漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0130387
漏洞标题:搜狗6000万用户登录邮箱可通过uid遍历
相关厂商:搜狗
漏洞作者: Vinc
提交时间:2015-07-30 10:37
修复时间:2015-09-13 11:00
公开时间:2015-09-13 11:00
漏洞类型:敏感信息泄露
危害等级:中
自评Rank:10
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-07-30: 细节已通知厂商并且等待厂商处理中
2015-07-30: 厂商已经确认,细节仅向厂商公开
2015-08-09: 细节向核心白帽子及相关领域专家公开
2015-08-19: 细节向普通白帽子公开
2015-08-29: 细节向实习白帽子公开
2015-09-13: 细节向公众公开
简要描述:
看到这个http://wooyun.org/bugs/wooyun-2014-077356 想到的
详细说明:
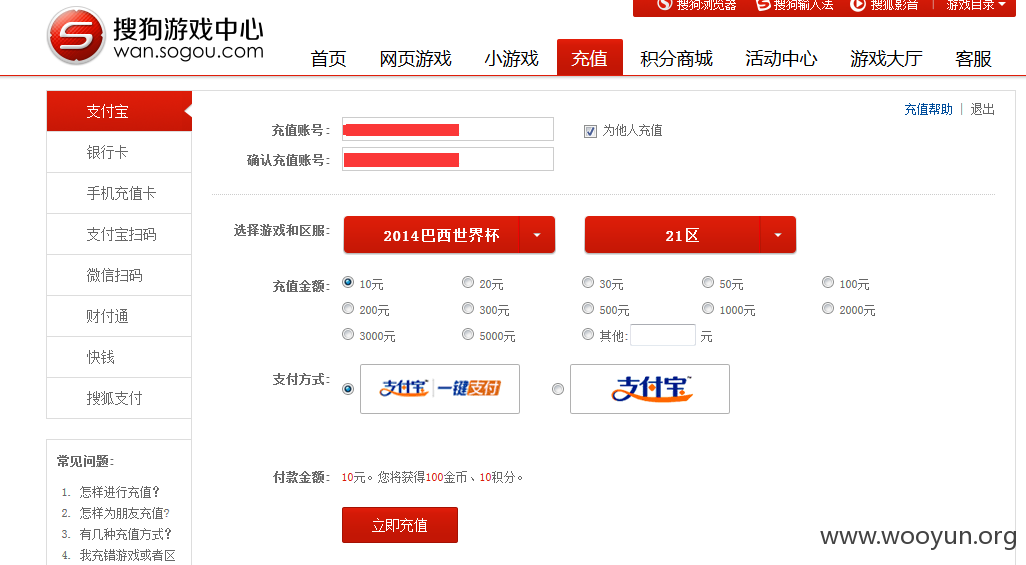
1.sogou游戏中心站点http://wan.sogou.com/p/index.do
2.充值处,可以为他人充值
该处可以通过遍历uid来获取其他用户的邮箱信息,用作暴力破解或者撞裤
通过测试uid,有6000万+用户
POST请求包如下:
附上Py脚本:
漏洞证明:
频率不要太快,跑了100个测试下。
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
香百合[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
修复方案:
版权声明:转载请注明来源 Vinc@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:10
确认时间:2015-07-30 10:58
厂商回复:
感谢支持!
最新状态:
暂无