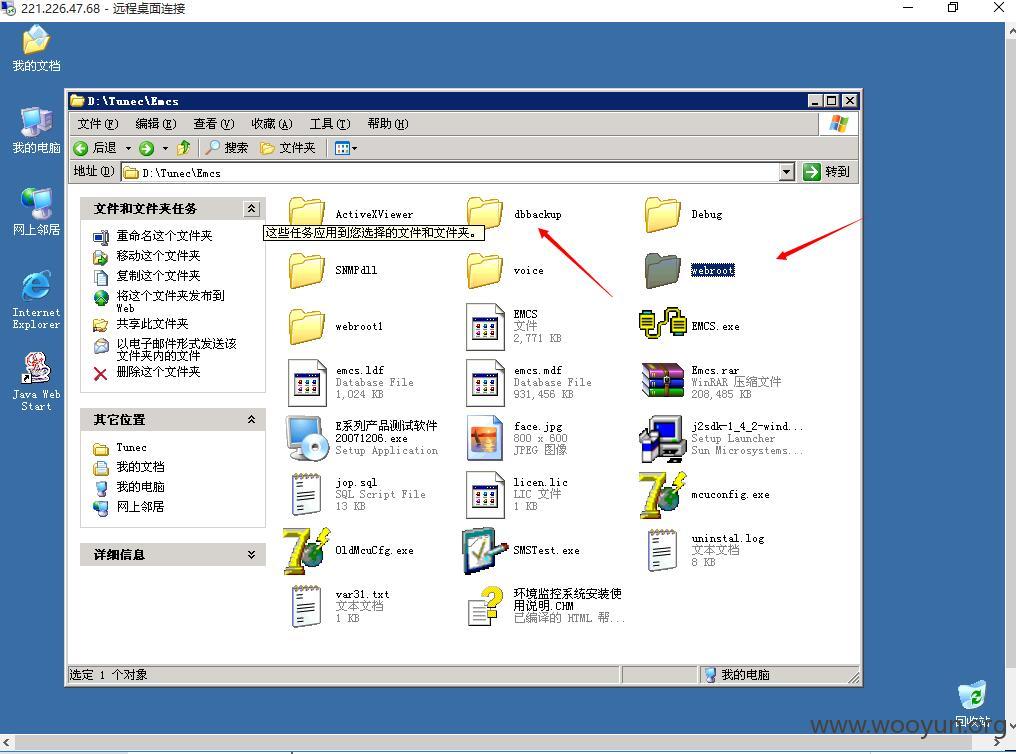
这2张截图可以证明已经内网了把? 私有IP,路由关系,数据库备份、webroot。我们来看看这系统是干嘛用的,开始菜单,程序里见到了外网登录界面所看到的环境监控系统,见下图:
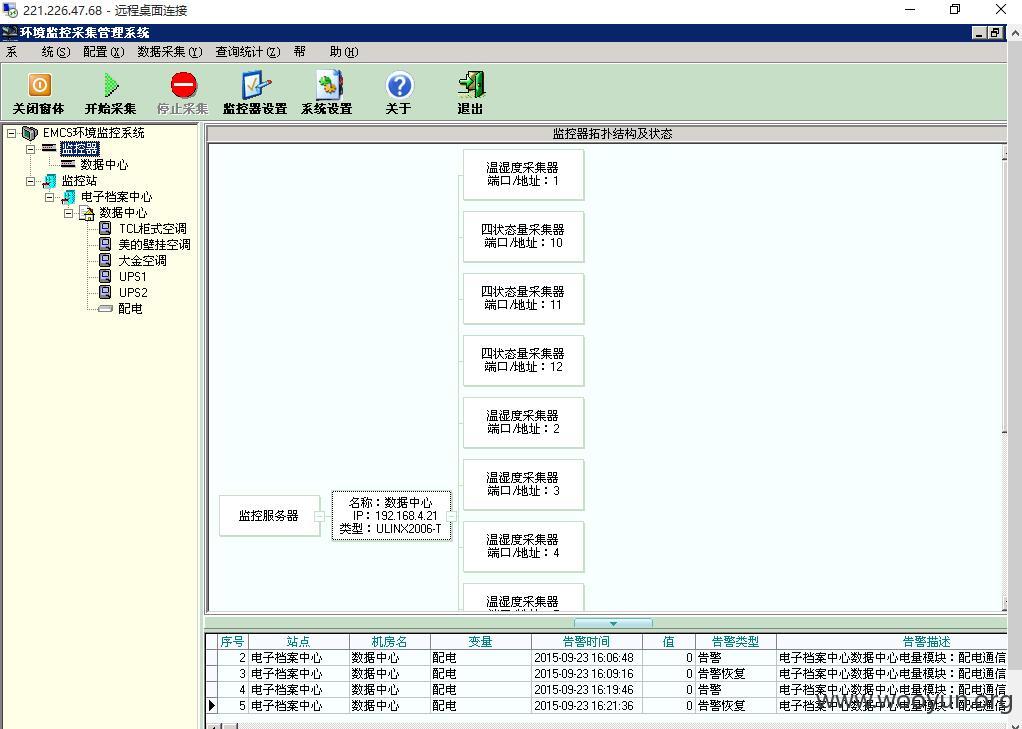
这是他们数据中心机房环境的监控系统。下面我来证明为什么说这是该省档案人员远程教育平台的内网,对内网地址尝试http登录,发现如下:
我们来看看:
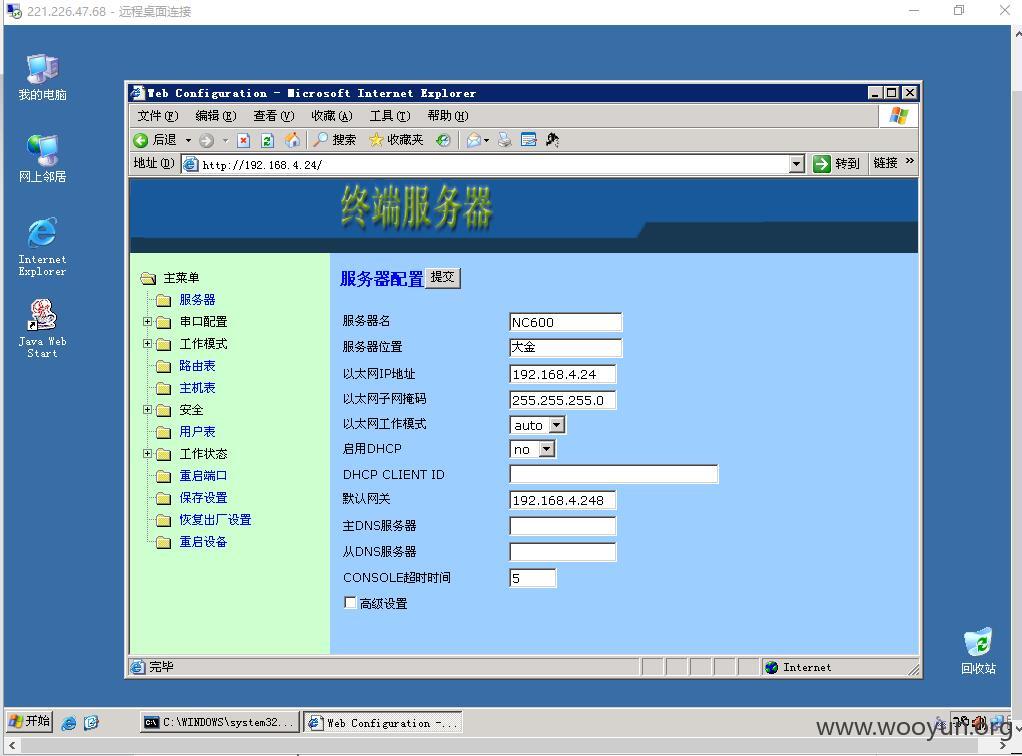
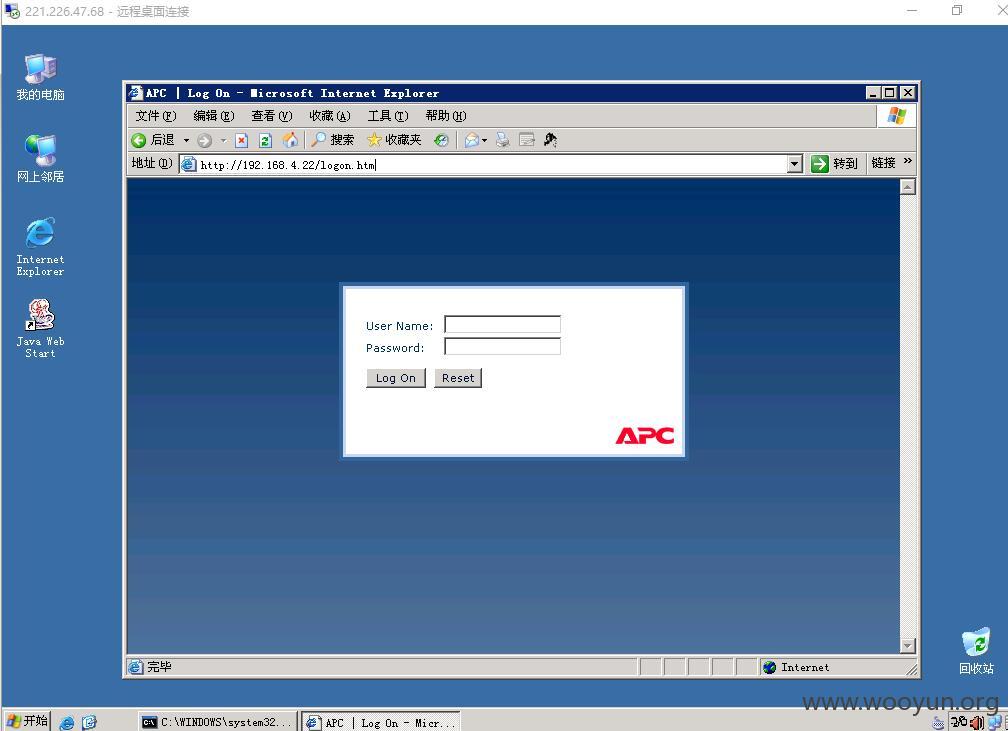
重点来了:
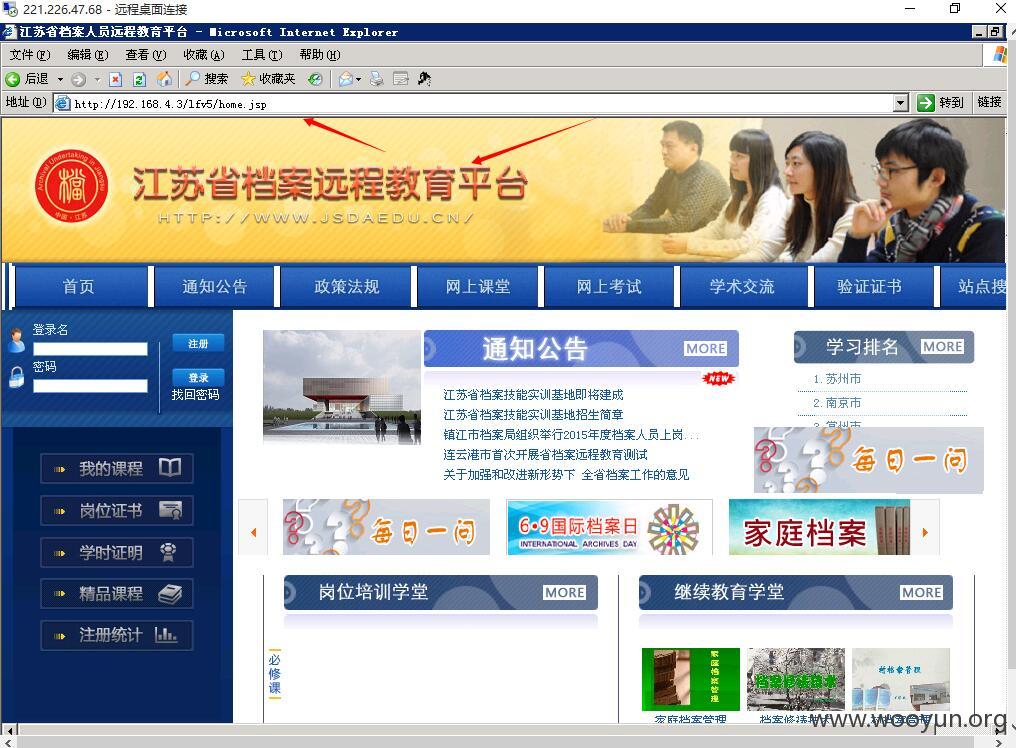
江苏省档案远程教育平台。
度娘查到其互联网地址为:**.**.**.**
nslookup解析一下:
与被远程主机IP相邻,应该可以证明了把。
问题url: **.**.**.**/

咋一看跟标题中的档案人员远程教育平台没有什么关系,好吧我也是后来才知道的。
存在SQL注入:
参数username存在 post型注入
直接上SQLMAP跑一下,结果如下:
可以看到是操作系统为windows,数据库用户名sa ,DBA权限。
测试发现其打开了3389端口
尝试使用os-cmd添加用户wooyun 密码wooyun
将添加的用户wooyun 添加到administrators组
尝试用wooyun wooyun 登录,运行输入mstsc /admin,远程IP **.**.**.** 发现登陆成功:


这2张截图可以证明已经内网了把? 私有IP,路由关系,数据库备份、webroot。我们来看看这系统是干嘛用的,开始菜单,程序里见到了外网登录界面所看到的环境监控系统,见下图:

这是他们数据中心机房环境的监控系统。下面我来证明为什么说这是该省档案人员远程教育平台的内网,对内网地址尝试http登录,发现如下:
我们来看看:


重点来了:

江苏省档案远程教育平台。
度娘查到其互联网地址为:**.**.**.**
nslookup解析一下:
与被远程主机IP相邻,应该可以证明了把。









