漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0116193
漏洞标题:某学生兼职网站接口泄露用户敏感信息
相关厂商:北京蓝众时代网络科技有限公司
漏洞作者: lonely-duck
提交时间:2015-06-02 18:00
修复时间:2015-07-17 18:00
公开时间:2015-07-17 18:00
漏洞类型:未授权访问/权限绕过
危害等级:高
自评Rank:18
漏洞状态:未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-06-02: 积极联系厂商并且等待厂商认领中,细节不对外公开
2015-07-17: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
请求用户信息的接口暴露在JS文件中
详细说明:
//查看简历
function getMyResumeURL(userId) {
var pamaArr = [];
pamaArr.push("'AppUserID'" + ":" + "'" + userId + "'");
var str = pamaArr.join(',');
return serviceURL + "{" + getBaseParameterStr('1020') + "," + str + "}" + getRandom();
}
var domain = "http://e.tanlu.cc/";
var appHandler = domain + "AppService/AppRouteHandler.ashx";
var serviceURL = appHandler + "?msg=";
var locationURL = "http://wei.tanlu.cc/IP/Default.aspx";
var imageServerURL = "http://e.tanlu.cc/";
var pageNum = 10;
var version = "1.01";
漏洞证明:
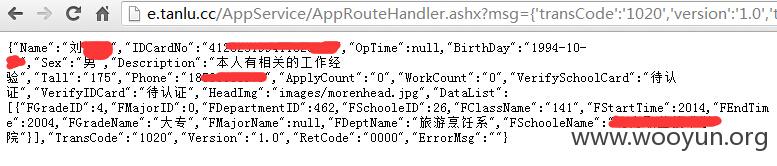
结果太吓人,不敢看(一定要等该网站修复此漏洞后,才能公开!!!!)
{"Name":"孙培波","IDCardNo":"","OpTime":null,"BirthDay":"1994-04-10","Sex":"男","Description":"","Tall":"175","Phone":"18134411120","ApplyCount":"0","WorkCount":"0","VerifySchoolCard":"待认证","VerifyIDCard":"待认证","HeadImg":"images/morenhead.jpg","DataList":[{"FGradeID":4,"FMajorID":0,"FDepartmentID":0,"FSchooleID":26,"FClassName":"","FStartTime":2013,"FEndTime":2004,"FGradeName":"大专","FMajorName":null,"FDeptName":null,"FSchooleName":"河南职业技术学院"}],"TransCode":"1020","Version":"1.0","RetCode":"0000","ErrorMsg":""}
修复方案:
版权声明:转载请注明来源 lonely-duck@乌云
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝