下载APP 鱼泡泡 的APP, 反馈建议输入xss
然后坐等cookie
等到俩,不过cookie都过期进不去
通过一系列摸排之后
得知第一个是 运营管理系统
第二个是 客服管理系统
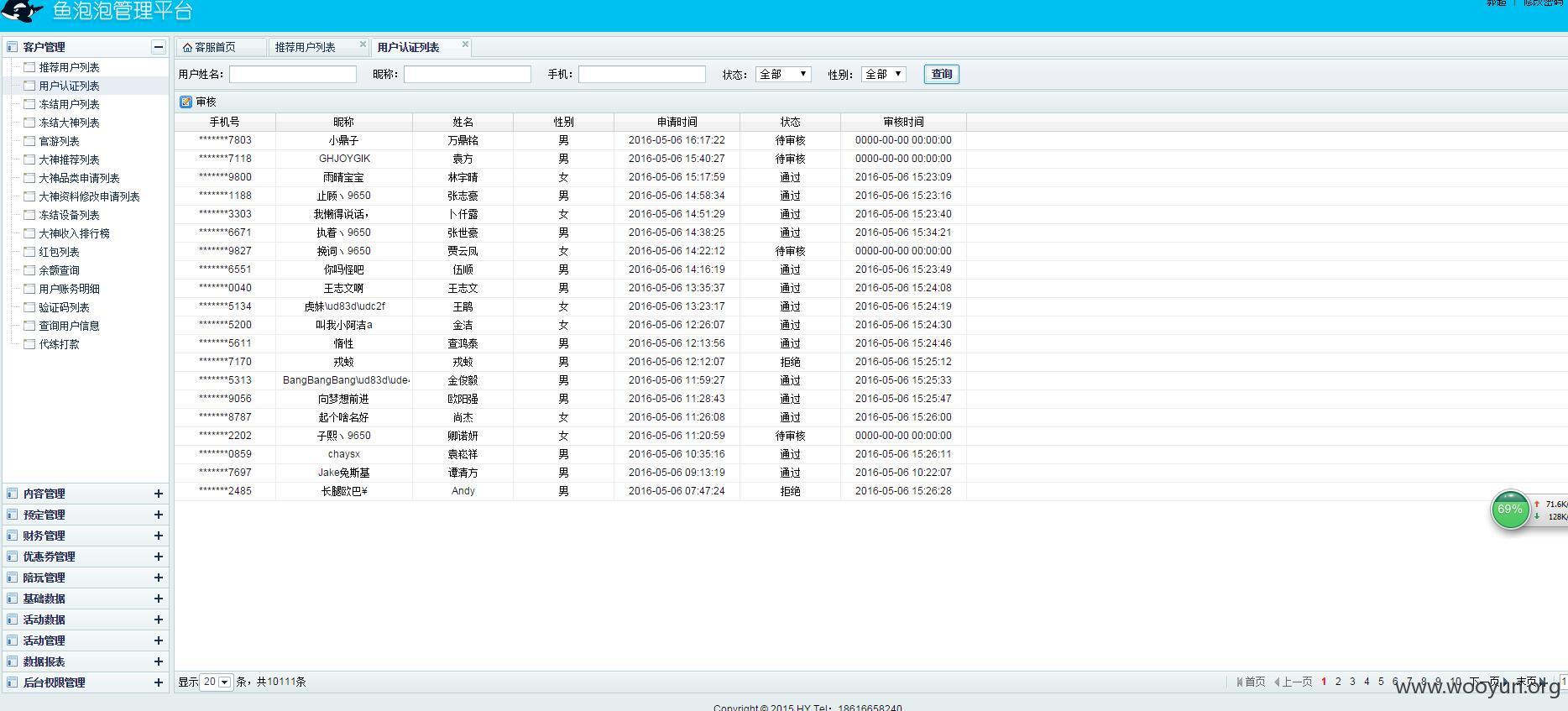
通过爆破客服管理系统
chenyan
liuna
zhanglin
zhangyong
guochao
liyongsheng
得知存在6位大侠的账户
然后果断用户名撞用户名
得到
guochao/guochao
liyongsheng/liyongsheng
俩弱口令
杀入进去
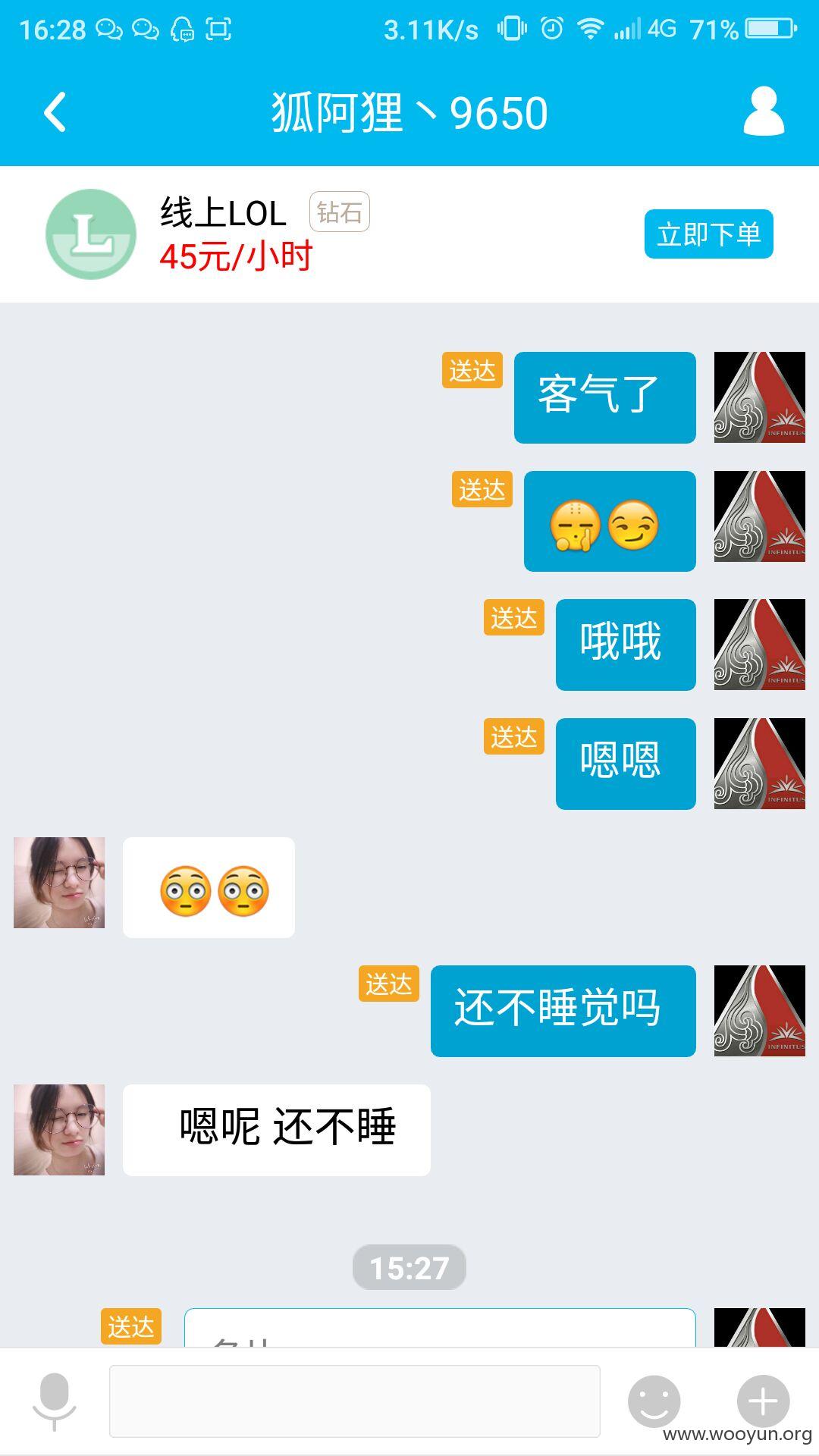
昨晚跟妹纸聊天
我还以为是机器人呢,居然不是- -
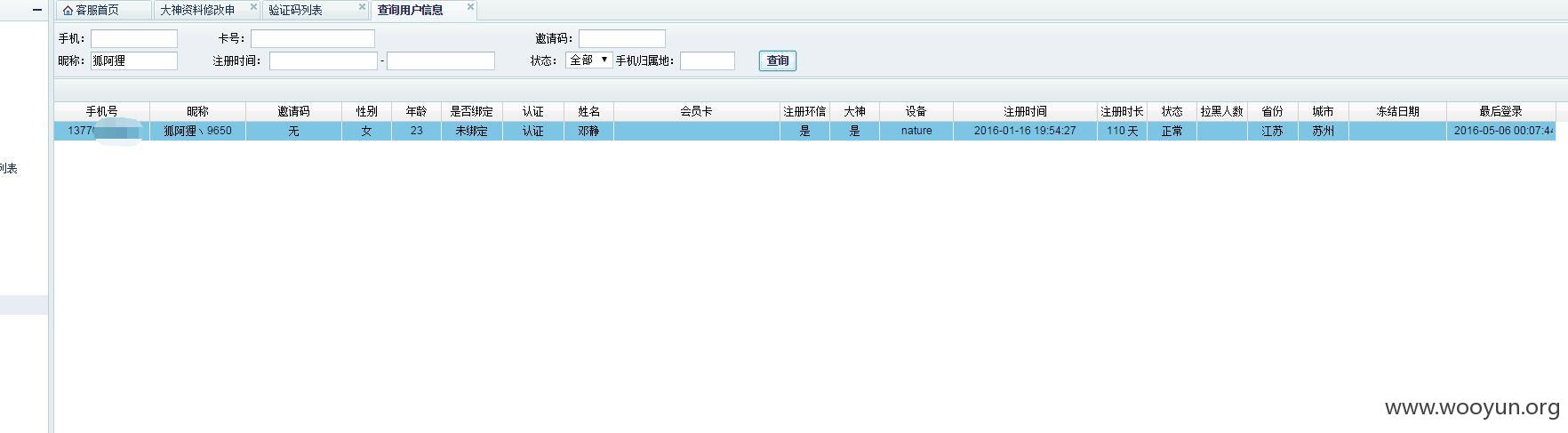
妹纸手机号码到手。(*^__^*) 嘻嘻……
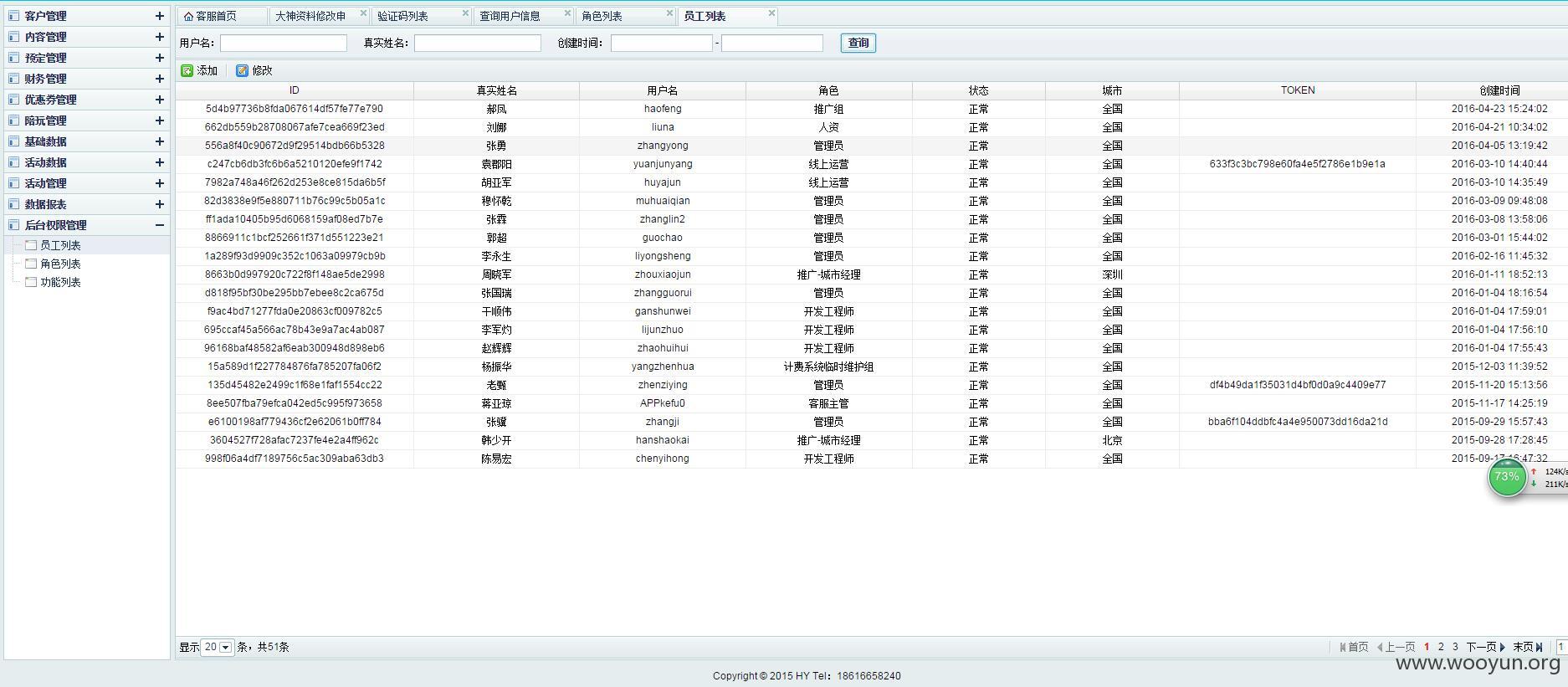
猜测还有大量弱口令
第2个系统
同样账号密码通用
http://yunying.yupaopao.cn/home/nim
进主系统看看
发现
看看http://doc.yupaopao.cn
丢~
没权限
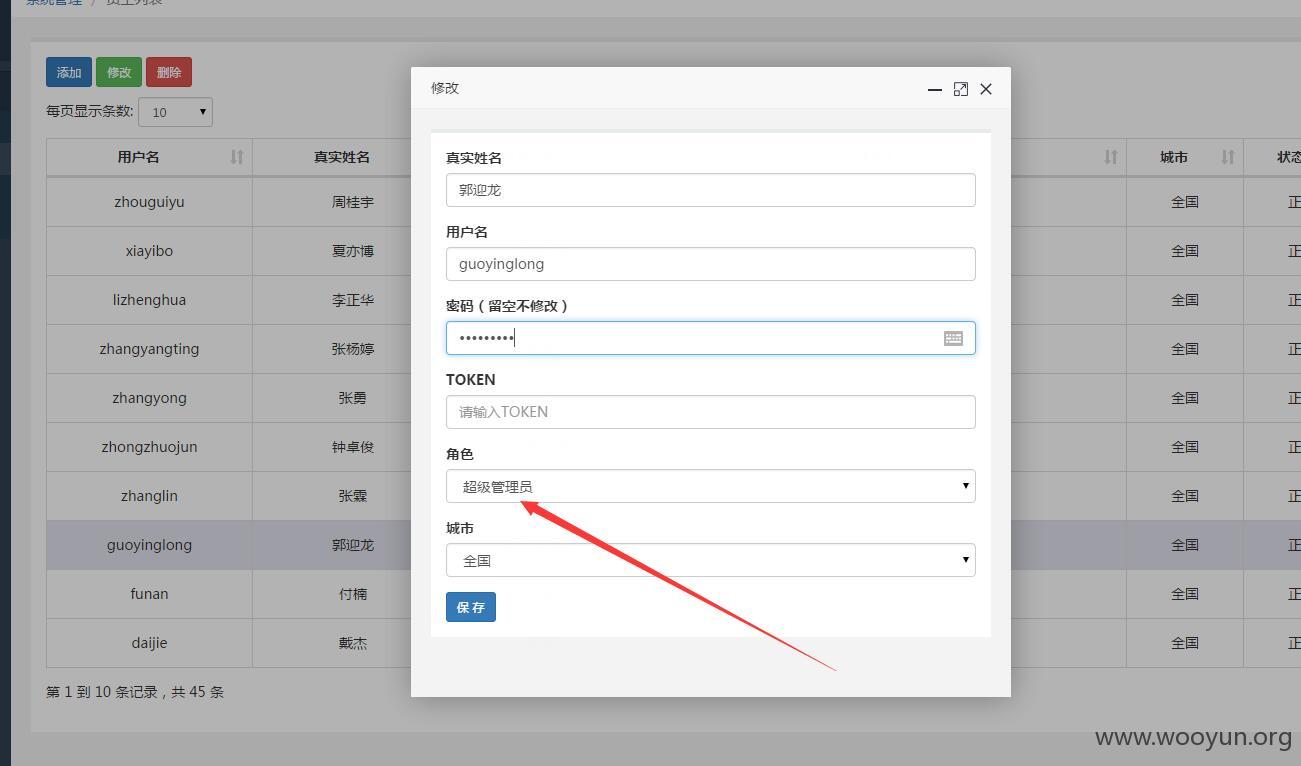
最后将超级管理员guoyinglong的密码改成189837992了
再试试权限多大
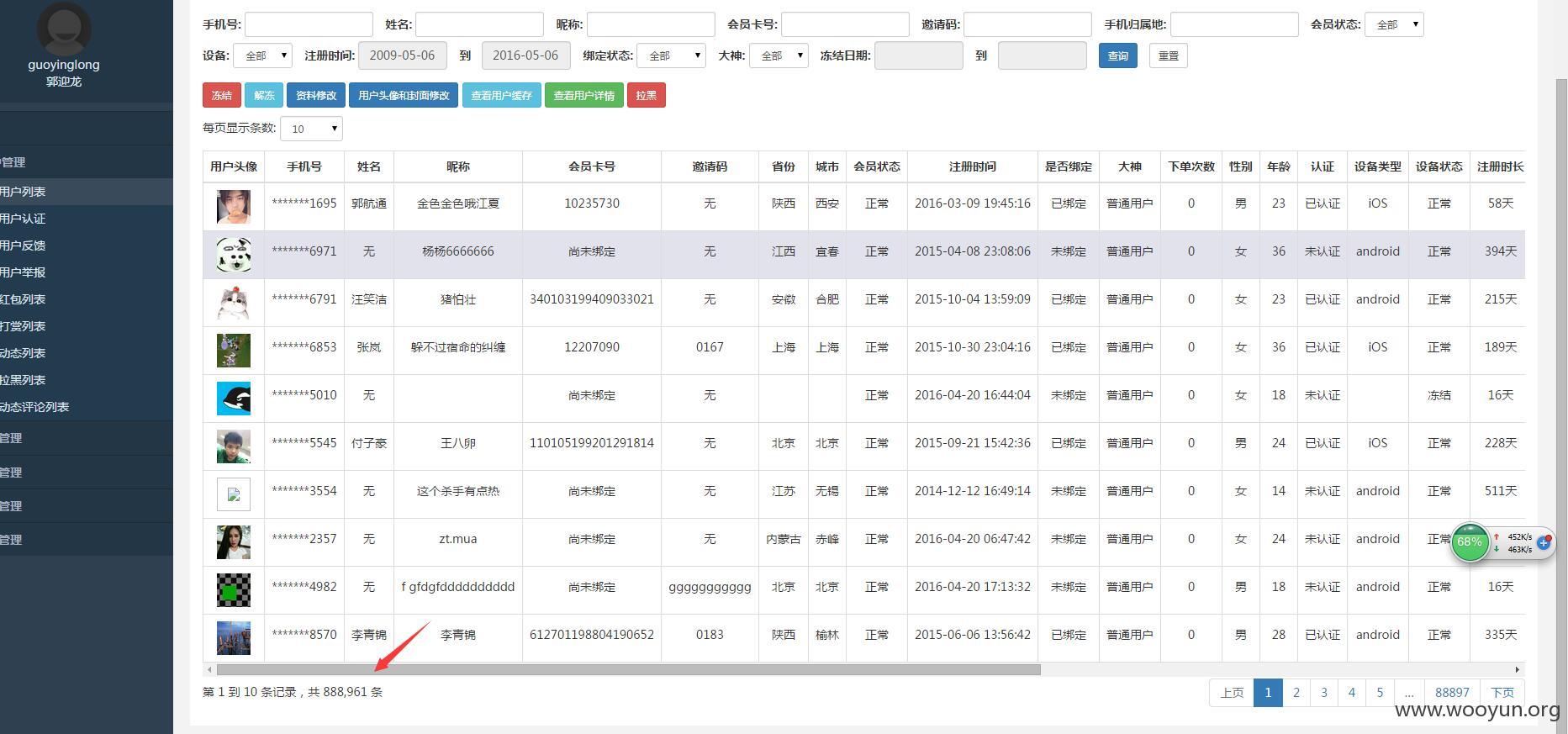
80万用户
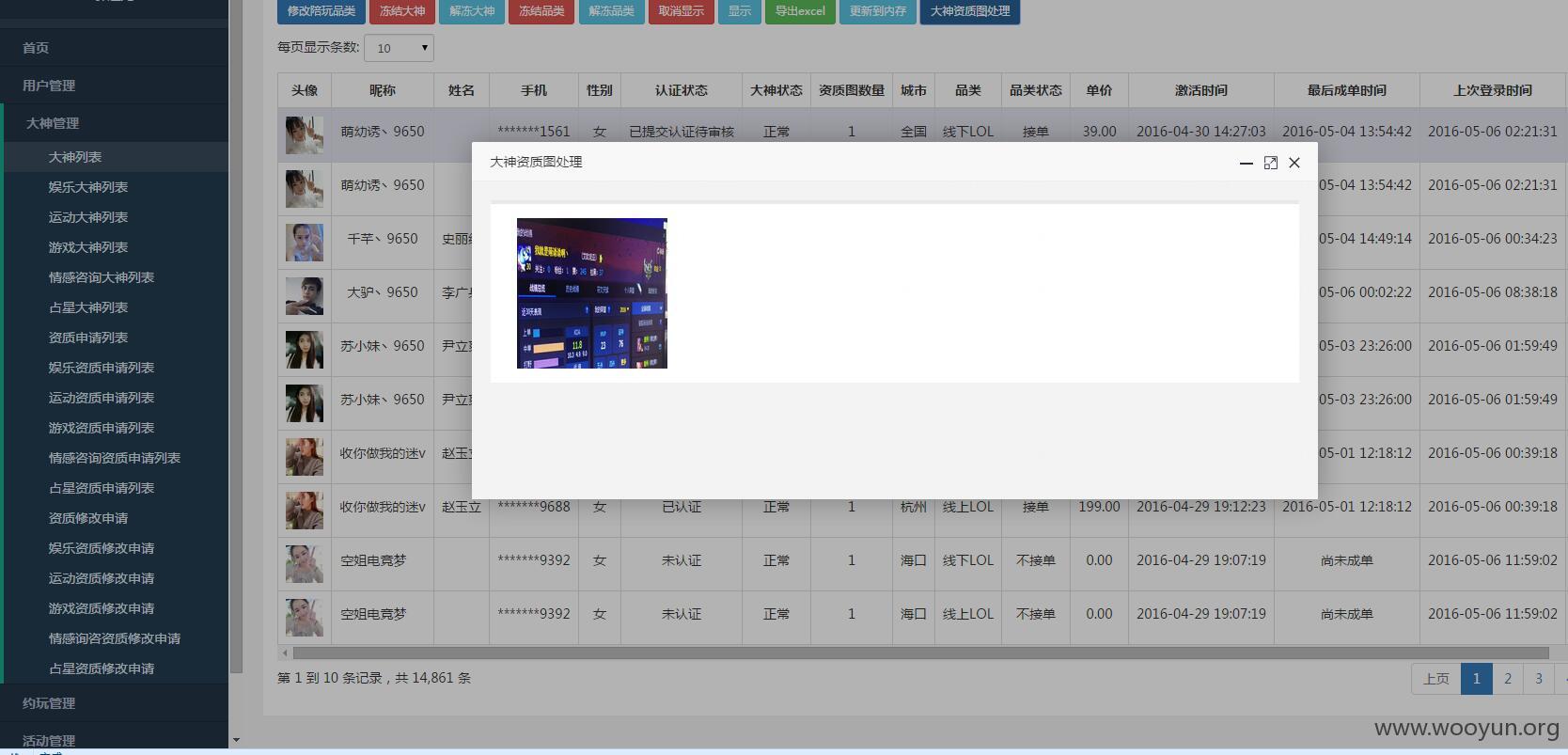
太牛逼了。 检测完赶快撤。
ps:程序员在做着后台的时候保证是没脾气的。。。