漏洞概要
关注数(24)
关注此漏洞
漏洞标题:乐看运维配置不当导致账号信息泄漏
提交时间:2013-10-30 12:24
修复时间:2013-12-14 12:24
公开时间:2013-12-14 12:24
漏洞类型:系统/服务运维配置不当
危害等级:中
自评Rank:5
漏洞状态:厂商已经确认
Tags标签:
无
漏洞详情
披露状态:
2013-10-30: 细节已通知厂商并且等待厂商处理中
2013-10-30: 厂商已经确认,细节仅向厂商公开
2013-11-09: 细节向核心白帽子及相关领域专家公开
2013-11-19: 细节向普通白帽子公开
2013-11-29: 细节向实习白帽子公开
2013-12-14: 细节向公众公开
简要描述:
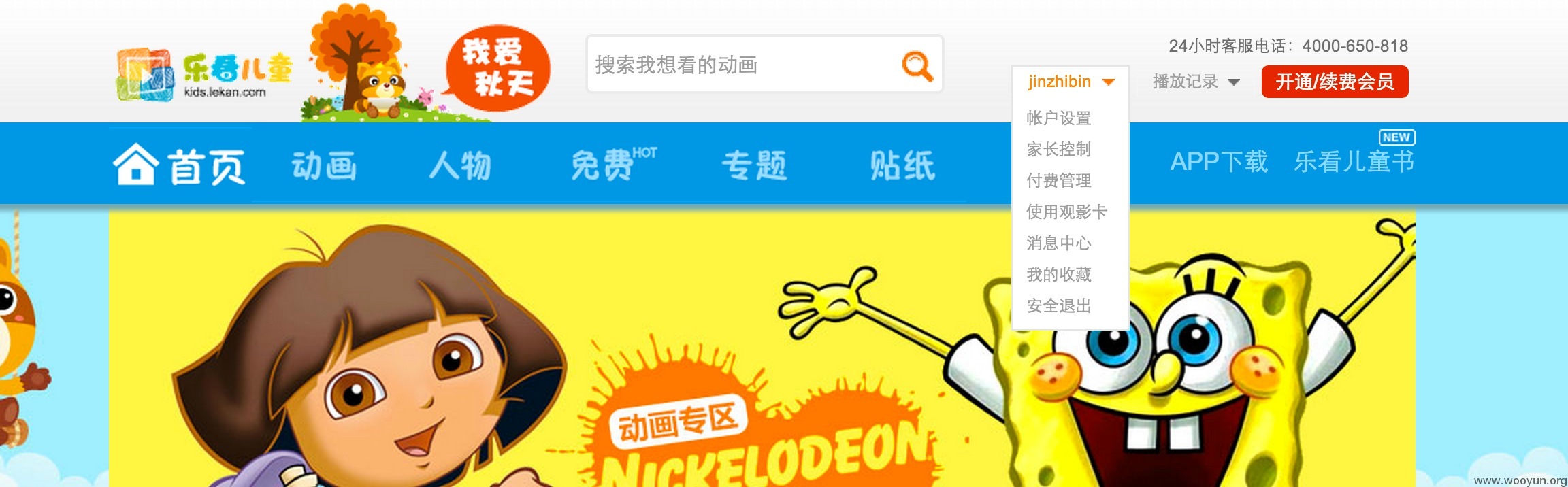
乐看rsync配置不当,导致用户登陆信息日志外泄,可导致用户名和密码泄漏。
详细说明:
漏洞证明:
修复方案:
版权声明:转载请注明来源 盈盈无绪@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:7
确认时间:2013-10-30 13:40
厂商回复:
rsync 配置因为临时原因去掉安全限制,没有及时改回;登录需要改为 POST 方式
最新状态:
暂无