先从第一个注入说起~
http://pay.mojing.cn:80/api/getvideo.php?version=3.00.1221.2211
注入参数version
然后注入users
拿到一个zhaochao的账户~但是不知道后台 pay和mpay域名的后台都打不开~没办法继续看看~
对所有域名进行目录爆破发现mj域名可以打开admin
就尝试使用zhaochao账户 成功登陆
然后就想是不是这个后台会存有注入呢~ 尝试搜索
发现http://mj.mojing.cn:80/admin/score/list?status=&uid=1&nickname=1&content=1&begin_score=1&end_score=4&res_type=&res_id=1&res_name=1&begin_create_time=2016-03-30+13%3A56%3A05&end_create_time=2016-04-23+13%3A56%3A07&excel=0
参数 res_id存在问题(其他的没测试)
mojing是这个后台的数据库
注入出root用户登录试试
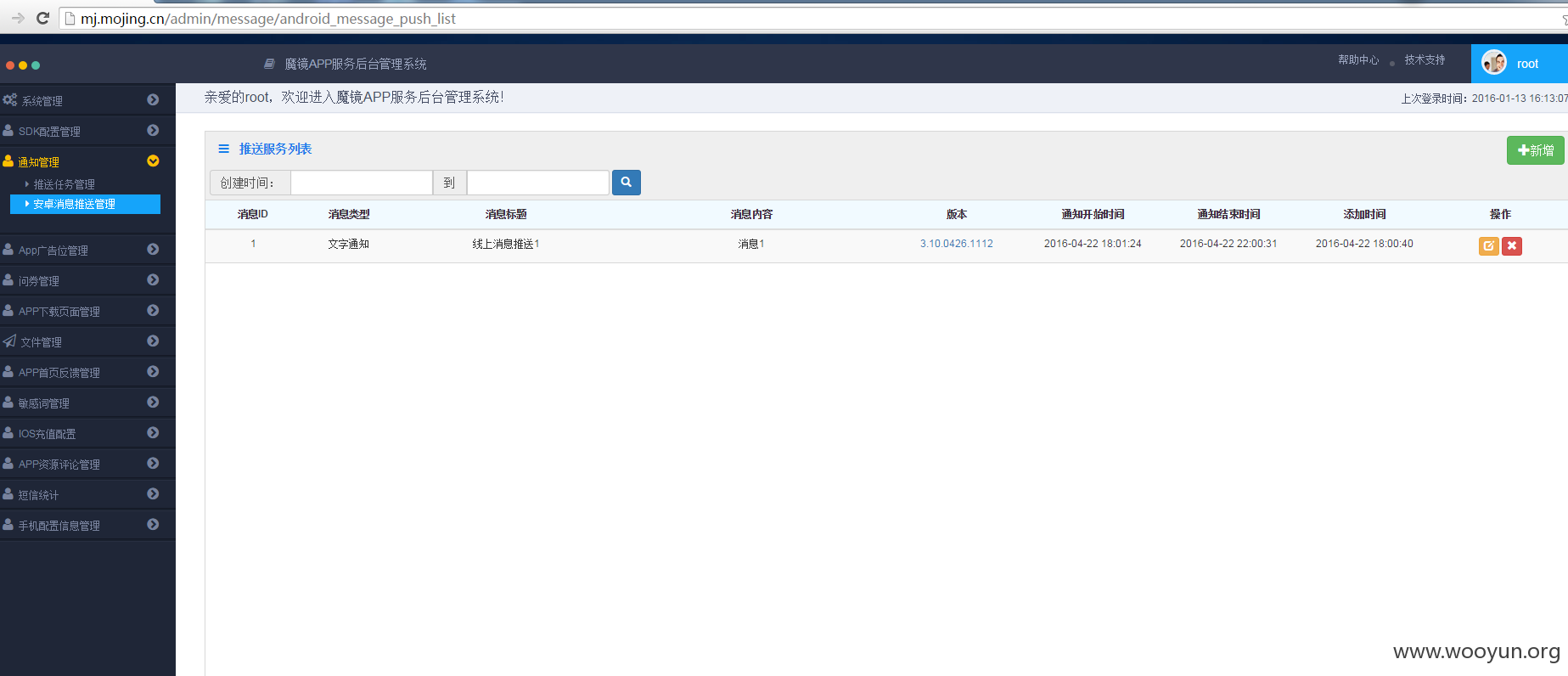
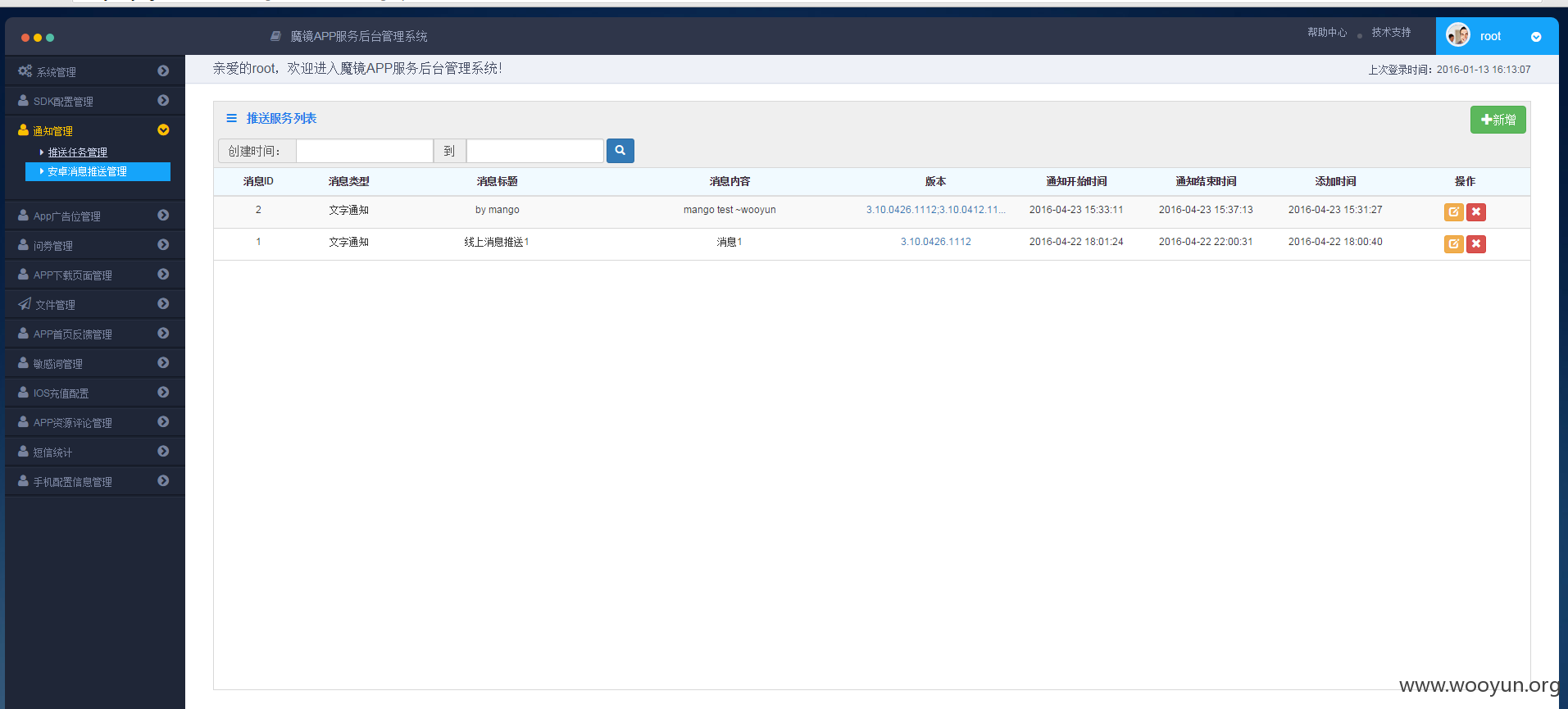
那么modou呢~
其中mojing_user_2 引起我注意 我尝试注入几条数据
![J84K96O56CP5I]NCM1Q%])G.png](http://wimg.zone.ci/upload/201604/2316364392e0f4ab5aab04242f8b95c39d2a937c.png)
看这应该是魔镜APP的用户吧~






![J84K96O56CP5I]NCM1Q%])G.png](http://wimg.zone.ci/upload/201604/2316364392e0f4ab5aab04242f8b95c39d2a937c.png)
![SJ]P$Z[TO9PPZFWH`1$%WOG.png](http://wimg.zone.ci/upload/201604/231607101863447307455fb0ec08c00ce559fc12.png)