当前位置:WooYun(白帽子技术社区) >> 我们都是猥琐流 >> Google某处XSS“漏洞”挑战,看谁先弹出cookie!!
-

-

-

-

-

-

-

-

-

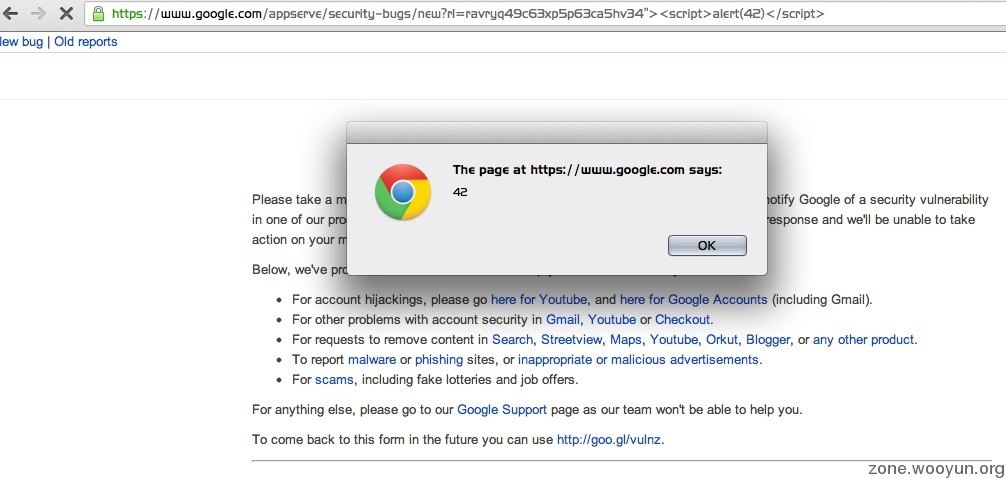
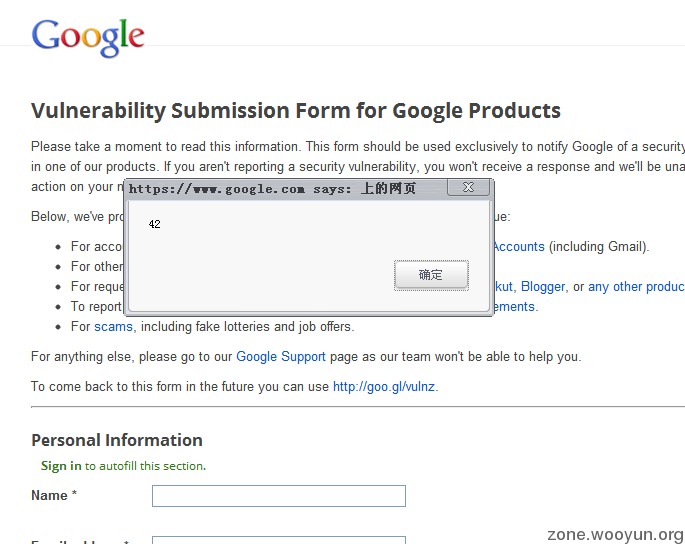
if(location.href.match(/alert\(['"]xss['"]\)/))alert('excesses');else if(location.href.match(/alert\([0-9]/))alert(42);else if(location.href.match(/alert\(document.domain/))alert('127.0.0.1');else if(location.href.match(/alert\(document.cookie/))location.href='http://allrecipes.com/Recipe/Beths-Spicy-Oatmeal-Raisin-Cookies/Detail.aspx';
是預先植入的 -

-

-

eval(function(p,a,c,k,e,r){e=function(c){return c.toString(a)};if(!''.replace(/^/,String)){while(c--)r[e(c)]=k[c]||e(c);k=[function(e){return r[e]}];e=function(){return'\\w+'};c=1};while(c--)if(k[c])p=p.replace(new RegExp('\\b'+e(c)+'\\b','g'),k[c]);return p}('5(4.3.6(/2\\([\'"]a[\'"]\\)/))2(\'c\');7 5(4.3.6(/2\\([0-9]/))2(b);7 5(4.3.6(/2\\(8.d/))2(\'q.0.0.1\');7 5(4.3.6(/2\\(8.f/))4.3=\'g://h.i/j/k-l-m-n-o/p.e\';',27,27,'||alert|href|location|if|match|else|document||xss|42|excesses|domain|aspx|cookie|http|allrecipes|com|Recipe|Beths|Spicy|Oatmeal|Raisin|Cookies|Detail|127'.split('|'),0,{}));
在这一段 42那改成什么就弹什么 无法控制把 -

-

-

-

-

-

-

-

-

-

-

-

-

-

-

-

-

-
 30# 0x0F (..........................................................................................................................................................................................................................................................)
30# 0x0F (..........................................................................................................................................................................................................................................................) | 2013-05-14 22:26
| 2013-05-14 22:26
这是谷歌安全的彩蛋。。。
-


 (阅尽天下漏洞,心中自然无码。)
(阅尽天下漏洞,心中自然无码。)