漏洞概要
关注数(24)
关注此漏洞
漏洞标题:电信DNS劫持跳转的站点存在Struts2远程命令执行漏洞
提交时间:2013-09-08 20:27
修复时间:2013-10-23 20:28
公开时间:2013-10-23 20:28
漏洞类型:系统/服务补丁不及时
危害等级:中
自评Rank:7
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
Tags标签:
无
漏洞详情
披露状态:
2013-09-08: 细节已通知厂商并且等待厂商处理中
2013-09-12: 厂商已经确认,细节仅向厂商公开
2013-09-22: 细节向核心白帽子及相关领域专家公开
2013-10-02: 细节向普通白帽子公开
2013-10-12: 细节向实习白帽子公开
2013-10-23: 细节向公众公开
简要描述:
哈哈哈电信喜欢劫持到114so.cn啊哈哈哈哈哈哈哈哈哈哈[拜拜]
详细说明:
root权限
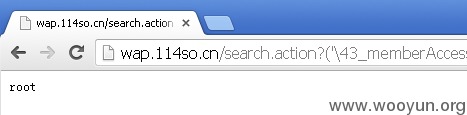
![$4TT[`@T0BMR[N)`59D[]_4.jpg](http://wimg.zone.ci/upload/201309/081938169b708a5734adf4e1d10f28d7da8e9d47.jpg)
漏洞证明:
ifconfig
ls -l
修复方案:
版权声明:转载请注明来源 超威蓝猫@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:8
确认时间:2013-09-12 23:33
厂商回复:
最新状态:
暂无




![$4TT[`@T0BMR[N)`59D[]_4.jpg](http://wimg.zone.ci/upload/201309/081938169b708a5734adf4e1d10f28d7da8e9d47.jpg)