漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0113364
漏洞标题:同花顺某接口撞库泄露用户登录凭据(有批量账号证明)
相关厂商:同花顺
漏洞作者: 路人甲
提交时间:2015-05-11 10:26
修复时间:2015-05-16 10:28
公开时间:2015-05-16 10:28
漏洞类型:设计缺陷/逻辑错误
危害等级:高
自评Rank:18
漏洞状态:漏洞已经通知厂商但是厂商忽略漏洞
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-05-11: 细节已通知厂商并且等待厂商处理中
2015-05-16: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
撞库扫号攻击已经是Top 10 Security Risks for 2014之一.撞库泄露用户隐私
详细说明:
求审核下5号的漏洞~~~
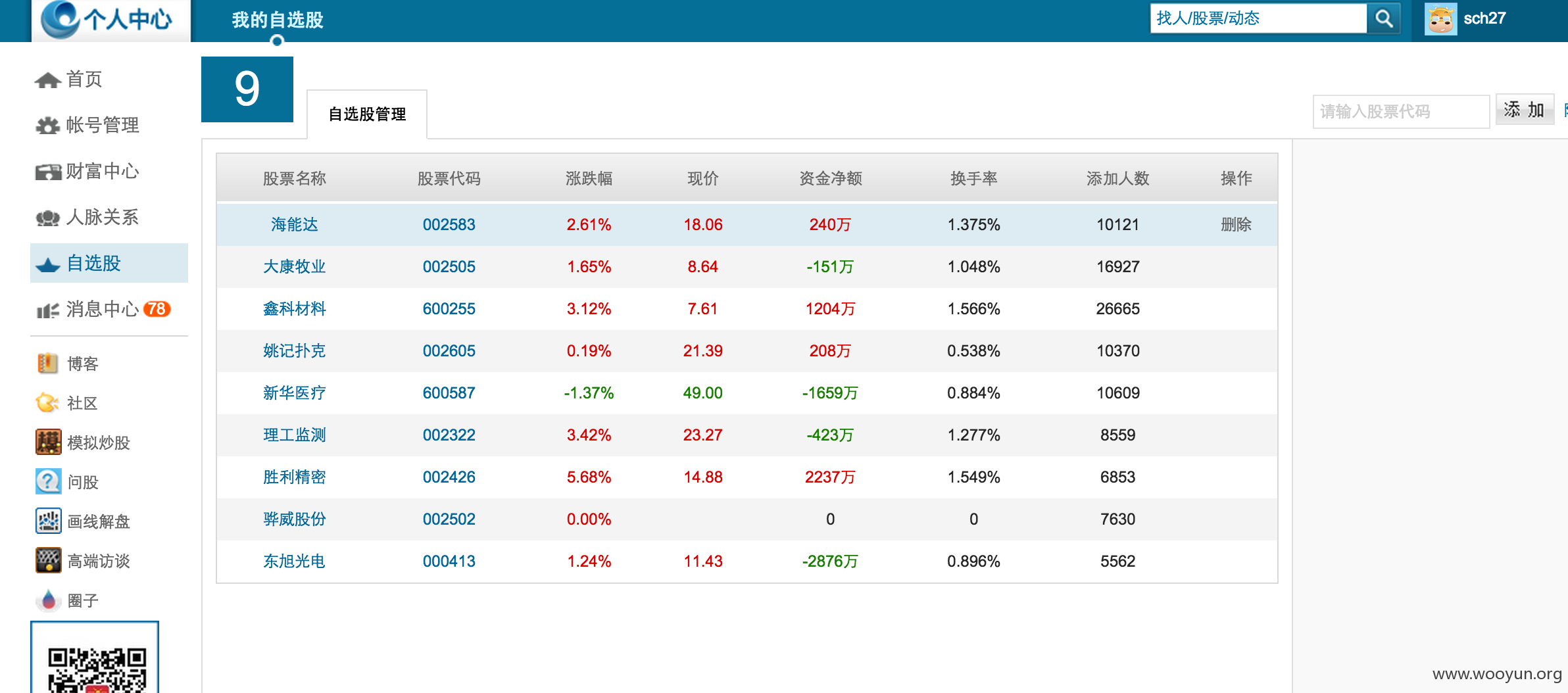
主站登陆登录接口没有防御撞库。对登录接口的调用没有进行限制。经过测试发现,使用某泄露数据库可以碰撞获得大量有效的登录账号。 登录接口抓包如下:
漏洞证明:
修复方案:
撞库防御参考资料:http://stayliv3.github.io/2015/04/15/%E6%92%9E%E5%BA%93%E6%94%BB%E5%87%BB%E9%98%B2%E5%BE%A1%E6%96%B9%E6%A1%88/
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:无影响厂商忽略
忽略时间:2015-05-16 10:28
厂商回复:
漏洞Rank:4 (WooYun评价)
最新状态:
暂无