漏洞概要
关注数(24)
关注此漏洞
漏洞标题:移淘网SQL注入漏洞
提交时间:2012-11-08 11:32
修复时间:2012-12-23 11:33
公开时间:2012-12-23 11:33
漏洞类型:SQL注射漏洞
危害等级:低
自评Rank:15
漏洞状态:未联系到厂商或者厂商积极忽略
Tags标签:
无
漏洞详情
披露状态:
2012-11-08: 积极联系厂商并且等待厂商认领中,细节不对外公开
2012-12-23: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
移淘商城sql注入
详细说明:
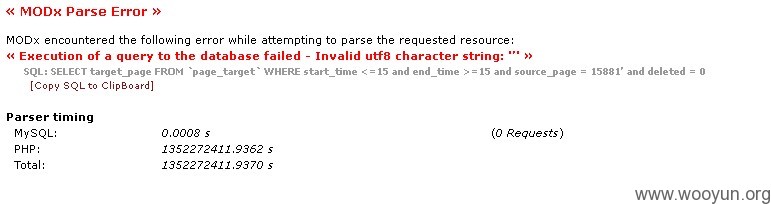
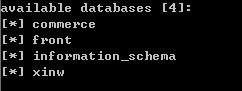
http://ytaow.cn/index.php?id=15881%A1%AF&from_id=40951没有做任何sql过滤导致sql注入漏洞,电商的安全性应该要求更高些吧。
漏洞证明:
修复方案:
漏洞回应




