漏洞概要
关注数(24)
关注此漏洞
漏洞标题:中国银行某系统存在弱口令可上传SHELL (穿透边界防火墙进入内网)
提交时间:2016-05-01 14:44
修复时间:2016-06-18 21:00
公开时间:2016-06-18 21:00
漏洞类型:未授权访问/权限绕过
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
Tags标签:
无
漏洞详情
披露状态:
2016-05-01: 细节已通知厂商并且等待厂商处理中
2016-05-04: 厂商已经确认,细节仅向厂商公开
2016-05-14: 细节向核心白帽子及相关领域专家公开
2016-05-24: 细节向普通白帽子公开
2016-06-03: 细节向实习白帽子公开
2016-06-18: 细节向公众公开
简要描述:
中国银行某系统存在弱口令可上传SHELL (穿透边界防火墙进入内网)
详细说明:
#1 发现方法
利用通用的弱口令检测脚本,简单而又高效且杀伤力巨大
http://zone.wooyun.org/content/22529
http://zone.wooyun.org/content/21962
中国姓名排行TOP500(数据统计来自国家人口数据库)
http://zone.wooyun.org/content/18372
#2 漏洞描述
https://e.boc.cn/ehome/property/frame/sign.do
发现1个弱口令:wangwei:000000
社区管理功能,添加附件,即可获得shell
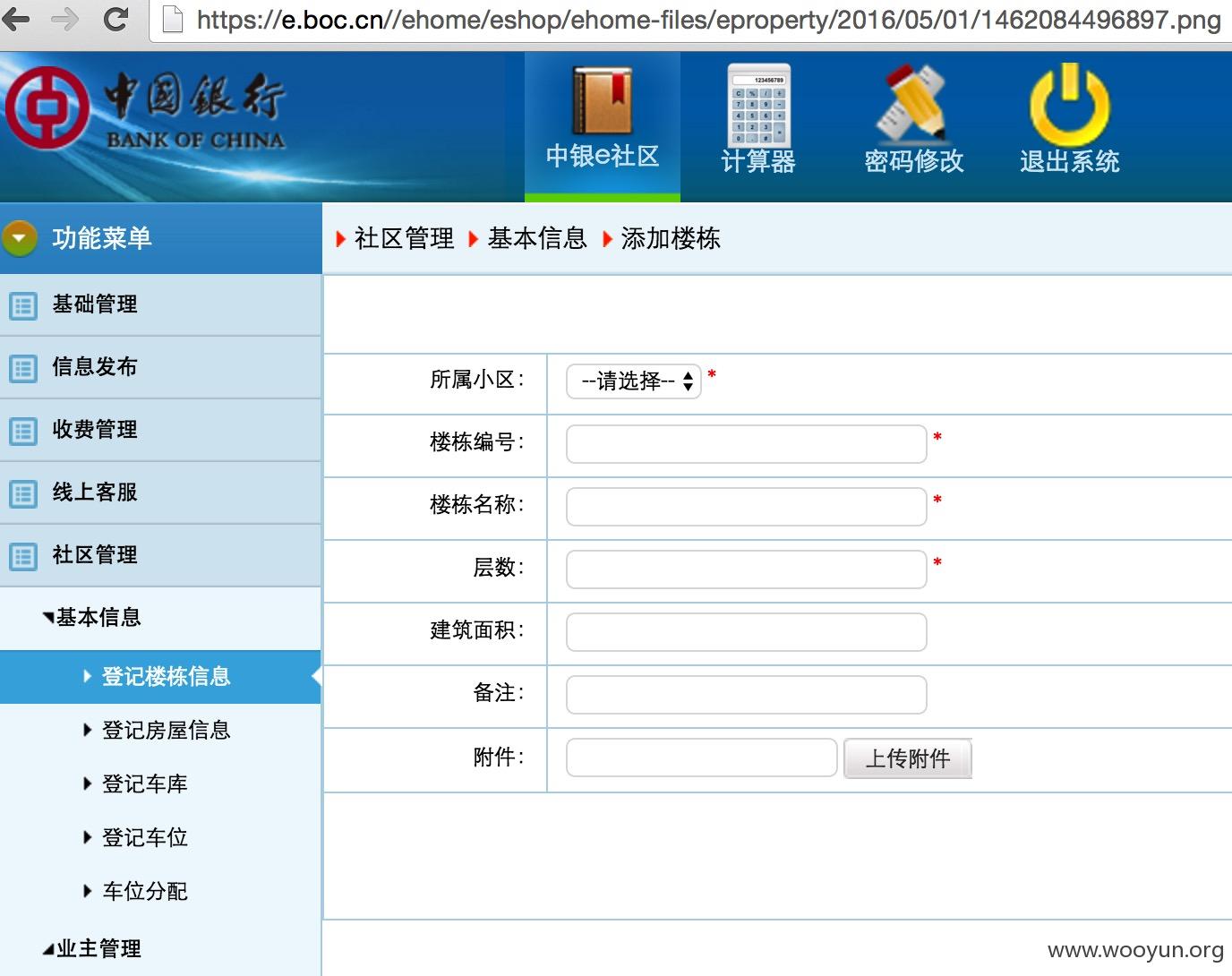
漏洞证明:
https://e.boc.cn/ehome/eshop/ehome-files/eproperty/2016/05/01/Customize14*********.jsp
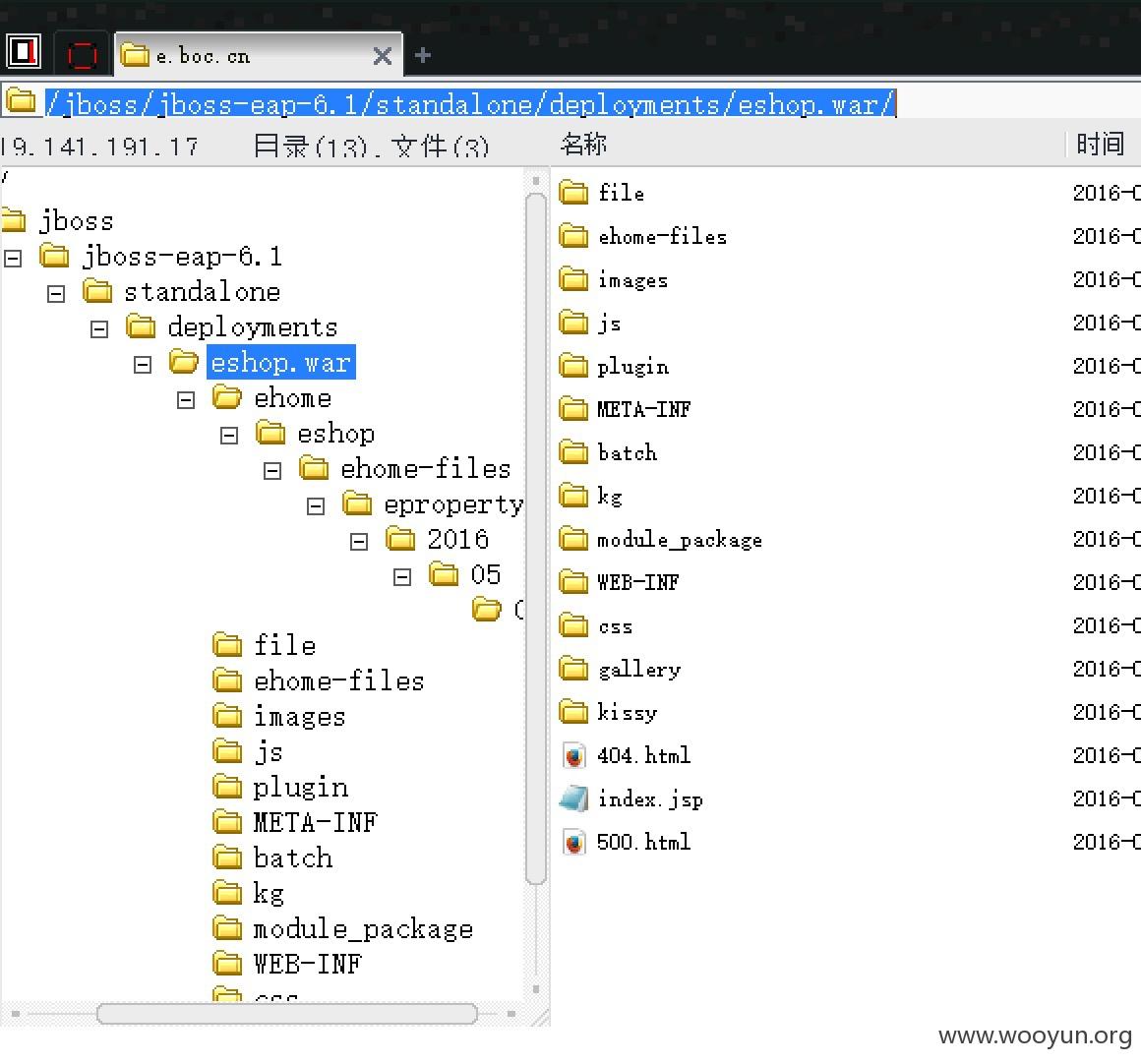
修复方案:
版权声明:转载请注明来源 猪猪侠@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:10
确认时间:2016-05-04 20:50
厂商回复:
感谢白帽子
最新状态:
暂无




